On October 31, 2016 (local time), Cisco Talos published three integer overflow vulnerabilities with the Memcached server on its official website http://www.talosintelligence.com.
The vulnerability assigned CVE-2016-8704 was found in the process_bin_append_prepend function. CVE-2016-8705 is about an integer overflow in the process_bin_update function. The last vulnerability, namely CVE-2016-8706, has been confirmed to be associated with the process_bin_sasl_auth function. All these vulnerabilities could be exploited to cause a heap overflow, leading to remote code execution. For details, click the following links:
http://www.talosintelligence.com/reports/TALOS-2016-0219/
http://www.talosintelligence.com/reports/TALOS-2016-0220/
http://www.talosintelligence.com/reports/TALOS-2016-0221/
For the official release notes regarding fixes for these vulnerabilities, visit the following link:
https://github.com/memcached/memcached/wiki/ReleaseNotes1433
What Is Memcached?
Memcached is a high-performance, distributed memory object caching system for speeding up dynamic web applications by alleviating database load. Specifically, it speeds up dynamic database-driven websites by caching data and objects in RAM to reduce the number of times an external data source must be read. Memcached is a hashmap of key-value pairs. Its daemon is written in C, but the client can be written in any languages and communicates with the daemon via the memcached protocol.
Affected Versions
- Memcached version < 1.4.33
Unaffected Versions
- Memcached version = 1.4.33
NSFOCUS NTI’s Analysis on the Global Influence of These Vulnerabilities with Memcached
- Global Distribution of Vulnerable Devices
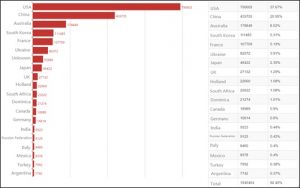
As of today, up to 2,098,840 devices around the world have been affected by these vulnerabilities.
The USA has the greatest number of vulnerable devices (37.67%), followed by China (20.95%) and Australia (8.52%). Other countries making it into the list include South Korea, France, Ukraine, Japan, UK, Holland, and South Africa.
Vulnerable devices in top 20 countries account for 92.45% of the global total, and the remaining 7.55% are scattered in other countries and regions.
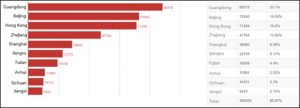
- Distribution of Vulnerable Devices in China
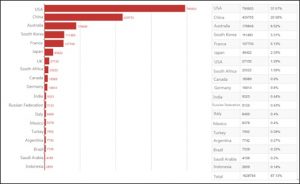
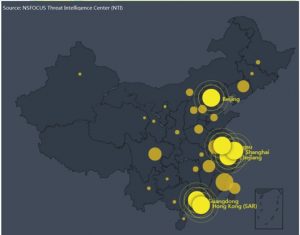
Up to 439,781 devices in China are affected by these vulnerabilities. Guangdong has the greatest number of vulnerable devices (88,378), followed by Zhejiang, Beijing, Hong Kong, and other provinces. From the perspective of cities, Beijing, Shanghai, Guangzhou, Shenzhen, Hangzhou, and Hong Kong, where the Internet is widely used, are most severely affected.
382,054 vulnerable devices are found in the top 10 provinces, accounting for 86.87% of the national total. The remaining 13.13% are scattered in other provinces and regions.
Vulnerability Analysis
- CVE-2016-8704
- Cause of the Vulnerability
In the process_bin_append_prepend function, signed integers and unsigned integers are added, subtracted, and assigned values in a mixed manner, leading to an integer overflow, which would further cause a heap overflow or even remote code execution.
- Vulnerability Details
Memcached uses two versions of the protocol for storing and retrieving data: One is based on ASCII and the other is based on binary. The binary protocol is optimized for size. When the binary protocol is involved, by issuing the Append (opcode 0x0e), Prepend (opcode 0x0f), AppendQ (0x19), or PrependQ (opcode 0x1a) command that appends or prepends data to an existing key-value pair, an attacker could cause an integer overflow.
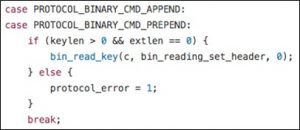
While parsing a binary packet, the process ends up in the following switch case if a command like Append or Prepend is issued:
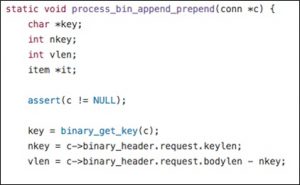
Obviously, no check is performed on the specified value of bodylen. Then the process ends up in the process_bin_append_prepend function that sees an integer overflow:
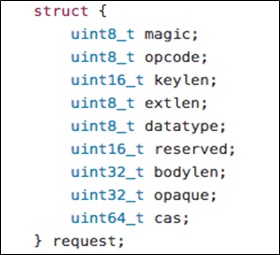
The request structure in binary_header of the structure parameter conn is defined as follows:
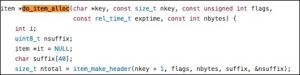
It can be found that keylen and bodylen are unsigned integer variables, while nkey and vlen are signed. After keylen is assigned to nkey, an integer overflow may occur during vlen calculation, causing the value of vlen to be negative. Values of nkey and bodylen can be directly controlled by users. The calculated vlen value will be used in do_item_alloc, which allocates the memory for the item and copies the key. The section of code associated with do_item_alloc is as follows:
nbytes corresponds to the previously calculated vlen value. An integer overflow occurs during vlen calculation, making ntotal too small. As a result, the memory allocated by slabs_alloc is too small to contain the key, leading to a heap overflow. At the time of the overflow, the contents of nkey and the contents of memory pointed to by key are under direct control of the attacker.
- CVE-2016-8705
- Cause of the Vulnerability
In the process_bin_update function, signed integers and unsigned integers are added, subtracted, and assigned values in a mixed manner, leading to an integer overflow, which would further cause a heap overflow or even remote code execution.
- Vulnerability Details
An attacker could cause an integer overflow by sending such commands as Set (opcode 0x01), Add (opcode 0x02), Replace (opcode 0x03), SetQ (opcode 0x11), AddQ (opcode 0x12), and ReplaceQ (opcode 0x13) to the Memcached server.
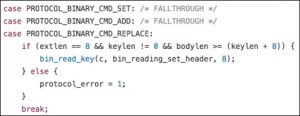
In the process of sending the preceding commands, the process ends up in the following case:
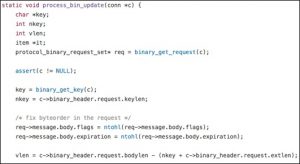
keylen is a signed integer and bodylen is an unsigned integer. After execution, the process ends up in the process_bin_update function:
nkey and vlen are singed integers and bodylen is an unsigned integer. An integer overflow may occur in calculation of vlen. bodylen and keylen are checked in the preceding case, but the automatic switch of data types may help bypass the check. The calculated vlen value will be used in do_item_alloc which allocates the memory and copies the key. Since an integer overflow occurs during calculation of vlen, the resulting value used as the size for allocation is too small to hold the key, causing a heap buffer overflow. At the time of the overflow, the contents of nkey and the contents of memory pointed to by key are under direct control of the attacker.
Due to various checks, this vulnerability can be triggered only when the following conditions are met:
- The value of extra_len must be 8.
- The value of body_len must be greater than key_len when compared as unsigned integers.
- key_len must be greater than 0.
- body_len must be in the 0xFFFFFFF0–0xFFFFFFFF range.
- CVE-2016-8706
- Cause of the Vulnerability
In the process_bin_sasl_auth function, signed integers and unsigned integers are added, subtracted, and assigned values in a mixed manner, leading to an integer overflow, which would further cause a heap overflow or even remote code execution.
- Vulnerability Details
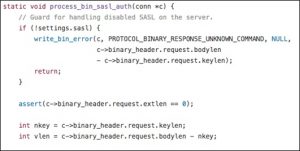
Memcached can enable SASL-based authentication for compilation. The process_bin_sasl_auth function is responsible for processing authenticated packets:
nkey and nkey are signed integers and body_len is an unsigned integer. An integer overflow may occur in calculation of vlen, resulting in a negative value of vlen. The calculated vlen value will be used in do_item_alloc which allocates the memory and copies the key. Since an integer overflow occurs during calculation of vlen, the resulting value used as the size for allocation is too small to hold the key, causing a heap buffer overflow. At the time of the overflow, the contents of nkey and the contents of memory pointed to by key are under direct control of the attacker.
Workaround
- Limit access to the application port (11211 by default) of Memcached. For example, use an access control list (ACL) to control which source IP addresses can access the Memcached service.
Solution
- The vendor has released an update. Users are advised to upgrade Memcached to the latest version (1.4.33) by downloading the update from the vendor’s official website:
http://www.memcached.org/files/memcached-1.4.33.tar.gz
Recommended Solutions
- Products
Remote products:
- Use NSFOCUS cloud emergent vulnerability online detection service for free detection. For details, see the following link:
Local products:
- Authorize NSFOCUS RSAS to check services.
- Use NSFOCUS’s protection product (IPS, IDS, or NF) to protect against the exploitation of the vulnerability.
- If you have purchased any of the preceding products or services of NSFOCUS, upgrade the product or service for effective protection.
- Services:
- Short-term service: Contact NSFOCUS for onsite handling (penetration testing + emergency response) to ensure that risk points are immediately eliminated in the network and the event impact is minimized. After the handling, an event analysis report is provided.
- Mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services to eradicate risks and prevent events from recurring.
- Long-term service: NSFOCUS provides industry-specific risk mitigation solutions (threat intelligence + attack traceback + professional security service).
Statement
==========
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete any information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
============
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.