ISC BIND 9 Denial-of-Service Technical Analysis and Solution
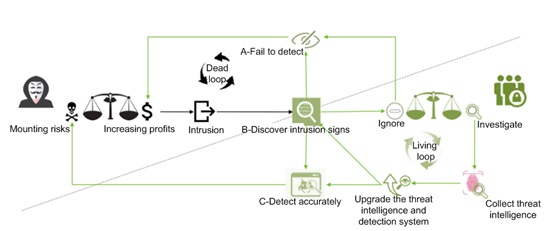
Internet Systems Consortium (ISC) officially released a security advisory to announce a vulnerability (CVE-2016-2776) and its fixing. The vulnerability exists in buffer.c. When constructing a response packet for a specially crafted query request, BIND will encounter an assertion failure, causing the program to crash and therefore a denial of service.