With the network threat forms becoming more and more diversified and complex and challenges from advanced persistent threat (APT) attacks, new-generation threats spread more quickly on a larger scale, covering mobile devices, desktops, networks, web, applications, and social networks. In the new normal situation, it is far from enough for customers to obtain threat information only from traditional network intrusion prevention system (NIPS) and network intrusion detection system (NIDS) devices, and professional, systematical, and intelligent devices are becoming really crucial. In particular, with the development of the Internet and improvement of user experience requirements, network threat behaviors should be detected through big data analysis to show customers the entire dynamic attack process intuitively.
To meet customer requirements, simplify device operations, improve customers’ intuitive awareness of the attack process, and adapt to the changes of new-generation threats, the dimensions for dividing traditional NIPS vulnerability rules should be completely adjusted and complete solutions should be provided to change the situation where one alert for one event previously provided by NIPS. By redividing vulnerability rules by attack chains and based on analysis of logs for alerts reclassified according to adjusted rules by the data processing center, the status analysis module presents customers with the entire attack process stage by stage (probing and scanning, penetration, compromise, tool installation, and malicious behavior) from the perspective of big data analysis.
What is “new normal”? Actually, “new normal” is a phrase coined by President Xi Jinping. “New” means it is different from the old and “normal” means the expected state. “New normal” indicates a development status which is different from the previous one, trend, and irreversible. So, what is the new normal of network security threats? It relies on large-scale security intelligence system and professional, intelligent big data analysis module and makes full use of data-driven security, forming an around-the-clock, all-round, multidimensional, and hierarchical network security threat aware solution integrating the cloud, people, and devices.
Alerts Generated by Traditional Devices
Alert logs are the first-hand intuitive alert information displayed for users after intrusion behaviors are detected. The number of alert logs varies with the network device access layer. To improve the overall effect of threat aware, the presentation form of network threats needs to be converted and improved, extending from virtual media to entities and changing from local to global view. This calls for a threat aware system, a brand new paradigm of next-generation detection devices. Therefore, the analysis of alert logs is of great importance, which includes the classification of alert logs. The classification dimensions directly affect customers’ identification and judgement of alert logs, further affecting the presentation effect of threat trend aware.
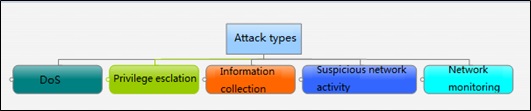
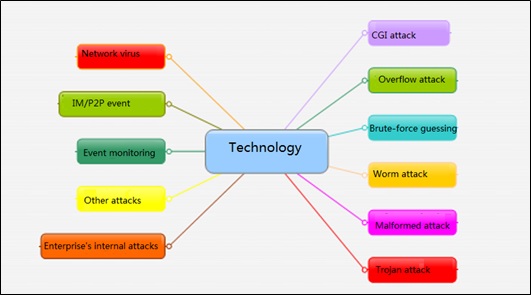
Types of Vulnerability Rules Provided by Traditional Devices
Currently, there are as many as thousands of rules on a device. Rule types are closely associated with proper policy configuration. On traditional NIPS devices, rules are classified from different dimensions. Rules, which used to be disorderly, are now in order and displayed by attack type, protocol type, service type, technology, and risk level. The following figures show two types of rule classification.
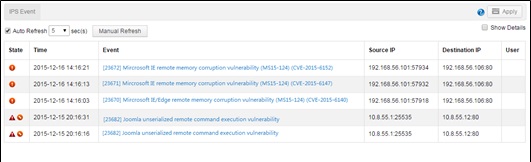
Display of Alerts
One alert is generated for one attack, providing limited information.
Weaknesses of Rule Types Provided by Traditional Devices
On traditional NIPS devices, rules are classified by attack type and displayed disorderly. Therefore, users cannot get the entire attack process and the attack effect cannot be intuitively displayed. This cannot lead users to make a correct judgment on attack behaviors and adapt to network security protection solutions under the current big data situation.
Threat Aware System
To build a threat aware system under the new normal, a new alert log analysis platform should be built, providing the analysis of massive data based on new rules, new classification standards, and attack chains. To cope with the changes of network attack behaviors, the system should be upgraded to a revolutionary state attack behavior alert scheme. Based on the actual diversified attack forms, the inherent mode of “one alert for one attack” should be ultimately changed, realizing the transformation of the way of thinking and improving the product quality, solutions, and user experience. To enable users to comprehensively control the dynamic threat aware, based on big data mining and intelligent data analysis, the threat aware trend solution for the new normal will be formed, really jumping out of the cycle of traditional NIPS detection alert form.
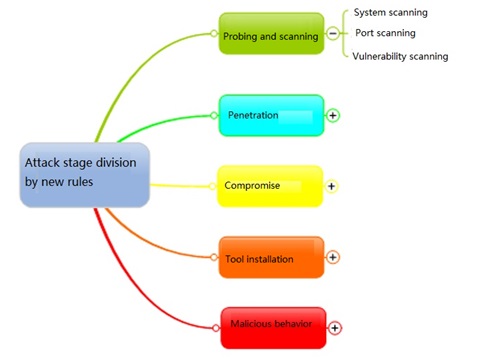
Criteria for Attack Chain Model-based Rule Classification
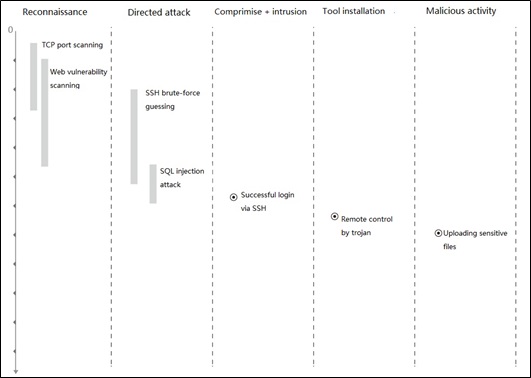
The classification of rules will affect the construction of the whole attack chain and the effect of threat aware. To fit in new attack behaviors and attack methods, the existing rules are divided into five attack stages, including probing and scanning, penetration, compromise, tool installation, and malicious behavior.
- Probing and scanning: This refers to the scanning of the target before attack, including network scanning, system scanning, port scanning, and vulnerability scanning. Scanning is the initial stage of intrusion. By collecting information and grasping the system and vulnerability information of the target machine, scanning makes compromise easier.
- Penetration: In this phase, the attacker has scanned the target host. Alternatively, the attacker may directly launch attacks against the target host by exploiting a heap or stack vulnerability, web system platform vulnerability, logical configuration error, or memory corruption vulnerability.
- Compromise: After the target host is successfully compromised, the attacker could do whatever he wants, such as login to the system via FTP or Telnet password guessing.
- Tool installation: After successfully logging in to the target host, the attacker could install malware or trojan programs to control the target host and download other malware.
- Malicious behavior: After the malware is installed on the target host, the malware could be used to conduct such malicious behaviors as controlling links and performing malicious operations on the target host.
Display
To display attack stages, duration, and time, attacks are displayed as follows.
Threat Aware System Under the New Normal
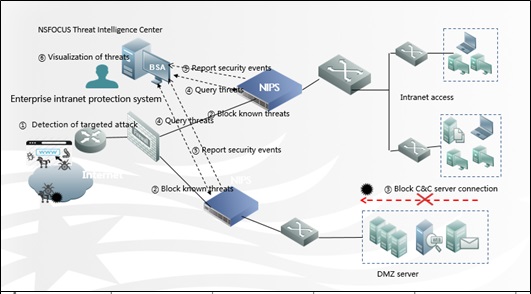
In addition to reclassification of rules, the entire attack process should be visualized to users more intuitively by using data mining and data analysis technologies, including the source IP address, destination IP address, exploited vulnerability, number of attacks, and attack stage. After the classified alert information is uploaded to the data processing center (BSA), BSA performs data mining and analysis and then visualizes the result. It relies on massive data and professional, intelligent big data analysis module and makes full use of data-driven security, forming an around-the-clock, all-round, multidimensional, and hierarchical network security threat aware solution integrating the cloud, people, and devices.
Threat Aware Effect with Big Data Analysis
To make users understand the attack trend more intuitively, the big data processing center provides various display modes, allowing users to understand the network attack behaviors from the perspectives of attack time and attack count.
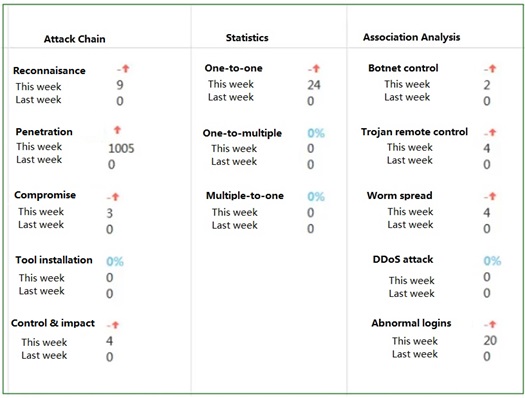
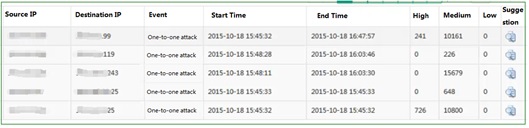
To provide more attack information, attack alert information is allocated for different attack events, including one-to-one, one-to-multiple, and multiple-to-one modes. In addition, the number of attacks in a specified time and attack event information are also displayed. To help users to timely understand the overall attack trend, the attack information is visualized.
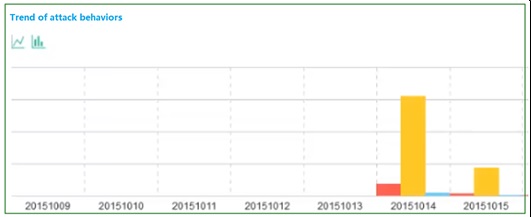
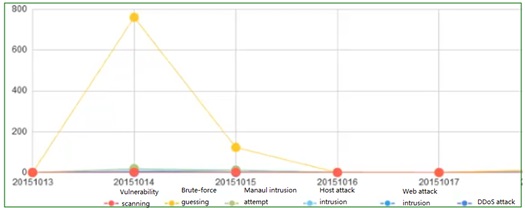
The following shows the curve of signatures of different attack behaviors in different time periods.
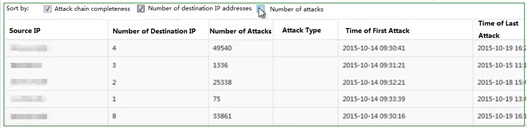
The following shows the statistical information of attack IP addresses.
The following shows information traced after association analysis.
Through the analysis of alert logs, visualized analysis and display of the attacks against the target host is provided by dividing the attacks by attack time and attack stage, helping users to understand attack behaviors in the affected system. In the following figure, each color represents an attack stage, clearly indicating the attack status of the target host.
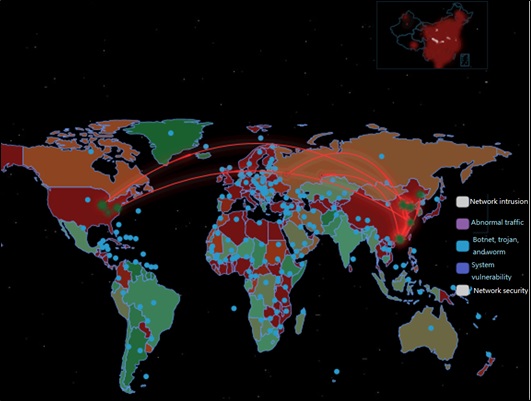
With attack behaviors in the global sphere in mind, dynamic aware can finally deploy countermeasures to enhance the capability of preventing known and unknown threats and nip potential risks in the bud by analyzing, detecting, tracing, and restoring the entire attack process of attack and locating the vulnerable spots with the professional and intelligent big data mining technology.
The following figure shows the global network risk trends from the perspectives of attack sources, attack types, and attack targets, thereby providing comprehensive and in-depth threat alerts and helping users to take measures promptly. With alert logs as the core, the data processing center focuses on data visibility, and supports multi-level network architecture data retrieving.
Summary
The Internet makes everything connected. The connection also brings security risks. Network security and Pandora’s box are like the shadow following the form since the emergence of the Internet. In particular, people are heavily relying on big data, cloud computing, and mobile Internet. Networks are ubiquitous, from energy and traffic infrastructure to daily basic necessities of life. Security risks are on the rise unprecedentedly. The traditional detection method of NIPS devices is no longer applicable to network threats in the big data-driven Internet of Things (IoT). A new system should be developed based on a new rule classification model and massive data obtained around the globe. It should incorporate the intelligent big data mining and analysis module. By making full use of data-driven security, it can provide a visualized detection and alerting platform featuring global coverage, multi-source reporting, and hierarchical connection. This is what we call an around-the-clock, all-round, multidimensional, and hierarchical network security threat aware solution integrating the cloud, people, and devices.
Chinese version: https://blog.nsfocus.net/threat-sensor-system-base-attack-chain/