Recently, Dahua Technology, a well-known security camera and digital video recorder (DVR) vendor in China, released firmware updates to address a serious security issue in certain products. Before the vendor made an official statement on this issue, however, a security researcher named Bashis said that this vulnerability seemed to be a backdoor intentionally left by the vendor and so made his findings public without notifying Dahua in advance.
By exploiting this vulnerability, an attacker can access the user database of a Dahua camera without needing administrative privileges and extract the user name and password hash. Then the attacker can directly use this user name and password hash to log in to the device and obtain related privileges.
For details, visit the following links:
https://ipvm.com/reports/dahua-backdoor?code=bash
http://us.dahuasecurity.com/en/us/Security-Bulletin_030617.php#none
According to Dahua Technology’s official statement, the following models are affected:
- DH-IPC-HDW23A0RN-ZS
- DH-IPC-HDBW23A0RN-ZS
- DH-IPC-HDBW13A0SN
- DH-IPC-HDW13A0SN
- DH-IPC-HFW13A0SN-W
- DH-IPC-HDBW13A0SN
- DH-IPC-HDW13A0SN
- DH-IPC-HFW13A0SN-W
- DHI-HCVR51A04HE-S3
- DHI-HCVR51A08HE-S3
- DHI-HCVR58A32S-S2
NSFOCUS Threat Intelligence’s Analysis on the Global Impact of This Vulnerability
- Global Distribution of Vulnerable Devices
According to our statistics, the number of worldwide devices with this vulnerability reaches 1,140,446, which are distributed as follows:
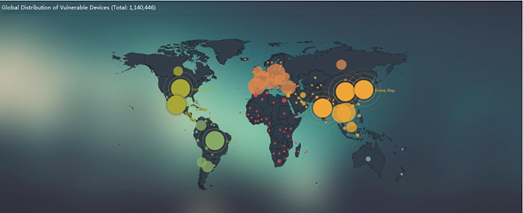
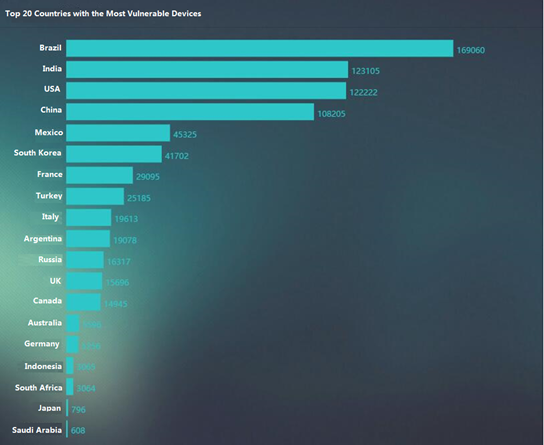
Top 20 countries with the most vulnerable devices are shown as follows:
- Nationwide Distribution of Vulnerable Devices in China
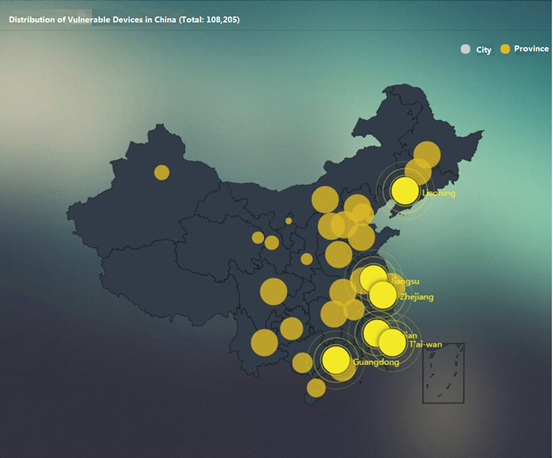
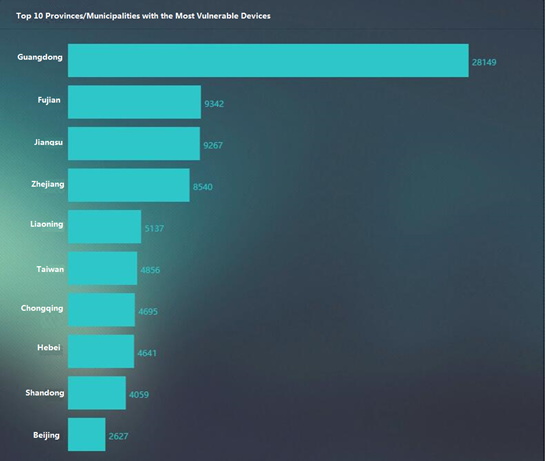
Our statistics reveal that there are 108,205 devices in total affected by this vulnerability in China. The following figure shows the distribution of these vulnerable devices in different provinces.
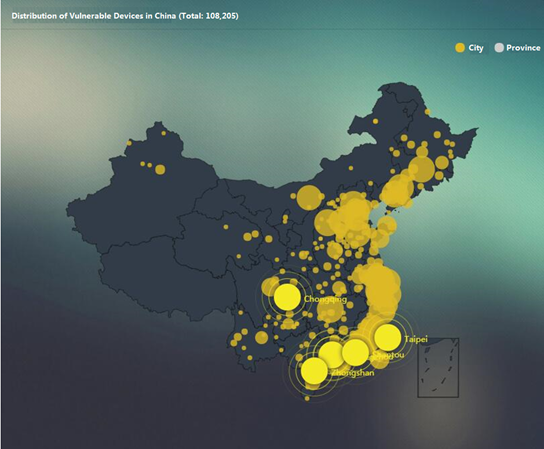
The following figure shows the distribution of these vulnerable devices in major cities.
The following figure shows top 10 provinces and municipalities with the most vulnerable devices.
Vulnerability Analysis
- Prerequisites for Vulnerability Exploitation
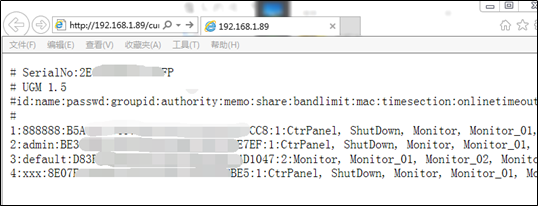
As shown in the following figure, after accessing a specific device by typing its IP address in the address bar, the attacker can obtain all data of the user database, including such sensitive information as user names and hashed passwords for access to the device. For the sake of security, sensitive information is obfuscated.
- Vulnerability Exploitation
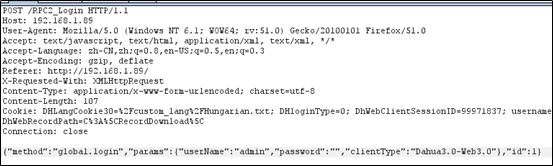
The hashed passwords do not need to be cracked before being used to log in to the device and obtain related privileges, as shown in the following figure.

- Consequence
After login to the device, the attacker can view and modify its configurations such as the admin password.
Moreover, after such remote login, the attacker can directly obtain sensitive information, such as images, stored on the device, posing a serious threat to users’ privacy.
Solutions
- Vendor Solutions
Dahua Technology has identified 11 models affected by this vulnerability and released firmware updates. Users should check their models against the following table and upgrade their devices as soon as possible.
| DH-IPC-HDW23A0RN-ZS | Download |
| DH-IPC-HDBW23A0RN-ZS | |
| DH-IPC-HDBW13A0SN | Download |
| DH-IPC-HDW13A0SN | |
| DH-IPC-HFW13A0SN-W | |
| DH-IPC-HDBW13A0SN | Download |
| DH-IPC-HDW13A0SN | |
| DH-IPC-HFW13A0SN-W | |
| DHI-HCVR51A04HE-S3 | Download |
| DHI-HCVR51A08HE-S3 | Download |
| DHI-HCVR58A32S-S2 | Download |
- Technical Solutions
- If you are not sure whether your devices are affected by this vulnerability, you can use NSFOCUS Remote Security Assessment System (RSAS V5 or V6), Web Vulnerability Scanning System (WVSS), or ICS Scanning System (ICSScan V6.0) to detect this vulnerability.
Remote Security Assessment System (RSAS V5):
http://update.nsfocus.com/update/listAurora/v/5
Remote Security Assessment System (RSAS V6):
http://update.nsfocus.com/update/listRsasDetail/v/vulweb
http://update.nsfocus.com/update/listRsasDetail/v/vulsys
Web Vulnerability Scanning System (WVSS):
http://update.nsfocus.com/update/listWvssDetail/v/6/t/plg
ICS Scanning System (ICSScan V6.0):
http://update.nsfocus.com/update/listICSScanDetail/v/vulsys
You should upgrade your devices to the latest version by downloading upgrade packages from the preceding links before using them to detect vulnerabilities.
- Use NSFOCUS’s protection product (NIPS, NIDS, NF, or WAF) to protect against the exploitation of the vulnerability.
Network Intrusion Prevention System (NIPS):
http://update.nsfocus.com/update/listIps
Network Intrusion Detection System (NIDS):
http://update.nsfocus.com/update/listIds
Next-Generation Firewall (NF):
http://update.nsfocus.com/update/listNf
Web Application Firewall (WAF):
http://update.nsfocus.com/update/wafIndex
You should upgrade your devices to the latest version by downloading upgrade packages from the preceding links before using them for protection.
Sum-Up
This vulnerability exists because of Dahua Technology’s negligence and mistake in engineering management. It allows access to and download of the user database of a specified device without requiring administrative privileges. After obtaining sensitive information such as user names and passwords, an attacker can remotely log in to the device, thus posing a serious threat to users’ privacy. After this vulnerability was disclosed, NSFOCUS determined that it is easy to exploit, with an extensive impact, and so engaged in prompt response activities, including analyzing its cause and working principle and providing customers with secure and reliable detection and protection solutions.
Statement
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete any information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.
