With the maturity of sensing, computing, and communication technologies, the Internet of Things (IoT) will be more and more widely used in various industries. Gartner, a market research agency, predicts that endpoints of the IoT will grow at a 33% CAGR from 2015 through 2020, reaching an installed base of 20.4 billion units, with almost two-thirds of them consumer applications. Spending on networked consumer and business endpoints will displace non-networked, growing at a 20% CAGR to $2.9 trillion.
In 2016, IoT was written into the Thirteenth Five-Year Plan, which pointed out that efforts should be made to push the development of cloud computing and IoT, promote the planning layout of IoT-aware facilities, and develop open-loop IoT application. This suggests that the government attaches great importance to various types of IoT infrastructure and applications strategically. Meanwhile, many IoT devices and applications are facing severe security challenges. On September 20, 2016, the famous security journalist, Brian Krebs’s website, KrebsOnSecurity.com, was attacked by a large-scale distributed denial-of-service (DDoS) attack, whose traffic peaked at 665 Gbps. Brian Krebs speculated that this attack was launched by means of the Mirai botnet. On the same day, France-based hosting service provider OVH became a victim of the record-breaking DDoS attacks that reached 1 Tbps, with peak traffic of 1.5 Tbps. On October 21, 2016, Dyn, a US-based DNS provider, received a global DDoS attack, whose attack source was confirmed to be the Miari botnet. This attack finally led to a massive network outage in the east coast of the United States. On November 28, 2016, a new Mirai variant disrupted Deutsche Telekom services. The reason why Mirai botnets are widely spread is that IoT devices exposed on the Internet are prone to security issues, such as weak passwords.
It is important to note that a majority of Mirai-infected IoT devices are directly exposed on the Internet. Therefore, it is noteworthy to research on exposed IoT assets. A feasible research methodology is to locate related IoT devices by using cyberspace search engines.
Unlike Internet search engines (such as Google and Baidu), cyberspace search engines (such as NTI[1], Shodan[2], and ZoomEye[3]) focus on IP addresses, corresponding devices, and services running on these devices. NSFOCUS Threat Intelligence (NTI) is a threat intelligence platform of NSFOCUS. According to detection results, security researchers can find vulnerabilities and quickly grasp the global distribution of such vulnerabilities.
In 2016, Trend Micro released a research report[9] based on Shodan data, which analyzed the exposed six key sectors (the government, emergence services, healthcare, utilities, finance, and education) on the Internet in America. At the 2017 RSA Security Conference, a researcher from Trend Micro delivered a keynote speech on the report content. In the IoT-related analysis, the report mainly focuses on the industrial control system. Though video surveillance devices and routers are mentioned, they are not the focal point and only mentioned as products detected in an industry.
In the context that IoT-related security issues are attracting more and more attention, it is necessary to analyze and identify IoT assets exposed on the Internet. Related data can be obtained for analyzing IoT security situation, solutions, and technically assessing vulnerabilities and risks.
In terms of the technical roadmap, considering the great differences between domestic and international IoT systems and products, this paper mainly analyzes IoT assets in China and describes their exposure, such as their distribution among cities and the distribution of ports on them, to illustrate what services are accessible on the Internet and potential security problems, with the purpose of raising the public awareness of IoT threat defense.
In chapters 2 and 3, the analysis is made respectively from the perspectives of IoT devices and IoT operating systems (OSs). Chapter 2 describes IoT devices exposed on the Internet and their distribution. Chapter 3 describes common IoT (OSs), providing readers with some knowledge of the OSs exposed on the Internet.
It is worth noting that, when an IoT device is exposed on the Internet, this does not necessarily mean that this device is vulnerable, but suggests that it is at risk of being attacked and exploited. For example, for a device that allows users to log in by typing a correct user name and password, if the user adopts a complex password, this device is not prone to a weak password vulnerability. However, once exposed on the Internet, the device will have a larger attacker surface. In an unexpected security event (such as heartbleed), the vulnerability in its Internet-exposed services will be found and exploited.
1.1 Research Methodology
This analysis is conducted based on NTI, ZoomEye, and Shodan data. There are mainly two data sources: One is information about the devices identified by search engines. If believing such information correct, we will directly use such information, for example, using “service:DAHUA-DVR” as the keyword on NTI to search for information about Dahua DVRs. The other data source is the search results of vendor names and models[1]. We will observe the search results and then adjust search keywords until satisfactory results appear. Here, take routers as an example. We first search for most models of mainstream home routers. For Hikvision products, we find that the banner[2] information of some services of their cameras contains “Server: Hikvision-Webs”. Therefore, we can use this character string as the keyword to search for Hikvison cameras.
Statement:
All data in this report comes from such public cyberspace search engines as NTI, Shodan, and ZoomEye.
1.2 Key Findings
By analyzing common IoT devices and OSs, we find as follows:
[1] We obtained model information from the respective official websites.
[2] Banner information refers to the return information received by search engines in the process of detecting IP addresses and ports. Take an HTTP message as an example. The received result contains HTTP headers and body. “Server: Hikvision-Webs” resides in the HTTP header section.
- Hikvision and Dahua have the most exposed network surveillance devices. Coastal provinces in the southeastern part of China witness the most exposed devices.
- Most routers exposed to China’s Internet are of domestic brands. The ports of these exposed routers mainly adopt UPnP and FTP protocols. The Sales of routers from Internet vendors are booming, with few exposed on the Internet.
- Thousands of routers in China are infected with malware Linux.Wifatch. The security situation of routers is not optimistic
- Hong Kong and Taiwan have the most exposed network printers, accounting for over 95% of the printers.
- The reason why most devices carrying an OS are probed is that they are deployed on the Internet with no default settings changed. For example, among the 7924 ports opened for the HTTP service on devices running DD-WRT, 22.6% are exposed because their titles contain “DD-WRT (build xxxxx=”infopage”>”. 98.6% devices running uClinux contain such banner information as “Server: uClinux/2.6.28.10 UPnP/1.0 MiniUPnPd/1.3”.
For a device that runs DD-WRT or uClinux and functions as a router, performing network address translation (NAT) makes it possible for its IP address to embody combined properties of multiple devices.
Introduction
Smart devices are becoming an integral part of people’s daily lives. Though IoT devices are very convenient, potential security issues should not be underestimated. Through data collection and analysis, we have learned that a dozen or so IoT devices are severely exposed, which are presented in Figure 2-1 in the descending order of the number of exposed devices. As shown in Figure 2-1, Internet-connected devices are most exposed. In China, routers and top the list, with a total number of more than 5 million.

Of course, IoT device are far more than those presented in the figure. On the one hand, some lesser-known devices (such as access control device, temperature monitoring system, and vehicle dispatching system) and the devices used in special industries are not listed. If necessary, we will complement or update device information in subsequent reports. On the other hand, many IoT devices connect to LANs and communicate with IoT-based applications via NAT. Hidden among gateway devices, such devices will not be exposed on the Internet.
Video Surveillance Devices
As very important IoT devices, video surveillance devices have been involved in many international IoT security events in the past several years. Therefore, this section provides statistics on and analyzes exposed video surveillance devices in China.
Overall Picture
According to the World Market for CCTV and Video Surveillance Equipment (2014) released by IHS, Hikvision, Dahua, Axis Communications, Panasonic, Samsung Techwin, Bosch Security Systems, Pelco, Honeywell, Avigilon, Tyco, Sony, Uniview, Aventura, UTC, and Infinova were the top 15 vendors enjoying the biggest market share. Hikvision was number one, followed by Dahua. However, the gap between the two was huge[19]. Figure 2-2 shows the market shares of video surveillance devices in China in 2013 released by HIS.

By investigating the exposure of the preceding video surveillance devices and that of devices from other vendors, we find as follows:
Viewpoint 1: Hikvision and Dahua have the most exposed devices.
Up to today, the products from a dozen or so network surveillance device (network hard disk camera, web camera, and video server) vendors are suffering a varying degrees of exposure. Hikvision and Dahua have the most exposed devices.
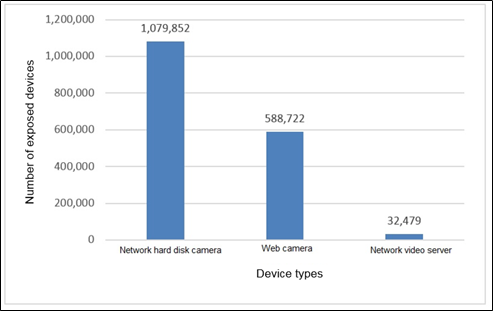
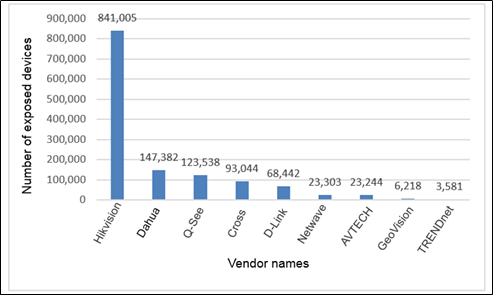
As shown in Figure 2-3 and Figure 2-4, more than one million surveillance devices are exposed in China, mostly network hard disk cameras. However, the number of exposed devices from Hikvision and Dahua reaches nearly one million.
1.1.1 Analysis of Specific Vendors
As shown in Figure 2.4, Dahua and Hikvision have the most exposed network surveillance devices. This section takes them as the main analysis object and conducts the analysis from the perspectives of open port and geographical location.
- Open Ports
Viewpoint 2: The ports exposed on network surveillance devices are mostly the default ones.
Table 2-1 lists the ports frequently appearing, common ports, and corresponding protocols on exposed devices. According to our investigation, default ports vary with surveillance device vendors. For example, the default port for the video data service of Dahua surveillance devices is 37777 and that for the data service of Hikvision devices is 8000. Likewise, attackers can also find these default ports by referring to related materials and then scan to locate devices. Therefore, we recommend that the default port of each service should be changed, thereby reducing the risk of being detected by the attacker’s broad-spectrum scanning.

| Port | 80 | 554 | 443 | 49152 | 8080 |
| Protocol | HTTP | RSTP | HTTPS | UPnP | HTTP |
……
Conclusion
The preceding sections analyze some common IoT OSs, including Nucleus, OpenWrt, Raspbian, uClinux, and VxWorks in terms of the exposed ports and application-layer protocols. Through analysis, we have the following findings:
- Devices running one of these five operating systems have some common signatures, which are contained in the banner of services. For example, VxWorks hosts deliver the message “220 VxWorks (VxWorks5.5.1) FTP server ready” in the banner and uClinux hosts deliver the message “Server: uClinux/2.6.28.10 UPnP/1.0 MiniUPnPd/1.3” in the banner.
- Some devices are deployed with default system settings for connection to the Internet. For example, the title field of HTTP in the DD-WRT firmware provides information like “DD-WRT (build xxxxx=”infopage”>“.
- Sometimes an IP address (device) is associated with multiple intranet IP addresses (devices). This is probably because multiple devices are mounted to a router via UPnP. As a result, one IP address delivers different services with different device IDs because the NAT mapping makes it possible for an IP address to embody combined properties of multiple devices.
Other operating systems, such as Brillo, TinyOS, LiteOS, Linino OS, Ostro, FreeRTOS, Contiki, MICO, and Zephyr, are not analyzed here because they have much smaller installed bases according to results returned by cyberspace search engines.
Sum-Up
Chinese territory from two perspectives: One is the distribution of various devices on the Internet and the other is the exposure of IoT operating systems on the Internet.
Owing to the limited time and energy, we cannot guarantee that our analysis covers all types of devices and all operating systems in use. And even for the covered device types and operating systems, we cannot safely say that all related data is 100% accurate. In spite of this, we tried our utmost to ensure the comprehensiveness and accuracy of data by basing our research on the comparison and analysis of data from three search engines instead of relying only on one search engine. Then, our purpose is to call people’s attention to the necessity and urgency of IoT protection by revealing the exposure of IoT devices on the Internet. In this sense, a few omissions or some noisy data will not prevent readers from understanding our viewpoints presented in this article.
This article dwells upon such IoT devices as video surveillance devices, routers, and printers. In future, we will analyze the exposure of more devices and may update data provided here as necessary.
Based on our findings, we recommend users and vendors to do the following for their IoT devices:
- Users:
- Enhance security of user names and passwords by changing initial passwords and weak passwords.
- Disable unused ports such as ports 21 (FTP), 22 (SSH), and 23 (Telnet).
- Upgrade device firmware in time.
- Vendors:
- For the first use of devices, force users to change the initial password and check the complexity of passwords set by users.
- Provide an automatic online upgrade option for device firmware to reduce the exposure of networked devices to security risks.
- Provide default settings according to the principle of opening the fewest ports required to reduce the possibility of ports exposed on the Internet.
- Set access control rules to strictly control external access from the Internet.
Analysis on Exposed IoT Assets in China-0521
