OpenSSH contains a memory exhaustion issue during key exchange. An unauthenticated client can increase the memory allocated to each connection on the server to 384 MB, by repeating the KEXINIT process. An attacker can exploit this vulnerability by initiating multiple connections, to exhaust memory resources of the server and therefore lead to a denial of service.
This vulnerability (CVE-2016-8858) exists in the kex_input_kexinit() function. For details, see the following:
http://www.securitytracker.com/id/1037057
What Is OpenSSH?
OpenSSH is a free, open source implementation of the SSH (Secure Shell) protocols. The SSH protocol family can be used for remote control or file transmission between computers. Traditional SSH implementations, such as Telnet, RCP FTP, Rlogin and RSH, are very unsecure and transmit passwords in plaintext. OpenSSH provides a server-side daemon and client tools to encrypt data in remote control and file transmission, replacing previous similar services.
Affected Versions
OpenSSH 6.8-7.3
Unaffected Versions
OpenSSH < 6.8
Vulnerability Analysis
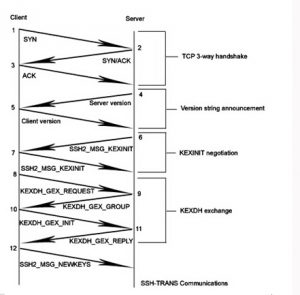
The handshake procedure of the SSH transport layer is as shown in the figure below. During the authentication phase, the SSH client sends an authentication request to the server, and the server authenticates the client. The principle of triggering the vulnerability is: after receiving an SSH2_MSG_KEXINIT packet from the client, the server will allocate up to 384 MB of memory as requested. By default, if the server processes 100 concurrent connections, it will consume up 38400 MB of the server’s memory resources, leading to a remote denial-of-service vulnerability.
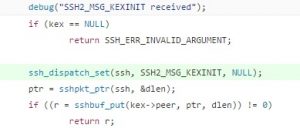
To fix this vulnerability, the processing of KEXINIT messages is added to the kex_input_kexinit() function. As shown in the following figure, “ssh_dispatch_set(ssh, SSH2_MSG_KEXINIT, NULL)” is added to the remediation code.
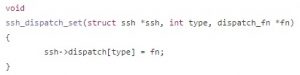
The definition of ssh_dispatch_set() is:
The remediation code leads to ssh->dispatch[SSH2_MSG_KEXINIT]= NULL. This is, after receiving a KEXINIT message, the server sets it to NULL and releases the occupied memory, avoiding the vulnerability.
NSFOCUS NTI’s Analysis on the Global Influence of This Vulnerability
- Global Vulnerable Device Distribution
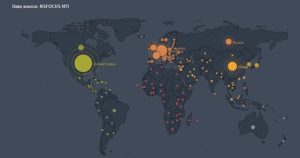
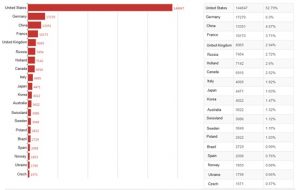
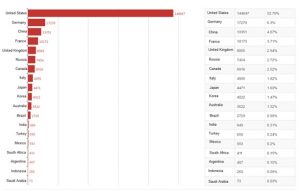
As of today, we have discovered up to 274,371 vulnerable devices around the world. The United States have the most vulnerable devices (52.79%), followed by Germany (6.3%), China (4.87%), France, UK, Russia, Holland, Canada, Italy, and other countries.
91.61% of the vulnerable devices reside in the top 20 countries, and the remaining 8.39% in other countries.
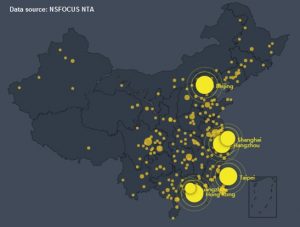
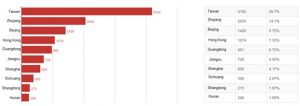
- Vulnerable Device Distribution in China
Up to 6039 devices in China are affected by this vulnerability. Taiwan has the most vulnerable devices (1752), followed by Beijing, Shandong, and other provinces. 84.47% of the vulnerable devices reside in the top 10 provinces, and other 15.53% of them in other provinces.
Recommended Solutions
- The vendor has not released a version update but provides a remediation to the source code. Users are advised to upgrade and compile the source code. The remediation code is available at:
- http://cvsweb.openbsd.org/cgi-bin/cvsweb/src/usr.bin/ssh/kex.c#rev1.127
- Until the vendor provides a version update, users are advised to temporarily disable the OpenSSH service, or adopt measures of monitoring the memory usage of the service if the service is necessary.
- Limit the number of concurrent OpenSSH connections. Since each OpenSSH connection can consume up to 384 MB of memory, you can set the maximum number of allowed concurrent connections based on your upper limit of memory usage:
- Authorize NSFOCUS RSAS to check services.
- Use NSFOCUS’s protection product (IPS, IDS, or NF) to protect against the exploitation of the vulnerability.
- If you have purchased any of the preceding products or services of NSFOCUS, upgrade the product or service for effective protection.
- Use NSFOCUS’s short-term service: NSFOCUS engineers handle the related event onsite to ensure that risk points are immediately eliminated in the network and the event impact is minimized. After the handling, an event analysis report is provided.
- Use NSFOCUS’s mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services to eradicate risks and prevent events from recurring.
- Use NSFOCUS’s long-term service: NSFOCUS provides industry-specific risk mitigation solutions (threat intelligence + attack traceback + professional security service).
Statement
==========
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
============
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.