With the robust development of the Internet of Things (IoT), more and more security issues are found with IoT devices. These imminent threats, especially those from network video surveillance systems (NVSSs) that account for a large majority of IoT devices, have drawn attention from security professionals from home and abroad. (In this paper, network video monitors (NVMs), web cameras, and digital video recorders (DVRs) are all referred to as NVSSs.)
Recently, one after another massive distributed denial of service (DDoS) attack has been reported in countries outside of China by using a slew of NVSSs compromised by hacker organizations. In October 2015, Incapsula discovered a DDoS attack originated by 900 web cameras on its network, with the maximum rate of 20,000 HTTP requests per second (RPS). In June 2016, Sucuri found a DDoS attack targeting its clients, with the maximum rate reaching 50,000 HTTP RPS and traffic peaking at 400 Gbps. This attack was executed by a botnet composed of 25,513 independent web cameras.
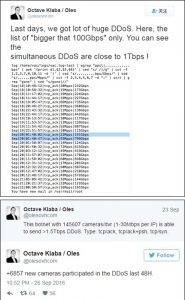
On September 19, Octave Klaba, chief technology officer (CTO) of OVH, claimed on Twitter that the company was suffering a DDoS attack from a botnet of 145,607 NVSSs, with peak traffic of 800 Gbps. It was predicted that this botnet was capable of launching DDoS attacks of up to 1.5 Tbps. On September 20, KrebsonSecurity, a website engaged in exposure of cybercrimes, was subjected to a DDoS attack, whose peak traffic stood at 620 Gbps[1]. Klaba speculated that attacks targeting Krebs and OVH were launched from the same Mirai botnet[2]. According to the related analysis, a large proportion of bots seen in the Mirai botnet were NVSSs from a Chinese company.
In fact, security issues associated with NVSSs in China are equally challenging. According to A 2015 Survey of Internet Security Situation in China[3], “In 2015, CNVD announced a series of security events concerning various intelligent monitoring devices and routers that are prone to high-risk vulnerabilities and may therefore be remotely manipulated. In early 2015, a certain model of monitoring devices widely used by government agencies and the public sector was reported to contain a high-risk vulnerability, which had been exploited to plant malicious code, causing some devices to be remotely manipulated to launch cyberattacks toward external targets. CNCERT, through investigation, has found that the same type of devices from major Chinese vendors has the same security issue, which needs to be immediately addressed across the country.” A recent research report from a foreign institution shows that Mirai, as a piece of IoT-targeting malware, has begun to exploit video surveillance devices connected to the Internet for launch of large-scale DDoS attacks. Unfortunately, devices being exploited to do so include those from two vendors in China.
Today, volumetric DDoS attacks with peak traffic of a few hundred Gbps are not a rare sight. What shocks people is that an attack launched from a botnet made up of numerous NVSSs can easily generate traffic up to nearly 1 Tbps without help of any reflection/amplification protocols, and, if targeting the application layer, the attack can send millions of queries per second (QPS) or more. Such a devastating impact is not only horrifying but also thought-provoking: How come video surveillance systems used in conventional security areas are reduced to weapons of hackers to leak privacy of users and end up bots to launch massive DDoS attacks, paralyzing target networks?
With the popularization of security monitoring devices in various social sectors as well as in-depth convergence of traditional security sectors with the Internet, NVSSs will pose a great challenge to global cybersecurity if no measures are taken to address their security issues, considering the exponential growth of botnets based on NVSSs.
2 Worldwide and Nationwide Distribution of NVSSs with Security Hazards
2.1 Worldwide Distribution of NVSSs with Security Hazards
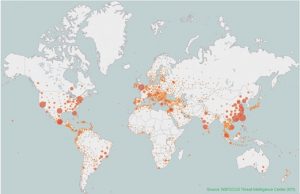
As of the end of September, the number of NVSSs with security hazards had exceeded 2,500,000 around the world. According to our analysis, many of these devices have been infected with the malware Mirai, which has been extremely active recently, and the number keeps increasing. We will continue observing the trend of infections by Mirai.
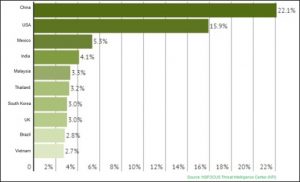
China has the largest proportion of NVSSs with security hazards, accounting for 21.4% of the global total, followed by the USA, which has 15.9% of such devices. Other countries making it into the top 10 list are Mexico, India, Malaysia, Thailand, South Korea, UK, Brazil, and Vietnam.
Vulnerable NVSSs in top 10 countries account for 65.3% of the global total. The remaining 34.7% are distributed in the other 204 countries and regions.
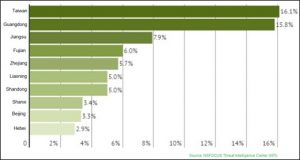
2.2 Distribution of NVSSs with Security Hazards in China
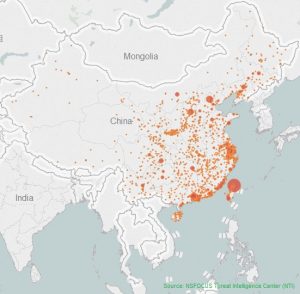
The number of vulnerable NVSSs across China totals 554,174. Among all provinces and regions, Taiwan has the largest number of such systems, accounting for 16.1%, followed by Guangdong, Fujian, and Zhejiang.
Vulnerable NVSSs in top 10 provinces account for 71.2% of the country’s total. The remaining 28.8% are distributed in the other 17 countries and regions. Evidently, most NVSSs with security hazards are seen in economically developed regions, namely, coastal provinces in the southeastern part of China, which is commensurate with the market distribution of NVSSs.
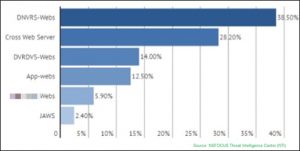
2.3 Signature Analysis
According to our statistics and analysis, responses returned by NVSSs with security hazards usually carry some common HTTP headers. Currently, the most frequently seen HTTP header is DNVRS-Webs, accounting for 38.5% of the total, followed by Cross Web Server (28.2%), DVRDVS-Webs (14%), App-Webs (12.5%), xx (vendor name)-Webs (5.9%), and JAWS (2.4%).
3 High-Risk Vulnerabilities in NVSSs
NVSSs distributed across the world in large quantities generally have various security issues such as weak passwords, system backdoors, and remote code execution (RCE) vulnerabilities. Such devices are usually not subject to proper management. Some users are not sensitive to security issues and sometimes devices fail to be upgraded in a long time or firmware upgrade packages are released at longer intervals than reasonable. As a result, vulnerabilities in these devices cannot be fixed in time. In addition, most devices, for which no protection is applied, are directly exposed to the Internet. Worse still, malicious botnet programs targeting these systems keep emerging, always with new means of propagation. It is only a matter of time before these fully open or semi-open NVSSs end up hacker-controlled bots.
4 NVSS-based Botnets
Our analysis finds that a large number of NVSSs have been infected with some kind of malware, such as notorious LizardStresser, Mirai that has gained a bad reputation in the wake of several massive DDoS attacks, and the emerging malware LuaBot. These infected devices are controlled by various hacker organizations for the implementation of hacking activities like scanning and DDoS attacks.
The following sections analyze the three typical botnets, namely, LizardStresser, Mirai, and LuaBot, and the related malware samples.
5 Root Cause Analysis and Security Measures
5.1 Root Cause Analysis
Owing to the prevalence of high-risk vulnerabilities, hackers can gain control over numerous NVSSs with ease. They can obtain surveillance video of the devices under control and pry into or expose users’ privacy. Some of them, by gaining shell access on these devices, use botnet tools to upload malicious code and maintain backdoors so as to develop their own botnets. Subsequently they will control attack behaviors of these bots through the C&C server.
According to our statistics, the number of NVSSs with security hazards had exceeded 2,500,000 around the world as of the date when this report was released. Some device vendors and users are not highly aware of cybersecurity. As a result, these vulnerable devices will not be upgraded anytime soon. That is to say, these devices with security hazards are exposed to the Internet without any protection, at the risk of being infected and becoming part of the gigantic IoT botnet.
It is predictable that the quantity of botnets based on NVSSs will experience an explosive growth. With the increasing need for security protection in the global landscape, this figure will be worryingly larger.
Both objective and subjective factors contribute to the current security status of NVSSs.
Objectively, the worrying security status of NVSSs is due to historical evolution and deployment characteristics of these systems, as described below:
- NVSSs have evolved from industrial monitoring systems. In times when the Internet was accessible to only a limited number of people, monitoring devices were deployed on production networks or private networks and their security was nothing to worry about.
- With the development of the Internet and IoT and the emergence of individual and non-industrial security needs, NVSS came into being. At first, what mattered for vendors was how to improve user experience and ensure transmission stability. Moreover, these devices generally used small Linux systems, either tailored or embedded, running on common platforms including ARM, ARM7, MIPS, and x86. Additional resources were hardly possible to be allocated for security considerations. Therefore, compared with conventional PCs that can run antivirus and firewall software, these NVSSs have been running without any protection, that is, directly exposed to the Internet.
- Usually, an NVSS, after going live, needs to always stay online, with preferential bandwidth allocation for the remote transmission of high-definition video and audio.
- These factors make NVSSs so vulnerable that hackers can take them down as easily as riding a bike. This is why NVSSs seem to be more appealing than conventional PCs for hackers.
The following subjective factors also contribute to the vulnerability of NVSSs: - To save on R&D costs, some vendors use versatile, open-source firmware or adopt the OEM mode without making any security enhancements. As a result, devices of different brands use the same default password or contain the same vulnerabilities. Once these vulnerabilities are known to hackers, an extensive impact will be caused. An example of this factor is one RCE vulnerability found in devices of more than 70 brands.
- Most NVSSs do not have any automatic system update and vulnerability remediation mechanisms. Even if high-risk vulnerabilities are disclosed, they can hardly be immediately fixed through system updates. Besides, users are not sensitive to the security of these devices.
- Users do not pay attention to security. Some set very simple passwords, such as “1234” and “admin”, and some even use empty or default passwords. All these make it easier for hackers to gain control over the related system and further use it to their advantage.
5.2 Security Measures
For NVSS vendors, their devices’ security issues have a negative influence on their brands and reputation, which, in turn, hinders expansion of their market shares. We call on major vendors to attach importance to the security of their products. Following are the recommended security measures:
- Discover vulnerabilities in products and fix them as soon as possible. For an OEM product, the vendor should promptly contact the OEM for remediation of vulnerabilities in that product and release patches on the official website.
- Establish a remote automatic update mechanism for devices, allowing users to load patches or upgrade firmware remotely or automatically.
- Set complexity requirements for all passwords, require users to change the default password after the first login, and use different initial passwords for different devices.
- Close unused ports.
For users, security issues associated with NVSSs may disclose their privacy, exposing their private lives or work to the public, which may pose a great security threat to users themselves and their families as well and blemish their reputation. What is even worse is that this may result in huge economic losses to businesses. Furthermore, bandwidth resources allocated to these devices are often exploited for such malicious behaviors as port scanning and DDoS attacks. Users are advised to adopt the following countermeasures:
- Avoid Internet-facing deployments wherever it is possible. Deploy NVSSs on private networks or allow access to NVSSs only through VPN connections.
- Set complex passwords.
- Patch the system or update firmware in time.
Security vendors are advised to take the following measures, which, however, are far from enough: - Release vulnerability information in time, monitor ongoing attacks, and notify regulatory agencies, users, and vendors of vulnerable systems when detecting vulnerabilities or attacks.
- Follow up with and analyze the perpetrating malware and its variants to help beef up the protection capability of security devices or services.
……
6 Sum-up
This report analyzes the distribution of NVSSs with security hazards and high-risk vulnerabilities in these systems and delves into NVSS-based botnets, revealing the security posture of NVSSs and the huge threats posed to the Internet. However, what is presented in this report is only a miniature of the actual security situation of numerous IoT devices. Around the world there are much more networked devices such as home routers, printers, and intelligent household appliances, all of which connect or will connect to the Internet in an open or semi-open manner. According to the prediction made by Gartner Inc., every day 5.5 million IoT devices will connect to the Internet in 2016. Throughout the year, there will be a total of 6.4 billion IoT devices staying online, a 30% increase from 2015. This figure will reach 20.8 billion in 2020. If no effective controls are taken, how shall we deal with numerous security threats by then[8]?
Fortunately, when this report was finished, there were regulatory authorities turning eyes to IoT devices and planning to take corrective measures for them. According to a report released by Euractive.com[9], the European Commission is planning new IoT rules, as a part of a new plan to overhaul the European Union’s telecommunications laws.
A Special Statement
All data for analysis is anonymized and no customer information appears in this report to avoid information disclosure by negligence on our part.
NSFOCUS DDoS Defense Research Lab and Threat Response Center (TRC) are keeping a close eye on the progress of DDoS attack events. For more information, please contact
NSFOCUS by Sina Weibo at:
https://blog.nsfocus.net/
NSFOCUS TRC by Sina Weibo at:
http://weibo.com/threatresponse
NSFOCUS by finding:
NSFOCUS at WeChat
For more information, please download the PDF: 2016-nsfocus-security-report-regarding-network-video-surveillance-systems