The banking trojan “Shifu” was discovered by the IBM counter fraud platform in April, 2015. Built based on the Shiz source code, this trojan employs techniques adopted by multiple notorious trojans such as Zeus, Gozi, and Dridex.
Overview
The banking trojan “Shifu” was discovered by the IBM counter fraud platform in April, 2015. Built based on the Shiz source code, this trojan employs techniques adopted by multiple notorious trojans such as Zeus, Gozi, and Dridex. This kind of trojan once mainly targeted 14 banks in Japan and has emerged in Britain since September 22, 2015, attacking at least more than 10 banks. On January 6, 2017, researchcenter.paloaltonetworks.com issued an article, indicating that the author of this trojan refined it in 2016. Specifically, this trojan, at its early stage, obtained system privileges of the attacked host by exploiting the vulnerability assigned CVE-2015-0003, but now achieves this purpose by leveraging the Windows privilege escalation vulnerability assigned CVE-2016-0167.
The sample analyzed in this document is a variant of the “Shifu” trojan. With privileges escalated to the system level by using the embedded system vulnerability exploitation module, this trojan steals users’ login credentials of the online banking business to cause damage.
The following figure shows the timeline of attacks launched via this trojan.

CVE-2016-0167
Microsoft Windows is a series of operating systems developed by Microsoft. win32k.sys is a kernel-mode device driver and is the kernel part of the Windows subsystem. It contains the window manager which controls window displays, as well as manages screen output.
The kernel-mode device driver contains a privilege escalation vulnerability because it does not properly handle objects in memory. An attacker could exploit this vulnerability to escalate his/her privileges and execute arbitrary code.
The following systems are affected:
- Microsoft Windows Vista SP2
- Windows Server 2008 SP2 and R2 SP1
- Windows 7 SP1
- Windows1
- Windows Server 2012 Gold and R2
- Windows RT 8.1
- Windows 10 Gold and 1511
Propagation and Infection
Sample Analysis
- Environment
| System | Windows 7 (32-bit) |
| Tools | ProcessMonitor, Xuetr, Wireshark, OllyDbg, IDA |
- Detection Results of TAC

The following table lists other same-origin samples:
| MD5 | File Size | Risk Level |
| f25528baf3d68444fa7d7fda382e9835 | 338948 | High |
| ebf3e72f8b698bbb0d026416d7a75a6a | 338948 | Medium |
| e98459c647a6e328c8b65945884ef29a | 338948 | Medium |

[1] Covert attack: Attacks are completed through multiple encryptions and process injections.
[2] Network behavior: The sample collects information (including but not limited to the local time zone, current time, operating system version, antivirus software version, and host name) about local hosts, uploads it to the remote server, and keeps communicating with the remote server to control the user and steal its information.
[3] Sandbox detection: The sample provides anti-debugging and anti-virtual machine (VM) functions. That is, the sample checks whether it is likely to be in the sandbox by comparing file names, process names, user names, and system signatures.
[4] Confrontation with antivirus tools: The sample can detect multiple analysis tools, antivirus software, and sandboxes. When antivirus software is found, this sample enters a sleep infinite loop, exhibiting no malicious behaviors. When a sandbox is detected, this sample terminates the script interpreter, traffic capture tool, binary analysis tool, and other processes, cutting off the interaction between the sandbox and the outside or preventing the sandbox’s automated analysis of this sample.
[5] Persistent attack: This sample, via concealing and self-starting, implements persistent attacks against target hosts, by taking the following actions: injecting svchost.exe for concealing processes and creating JavaScript scripts in the Startup folder on the Start menu for completing self-starting.
The following figure shows the sample execution process.
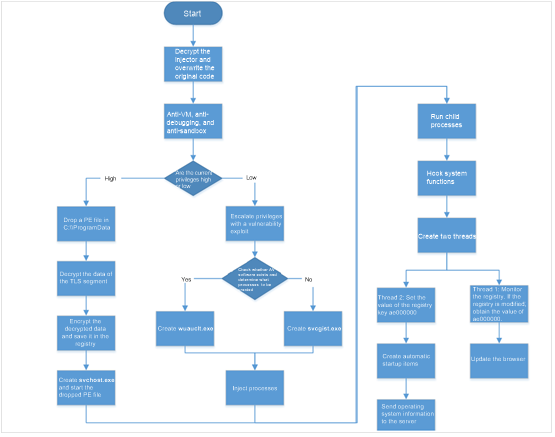
Functions of this sample are as follows:
- Decrypting the injector to overwrite the original code.
Code for decrypting the PE file is as follows:

Code for the decryption algorithm is as follows:
002C0564 3B75 64 cmp esi,dword ptr ss:[ebp+0x64] 002C0567 75 0D jnz short 002C0576 002C0569 0375 68 add esi,dword ptr ss:[ebp+0x68] 002C056C 037D 68 add edi,dword ptr ss:[ebp+0x68] 002C056F 2B4D 68 sub ecx,dword ptr ss:[ebp+0x68] 002C0572 85C9 test ecx,ecx 002C0574 74 12 je short 002C0588 002C0576 AD lods dword ptr ds:[esi] 002C0577 50 push eax 002C0578 2D BB462156 sub eax,0x562146BB 002C057D 90 nop 002C057E 90 nop 002C057F 33C2 xor eax,edx 002C0581 5A pop edx 002C0582 AB stos dword ptr es:[edi] 002C0583 83E9 03 sub ecx,0x3 002C0586 ^ E2 DC loopd short 002C0564
The memory attribute at 0x400000 is changed to writable.
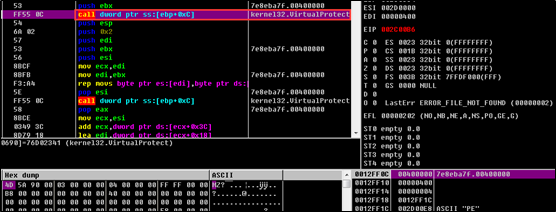
The content at 0x400000 is replaced (the address space of the original sample is overwritten and essentially replaced by the injection module).
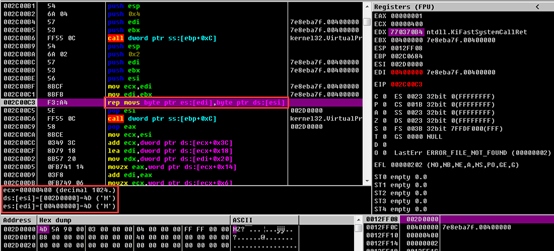
The function address is changed in IAT:
- Anti-VM, anti-debugging, and sandbox detection
- Anti-VM
The sample identifies parameters contained in the command line.
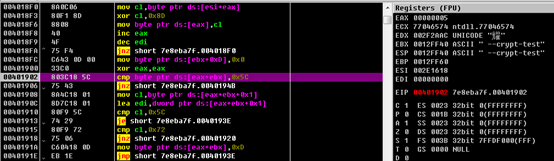
Then this sample searches the process list for target processes, encrypts the names of obtained processes with CRC32, and invokes the RtlComputeCrc32 function.
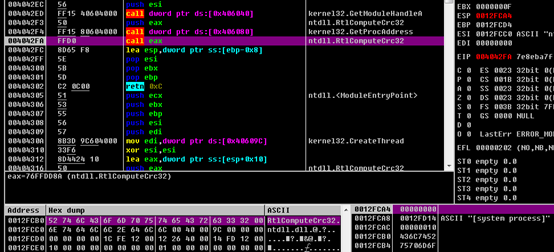
The sample checks whether such process names indicate specific processes such as vmtoolsd.exe, and then compares these names with hard code that is obtained after specific process names are encrypted with CRC32.
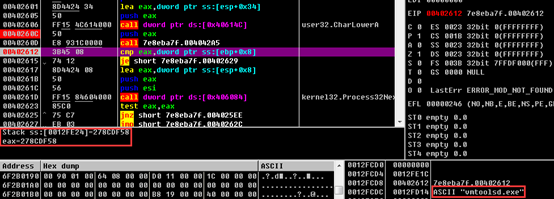
……
Attack Location
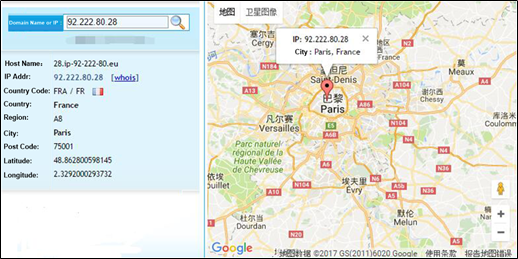
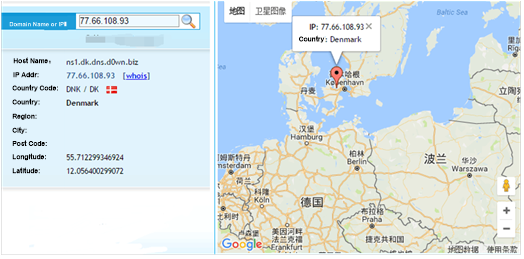
The sample queries the region where each of three DNS servers (92.222.80.28, 78.138.97.93, and 77.66.108.93) used by the actual C&C server is located.

Recommended Solution
- NSFOCUS Detection Services
- NSFOCUS engineers provide onsite detection services.
- NSFOCUS provides online cloud detection services. You can visit the following link to apply for the trial use of NSFOCUS Threat Analysis Center (TAC): https://cloud.nsfocus.com/#/krosa/views/initcdr/productandservice?service_id=1018
- NSFOCUS Solutions for Removing Trojans
- Short-term service: NSFOCUS engineers provide the onsite trojan backdoor removal service (manual services + NIPS + TAC + Kingsoft V8+ terminal security system) to ensure that risk points are immediately eliminated in the network and the event impact is minimized. After the handling, an event analysis report is provided.
- Mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services (NIPS + TAC + manual services) to eradicate risks and prevent events from recurring.
- Long-term service: NSFOCUS provides industry-specific risk mitigation solutions (threat intelligence + attack traceback + professional security service).
Conclusion
After using the embedded local system vulnerability exploitation module to escalate its privileges, this sample, with system-level privileges, steals user login credentials of the online banking business to cause harm.
As this sample provides various anti-debugging and analysis and detection means, common antivirus software regards it secure and passes it through. Also, it is able to escape common sandbox detection. Therefore, this sample is dangerous to users.
Using .bit domain names for network communication, this sample is more covert and anonymous, making it difficult to track.
Appendix
The encrypted data in the original file of the sample is decrypted with the key 0x8D as follows:
AddMandatoryAce
ADVAPI
Advapi32.dll
advapi32.dll
ws2_32.dll
WPUCloseEventW
PUCloseSocketHandle
WPUCreateEvent
WPUCreateSocketHandle
WPUFDIsSet
WPUGetProviderPath
WPUModifyIFSHandle
WPUPostMessage
WPUQueryBlockingCallback
WPUQuerySocketHandleContext
WPUQueueApc
WPUResetEvent
WPUSetEvent
WPUOpenCurrentThread
WPUCloseThread
WSPStartup
> %1\r\ndel %0
software\\microsoft\\windows\\currentversion\\run
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/echo
rundll32.exe shell32.dll, ShellExec_RunDLL %s
Microsoft\\Microsoft AntimalwareSoftware\\Coranti
Software\\risingSoftware\\TrendMicroSoftware\\Symantec
Software\\ComodoGroup
Software\\Network Associates\\TVD
Software\\Data Fellows\\F-SecureSoftware\\Eset\\Nod
Software\\Softed\\ViGUARD
Software\\Zone Labs\\ZoneAlarm
Software\\Avg
Software\\VBA32
Software\\Doctor Web
Software\\G Data
Software\\Avira
Software\\AVAST
Software\\Avast
Software\\KasperskyLab\\protectedSoftware\\BitdefenderSoftware\\Panda
SoftwareSoftware\\Sophos.bat\\\\.\\%C:
|$$$}rstuvwxyz{$$$$$$$>?@ABCDEFGHIJKLMNOPQRSTUVW$$$$$$XYZ[\\]^_`abcdefghijklmnopq
conhost
CreateProcessInternalW
ConvertStringSecurityDescriptorToSecurityDescriptorW
Content-Type: multipart/form-data; boundary=---------------------------%s\r\n
Content-Type: application/x-www-form-urlencoded\r\n
Host: %s\r\n%d.%d.%d.%d
%d.%d.%d.%d.%x
%temp%\\debug_file.txt
[%u][%s:%s:%u][0x%x;0x%x]%sDnsFlushResolverCache
\\*.*
dnsapi.dll
DnsGetCacheDataTable.dll.exe
download.windowsupdate.com
vk.com
yandex.ru
HTTP/1.1
https://http://%s
IsWow64Process
kernel
kernel32.dll
LdrGetProcedureAddress
Microsoft
NtAllocateVirtualMemory
CLOSED
LAST_ACKTIME_WAIT
DELETE_TCB
LISTEN
SYN_SENTSYN_RCVDESTAB
FIN_WAIT1
FIN_WAIT2
CLOSE_WAIT
CLOSING
TCP\t%s:%d\t%s:%d\t%s\n
netstat\nProto\tLocal address\tRemote address\tState\n
ntdll.dll
NtResumeProcess
NtSuspendProcess
\\\\?\\globalroot\\systemroot\\system32\\drivers\\null.sys
NtWriteVirtualMemory
openRegisterApplicationRestart
RtlCreateUserThread
ResetSR
RtlComputeCrc32
rundll32
SeDebugPrivilege
SystemDrive\\StringFileInfo\\%04x%04x\\ProductName
software\\microsoft\\windows nt\\currentversion\\winlogon
shell
Sleep
srclient.dll
SeShutdownPrivilege
\"%s\"
%d\t%s\ntaskmgr\nPID\tProcess name\nnet user\n
the computer is joined to a domain\n..
\\VarFileInfo\\Translation
GET%windir%\\system32\\%windir%\\syswow64\\POST*.exe
Low
%SystemDrive%
\\*SYSTEM*%02x%s:Zone.
Identifier
GetProcessUserModeExceptionPolicy
etProcessUserModeExceptionPolicy
%ws\\%ws\n%x
WORKGROUP
HOME
Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\ExplorerDisableCurrentUser
Run%s.datsoftware\\microsoft\\windows
%OS%_%NUMBER_OF_PROCESSORS%S
S:(ML;;NRNWNX;;;LW)D:(A;;GA;;;WD)
S:(ML;;NRNWNX;;;LW)D:(A;;GA;;;WD)(A;;GA;;;AC)
\\\\.\\AVGIDSShim
FFD3\\\\.\\NPF_NdisWanIpc:\\sample\\pos.exe
ANALYSERS
SANDBOX
VIRUS
MALWARE
FORTINET
MALNETVM
c:\\analysis\\sandboxstarter.exe
c:\\analysis
c:\\insidetm
c:\\windows\\system32\\drivers\\vmmouse.sys
c:\\windows\\system32\\drivers\\vmhgfs.sys
c:\\windows\\system32\\drivers\\vboxmouse.sys
c:\\iDEFENSE
c:\\popupkiller.exe
c:\\tools\\execute.exe
c:\\Perl
c:\\Python27
api_log.dll
dir_watch.dll
pstorec.dll
dbghelp.dll
Process32NextW
Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Zones\\31406.bit
MiniDumpWriteDump\r\nReferer: %s\r\n
\\Google\\Chrome\\User Data\\Default\\Cachevar
%s = new ActiveXObject("WScript.Shell"); %s.Run("%s");
IntelPowerAgent32
%OS%_%NUMBER_OF_PROCESSORS%
%s\cmd.exe
ComSpecConsoleWindowClass.exe
kernel32.dll
ntdll.dll
ZwQuerySystemInformation
ZwAllocateVirtualMemory
PsLookupProcessByProcessId
PsReferencePrimaryTokenClassWindow
open "%s" -q%windir%\\system32\\sdbinst.exe
/c "start "" "%s" -d"
%windir%\\system32\\sndvol.exe
"%s" -u /c "%s\\SysWOW64\\SysSndVol.exe /c "start "" "%s" -d"
"%temp%\\%u
%u.tmp
Wow64DisableWow64FsRedirection
Wow64RevertWow64FsRedirection
runas.exe
%systemroot%\\system32\\svchost.exe
%systemroot%\\system32\\wscript.exe
snxhk.dll
sbiedll.dll
/c start "" "%s" " "
cmd.exe
runas
--crypt-test:3
It work's!
--vm-test
Full text download please click: Shifu Banking Trojan Technical Analysis and Protection Solution
About NSFOCUS
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.
