Internet Systems Consortium (ISC) officially released a security advisory to announce a vulnerability (CVE-2016-2776) and its fixing. The vulnerability exists in buffer.c. When constructing a response packet for a specially crafted query request, BIND will encounter an assertion failure, causing the program to crash and therefore a denial of service.
More details are available at the following link:
https://kb.isc.org/article/AA-01419
What Is BIND?
Berkeley Internet Name Daemon (BIND) is the most popular DNS service application on the Internet, running on 90% of DNS servers. BIND is developed and maintained by Internet Systems Consortium.
Affected Versions
- BIND 9 version 9.0.x -> 9.8.x
- BIND 9 version 9.9.0 -> 9.9.9-P2
- BIND 9 version 9.9.3-S1 -> 9.9.9-S3
- BIND 9 version 9.10.0 -> 9.10.4-P2
- BIND 9 version 9.11.0a1 -> 9.11.0rc1
Unaffected Versions
- BIND 9 version 9.9.9-P3
- BIND 9 version 9.10.4-P3
- BIND 9 version 9.11.0rc3
Vulnerability Analysis
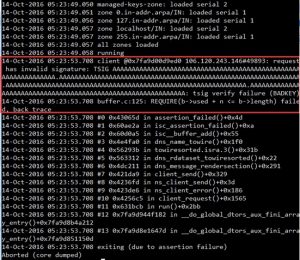
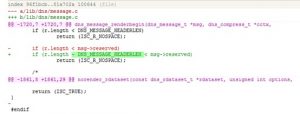
This vulnerability exists because BIND 9 incorrectly calculate the length of reserved space when constructing a response packet. This causes an assertion failure that causes BIND 9 to terminate, and finally leads to a denial of service. This vulnerability resides in the dns_message_renderbegin function, which implements as follows:
In the preceding figure, r.length indicates the length of the DNS response packet, which is fixed to 512 bytes. msg->reserved indicates the response data length that needs to be reserved. When r.length is smaller than msg->reserved, the reserved length is smaller than the needed length for response data, and ISC_R_NOSPACE is returned, indicating insufficient space. When r.length is equal to or larger than msg->reserved, ISC_R_SUCCESS is returned, indicating that there is sufficient space for constructing a response packet.
However, when comparing r.length with msg->reserved, the program does not take DNS_MESSAGE_HEADERLEN into consideration. DNS_MESSAGE_HEADERLEN indicates the message header length, 12 bytes. The length of msg->reserved, when ranging from 501 to 512 bytes, plus DNS_MESSAGE_HEADERLEN, exceeds the fixed response packet length of 512 bytes, causing a subsequent assertion failure and program termination.
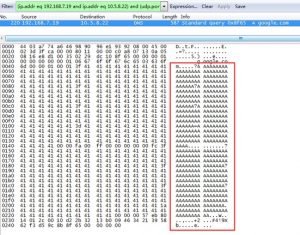
By sending BIND 9 a crafted DNS request with a manipulated Additional RR length, an attacker can make msg->reserved larger than 500, as shown in the following figure:
The following figure shows the assertion failure and termination of BIND 9:
In the remediation code, the length of DNS_MESSAGE_HEADERLEN is taken into consideration, ensuring that r.length is larger than the sum of msg->reserved and DNS_MESSAGE_HEADERLEN. The following shows the vulnerability remediation code.
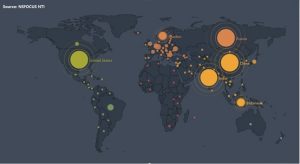
NSFOCUS NTI’s Analysis on the Global Influence of This Vulnerability
- Global Vulnerable Device Distribution
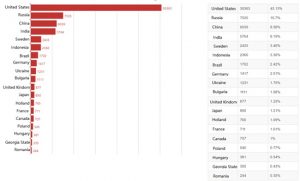
As of today, we have discovered up to 70,392 vulnerable devices around the world.
The United States have the most vulnerable devices (43.13%), followed by Russia (10.7%), China (8.58%), India, Sweden, Indonesia, Brazil, Germany, Ukraine, Bulgaria, and other countries.
83.87% of the vulnerable devices reside in the top 20 countries, and 16.13% of them in other countries.
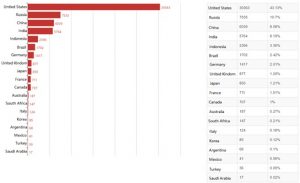
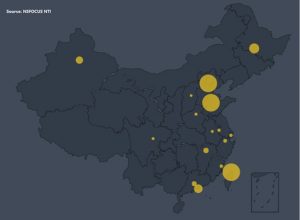
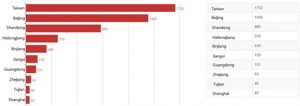
- Vulnerable Device Distribution in China
Up to 6039 devices in China are affected by this vulnerability. Taiwan has the most vulnerable devices (1752), followed by Beijing, Shandong, and other provinces. 84.47% of the vulnerable devices reside in the top 10 provinces, and other 15.53% of them in other provinces.
Recommended Solutions
- The vendor has released a version update. Users are advised to download the update available at the following link to upgrade BIND to the latest version:
- http://www.isc.org/downloads
- Use NSFOCUS’s protection product (IPS, IDS, or NF) to protect against the exploitation of the vulnerability.
- Use NSFOCUS’s remote assessment system (RSAS) to evaluate system security.
- If you have purchased any of the preceding products or services of NSFOCUS, upgrade the product or service for effective protection.
- Use NSFOCUS’s short-term service: NSFOCUS engineers handle the related event onsite to ensure that risk points are immediately eliminated in the network and the event impact is minimized. After the handling, an event analysis report is provided.
- Use NSFOCUS’s mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services to eradicate risks and prevent events from recurring.
- Use NSFOCUS’s long-term service: NSFOCUS provides industry-specific risk mitigation solutions (threat intelligence + attack traceback + professional security service).
Statement
===============
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. Both NSFOCUS and the author shall not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not add, delete, or modify this advisory or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
================
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.