On March 37, Zhiniang Peng and Chen Wu disclosed the Internet Information Services (IIS) 6.0 WebDAV remote code execution vulnerability, which has been assigned CVE-2017-7269 and CNNVD-201703-1151. This vulnerability, which could cause buffer overflows, is associated with the ScStoragePathFromUrl function in the WebDAV service in IIS 6.0 in Microsoft Windows Server 2003 R2.
Remote attackers could exploit this vulnerability to execute arbitrary code via a long header beginning with “If: <http://” in a PROPFIND request, as exploited in the wild in July or August 2016. A related proof-of-concept (PoC) is available on the Internet.
Related information is available in the following links:
Affected Versions
Microsoft IIS 6.0 in Microsoft Windows Server 2003 R2
Unaffected Versions
Currently, it is verified that other versions are not affected.
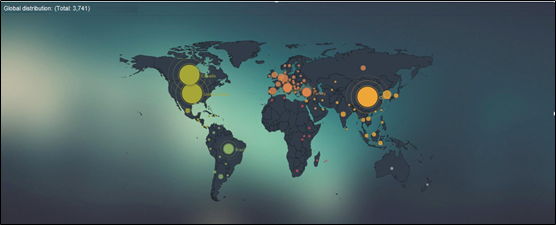
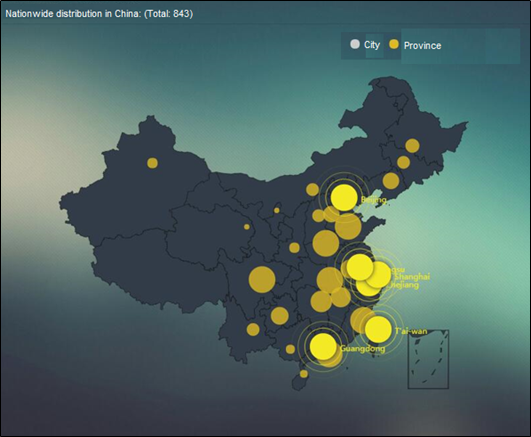
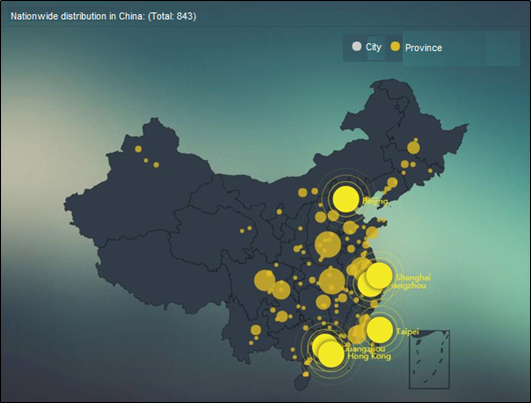
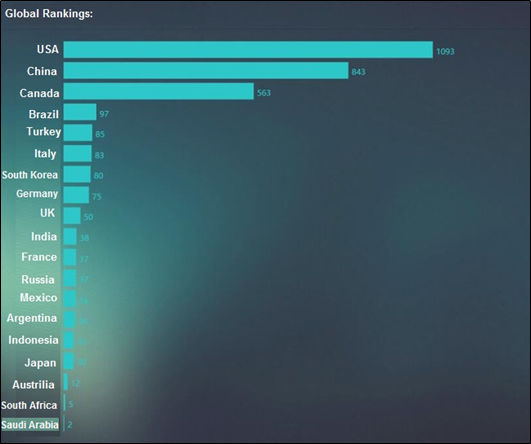
Vulnerability Distribution Released by NSFOCUS Threat Intelligence (NTI)
- Global Distribution
- Provincial Distribution in China
- City Distribution in China
- Global Top 20 Rankings
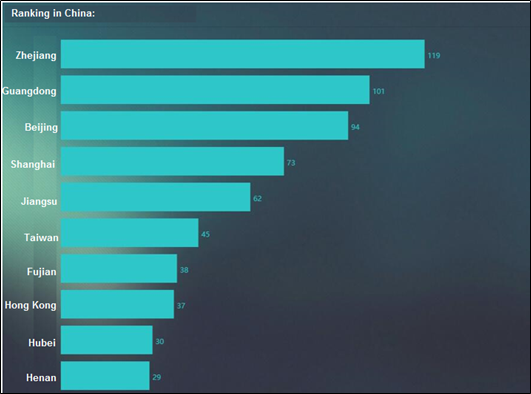
- Rankings in China
Vulnerability Analysis
The ScStoragePathFromUrl function in the WebDAV service in IIS 6.0 in Microsoft Windows Server 2003 R2 is prone to a buffer overflow vulnerability. Remote attackers could exploit this vulnerability to execute arbitrary code via a long header beginning with “If: <http://” in a PROPFIND request.
- Vulnerability Verification
According to the PoC released on GitHub, the vulnerability is reproduced as follows.
Link: https://github.com/edwardz246003/IIS_exploit
First, manually enable the WebDAV service in IIS 6.0, which is disabled by default.
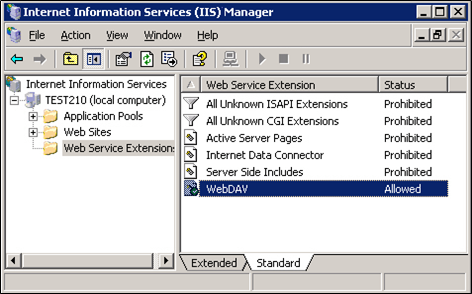
After the WebDAV service is enabled, execute the attack script.
It is found that the calculator process is executed in the IIS 6.0 process in the background. This is because that IIS privileges are inherited and the opened calc.exe belongs to the network service.

- Vulnerability Principle Analysis
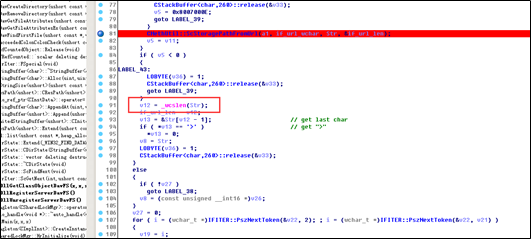
The ScStoragePathFromUrl function in %systemroot%\system32\inetsrv\httpext.dll in the WebDAV module of IIS 6.0 is prone to a buffer overflow vulnerability.
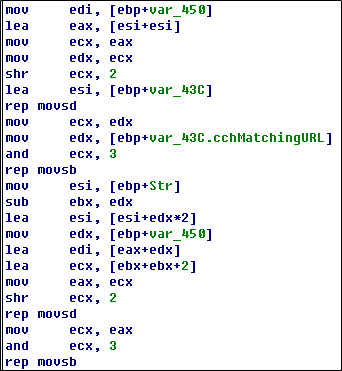
When receiving a PROPFIND request with a long header starting with “If: <http://”, the ScStoragePathFromUrl function copies the overly long character string to the stack without properly validating the length. When IIS processes the PROPFIND request CPropFindRequest->Execute, it does not check the length of the imported URL when using HrCheckIfHeader to process the “If” header and ScStoragePathFromUrl to translate the URL address into a local address. This causes an overly long URL, leading to a stack overflow.
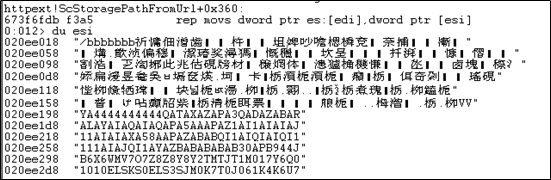
In HrCheckIfHeader, ScCanonicalizePrefixedURL(if_url, if_url_wchar, &if_url_len); translates “If: <http://localhost/aaaaaaaaaaa” in if_url into a wide byte (I\x00f\x00:\x00 <\x00h\x00t\x00t\x00p\x00:\x00/\x00/\x00l\x00o\x00c\x00a\x00l\x00h\x00o\x00s\x00t\x00/\x00a\x00a\x00a\x00a\x00a\x00a\x00) and saves it in if_url_wchar.
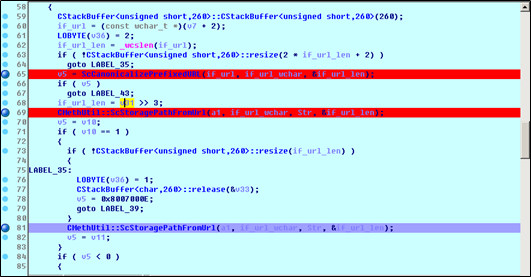
The first call only releases an element. It is the second call that triggers the vulnerability.
For the second time, CMethUtil::ScStoragePathFromUrl(a1, if_url_wchar, Str, &if_url_len); is called to translate the network address saved in the if_url_wchar variable into a corresponding address in the local file system, such as c:\inetpub\wwwroot\aaaaaaaaaa.
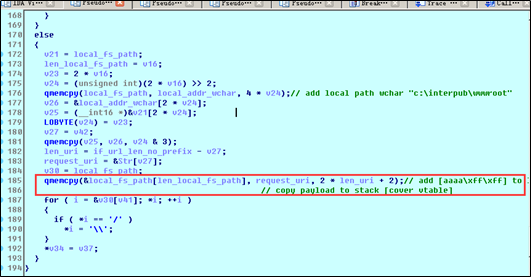
When the function translates http://localhost/aaaaa into c:\inetpub\wwwroot\aaaaaaaaaa, it first copies the local path to the stack and splices characters in the requested URI (namely, the local address before aaaaa). There is no length restriction. Therefore, the URI is so long that it triggers a stack overflow when being spliced, overwriting other elements in the stack and leading to a stack overflow.
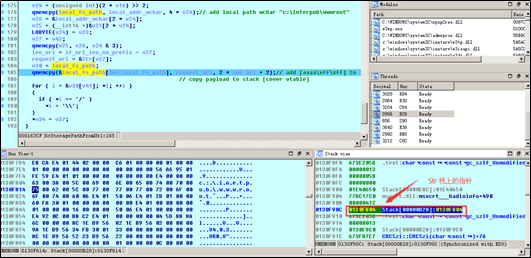
The following figure shows the situation where the local path is copied.
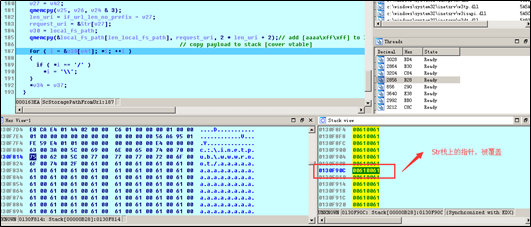
The “Str” pointer in the stack is overwritten by \x00\x61\x00\x61.
Therefore, an out-of-bounds memory read occurs during the calculation of the character string length.
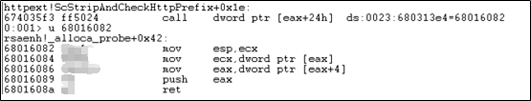
Triggering the vulnerability for several times rewrites the virtual function of the IEcb object, hijacks the control flow, takes the control, and executes return-oriented programming (ROP).
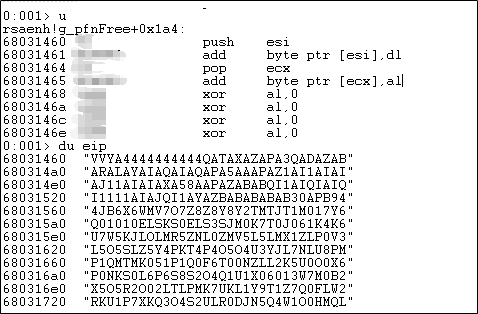
Use gadgets built in the rsaenh.dll module to execute ROP and finally execute shellcodes.
A shellcode is the encoded character string.
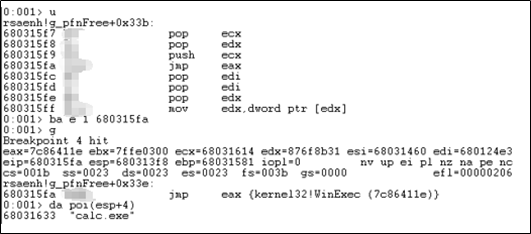
After the character string is decoded, the WinExec function is called. Then the calculator window pops out.
Official Solution
Microsoft has stopped providing supports for Windows Server 2003 since July 15, 2017. Therefore, there is no solution available for Windows Server 2003. Users are advised to upgrade to Windows Server 2016.
Windows Server 2016 can be downloaded from the following link: https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-2016.
Workaround
- Disable the WebDAV server under IIS.
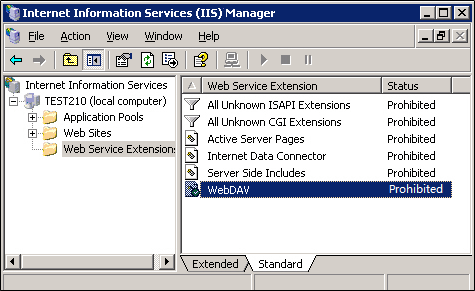
- If directly disabling the WebDAV service has impact on your business, employ flexible means, such as disabling the PROPFIND method, by performing the following steps:
- Install the IIS security tool UrlScan.
The default installation of UrlScan disables the WebDAV function.
UrlScan can be downloaded from the following link: https://technet.microsoft.com/en-us/security/cc242650.aspx. - Configure the UrlScan.ini file to make UrlScan reject HTTP requests based on the request method.
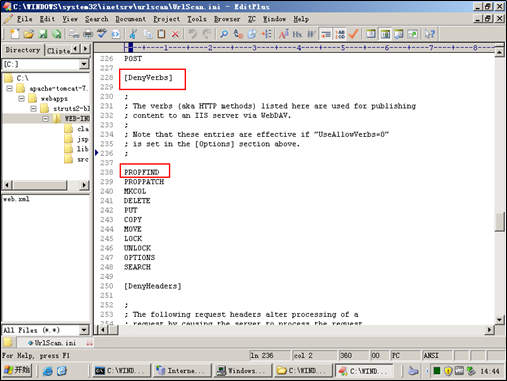
- Install the IIS security tool UrlScan.
In the configuration of the [DenyVerbs] node shown in the following figure, requests with all the listed methods will be rejected.
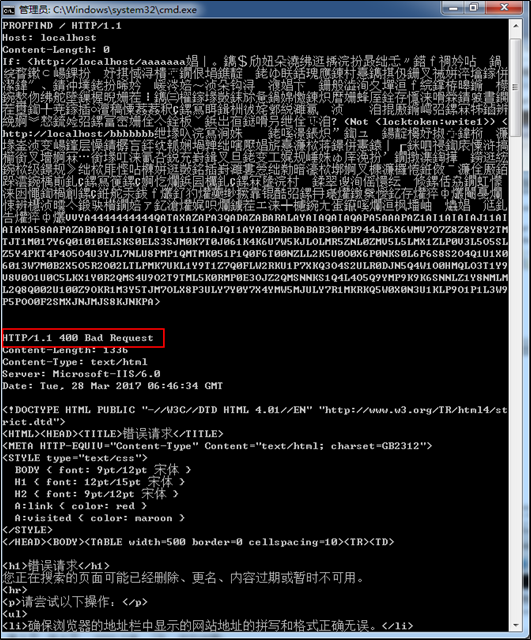
After configuration, use the PoC to launch an attack against the host again to see the defense effect.
The attack is successfully blocked.
Technical Solutions
- If you are not sure whether your whether the system you are using is affected by this vulnerability, do as follows:
- For Internet-facing assets, use the emergency vulnerability detection service of NSFOCUS Cloud to check for the vulnerability online. The service is available at the following link:
https://cloud.nsfocus.com/#/krosa/views/initcdr/productandservice?page_id=12
- For internal assets, use NSFOCUS RSAS V5 or V5 or WVSS to check the vulnerability.
Remote Security Assessment System (RSAS V5):
http://update.nsfocus.com/update/listAurora/v/5
Remote Security Assessment System (RSAS V6):
http://update.nsfocus.com/update/listRsasDetail/v/vulweb
Web Vulnerability Scanning System (WVSS):
http://update.nsfocus.com/update/listWvss
You should upgrade your devices to the latest version by downloading upgrade packages from the preceding links before using them to detect vulnerabilities.
- Use NSFOCUS’s protection product (NIPS, NIDS, NF, or WAF) to protect against the exploitation of the vulnerability:
Network Intrusion Prevention System (NIPS):
http://update.nsfocus.com/update/listIps
Network Intrusion Detection System (NIDS):
http://update.nsfocus.com/update/listIds
Next-Generation Firewall (NF):
http://update.nsfocus.com/update/listNf
NSFOCUS Web Application Firewall (WAF)
Since the buffer overflow vulnerability is triggered by an overly long HTTP header, you can enable the default HTTP protocol validation policy on WAF by setting Max HTTP Header Value.
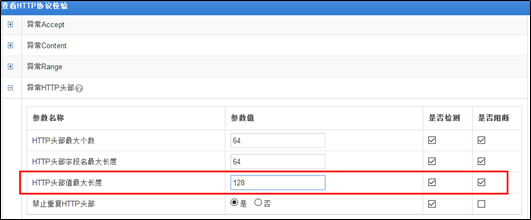
To prevent false positives, you can duplicate the default policy and then set Max HTTP Header Value to a value no greater than 1300 bytes.
From the previous links, you can upgrade WAF by installing the latest rule package for protection or perform custom protection as required.
Services:
NSFOCUS provides professional security techniques and services, protecting customers’ application systems in an all-round manner from the possible impact of this vulnerability.
- Short-term service: This type of service is provided in case of emergency, covering remediation suggestions specific to customers’ application systems and assurance of a secure upgrade.
- Medium- to long-term service: Revolving around its detection and protection products, NSFOCUS offers security operations services 24/7, including notifying customers immediately after learning a security threat to their application systems, conducting regular security checks, and delivering professional solutions to mitigate specific security risks.
Statement
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete any information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.
