The memory subsystem of the Linux kernel contains a race condition in the way of handling the copy-on-write (COW) breakage of private read-only memory mappings. An unprivileged local user could exploit this vulnerability to gain write access to otherwise read-only memory mappings, thus escalating his or her privileges on the system.
Vulnerability details are available in the following link:
https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Vulnerability Verification
For proofs of concept (PoCs), visit the following link:
https://github.com/dirtycow/dirtycow.github.io/blob/master/dirtyc0w.c
Scope of Impact
This vulnerability exists in Linux kernel 2.6.22 and later, affecting all versions of Linux and fixed on October 18, 2016. The impact on Linux distributions of Red Hat, Debian, and Ubuntu and fixes to this vulnerability can be found in the following links:
- Red Hat: https://access.redhat.com/security/cve/cve-2016-5195
- Debian: https://security-tracker.debian.org/tracker/CVE-2016-5195
- Ubuntu: http://people.canonical.com/~ubuntu-security/cve/2016/CVE-2016-5195.html
Vulnerability Analysis
COW is a mechanism by which a program generates a duplication of a mapping area when writing to this area. Any changes to this area will not be written back to the original file.
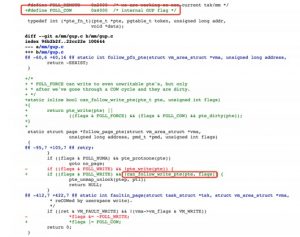
When a virtual memory page in a program is mapped to a read-only file via a read-only private mapping (PROT_READ and VM_PRIVATE), the first write into this page will cause a page fault. When handling this fault, the handle_pte_fault function finds that this page is in fact unwritable despite the FOLL_WRITE flag and a private mapping is used. Then it calls the do_cow_fault and do_wp_page functions to generate a duplicate of the physical page to resolve the page fault. In this way, content written into the duplicate will not affect that of the original file.
After a duplicate of the physical page is generated during the COW, the kernel drops the FOLL_WRITE flag. In this case, if another page fault occurs during a rewrite into this page (another thread keeps calling madvise (MappedMem, Size, and MADV_DONTNEED) to notify the kernel that the current page is no longer in use for the purpose of freeing the physical page), handle_pte_fault, when handling the fault, will not continue the COW process because the FOLL_WRITE flag is missing. Instead, it calls do_read_fault to complete common page fault handling. The content rewritten will be synchronized to the original mapping file, thus breaking the COW process and completing the write into a read-only file.
The author modified the code as follows so that the FOLL_WRITE flag will not be dropped, but a COW process flag (FOLL_COW) will be added after a duplicate of the physical page is generated during the COW process. In addition, a condition is added for canceling page mappings: The dirty bit must be set for COW operations. That is to say, a page mapping can be canceled only after the COW is complete.
Recommended Solutions
- Users who use a Linux distribution mentioned in the previous section can visit the provided links to upgrade their system according to recommendations provided by the related vendor or adopt workarounds as required.
- Users can modify the source code of the Linux kernel by reference to the following link. Recompiling the source code and installing the new Linux kernel will resolve this issue:
- Authorize NSFOCUS RSAS to check services.
- Short-term service: Contact NSFOCUS for onsite handling to ensure that risk points are immediately eliminated in the network and the event impact is minimized. After the handling, an event analysis report is provided.
- Mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services to eradicate risks and prevent events from recurring.
- Long-term service: NSFOCUS provides industry-specific risk mitigation solutions (threat intelligence + attack traceback + professional security service).
Statement
==========
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
============
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.