On the evening of June 27, 2017, multiple enterprises were attacked by ransomware, hence service interruption was caused. The first infections were identified in Ukraine. Since then, it has spread to many countries, including Brazil, Germany, Russia, and the US. This event had such an extensive and significant impact that technical support personnel of NSFOCUS paid close attention to it, and captured and analyzed the sample immediately.
Date of Release: June 28, 2017
- Overview
On the evening of June 27, 2017, multiple enterprises were attacked by ransomware, hence service interruption was caused. The first infections were identified in Ukraine. Since then, it has spread to many countries, including Brazil, Germany, Russia, and the US. This event had such an extensive and significant impact that technical support personnel of NSFOCUS paid close attention to it, and captured and analyzed the sample immediately.
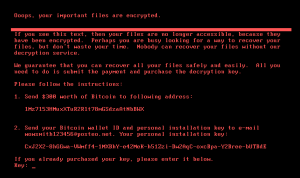
According to our analysis, the sample is an upgraded version of the Petya ransomware using different keys for encrypting the Master Boot Record (MBR). It also adopted APIs provided by Microsoft and used AES-128 to encrypt files of the specified format on the disk. The ransomware displayed a message after the encryption and system restart were complete.
2. Propagation and Infection
The first sample possibly originated from an email phishing virus and then used the EternalBlue exploit once used by WannaCry for further propagation. In addition, to increase the possibility of infecting PCs, the sample leveraged Microsoft tools for lateral penetration. The following figure shows the countries and regions infected by this sample. So far, Ukraine was the worst affected region.

Figure 2 Infection distribution of the sample
3. Sample Analysis
3.1 File Structure
| File Name | MD5 | Function |
| Source sample | 71b6a493388**********ce903bc6b04 | Ransomware in .dll format |
The sample utilized the EternalBlue vulnerability to propagate the .dll modular file, which has the ransomware function. Unlike common ransomware, the Petya ransom not only encrypts files of the specified format and modifies content in the MBR. In this way, after the PC is restarted, a forged disk check interface appears, asking the users to wait for the file encryption to complete. After the encryption is complete, a ransom message was displayed.

Figure 3 Forged disk check interface
Before MBR encryption and network propagation, the sample determines whether to execute related behaviors based on the hash value. Therefore, some PCs may not have such behaviors as MBR encryption or network connections.
The following figure shows the sample execution process.

Figure 4 Sample execution process
The content in the MBR was modified as follows:
The sample uses the XOR method to encrypt the MBR and writes the correct MBR into the 0x22 partition and modifies content in the 0x00–0x21 partitions.
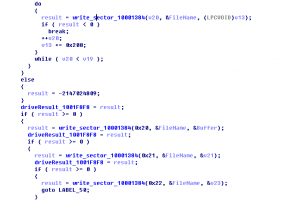
Figure 5 Writing content into the MBR repeatedly
The encryption analysis is as follows:
The sample uses the AES encryption function provided by Microsoft for encryption. Then it uses the built-in RSA public key to encrypt the AES key. The encrypted AES key is displayed in the notification, which can be sent to the victims for data restoration.

Figure 6 AES encryption
This file can encrypt files of the specified formats.

Figure 7 Encrypting files of the specified formats

Figure 8 Using the built-in RSA public key to encrypt the AES key
The propagation analysis is as follows:
The sample exploits the lateral penetration for propagation in the intranet environment and the Windows Management Instrumentation Command-line (WMIC) for command execution.

Figure 9 Using wmic.exe for command execution
The sample scans port 445 and exploits the MS17-010 vulnerability for further propagation.

Figure 10 Scanning port 445 for vulnerability exploit
The clearance analysis is as follows:
After encryption is complete, the sample clears logs and MFT tables, preventing the user from restoring data by using a restoration tool.
![]()
Figure 11 Clearing logs and MFT tables
4. Detection Method
4.1 Detection and Prevention
Users are advised to update the system and install patches.
Statement
==========
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete any information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
============
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.
