On June 8 and June 27, 2016, Kaspersky Lab discovered a new wave of targeted attacks in multiple regions around the world. The attacker sent spear phishing emails to entice victims to execute malware in these emails for the purpose of obtaining key business data from the target network.
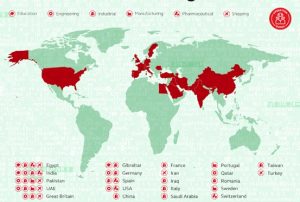
ccording to the current analysis, these attacks targeted industrial and engineering sectors. By using malware compiled on the basis of commercial spyware, the attacker has successfully attacked networks of over 130 organizations from 30 countries, including Spain, Pakistan, United Arab Emirates, and China, as shown in the following figure.
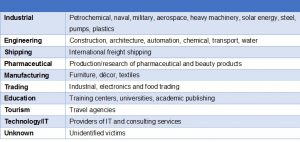
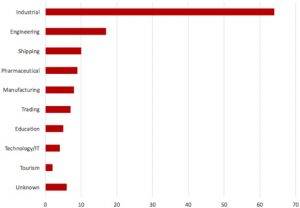
The following table lists victim industry types.
To obtain core data from target networks, the attacker usually sends data to senior members and executives of targeted organizations, including the following:
- Chief executive officer
- Chief operations officer
- General manager
- General manager, sales and marketing
- Deputy general manager
- Finance and admin manager
- Business development manager
- Manager
- Export manager
- Finance manager
- Purchase manager
- Head of logistics
- Supervisor
- Sales executive
- Engineer
Attack Process
Executive Summary
The malware in the email attachment is based on the commercial spyware HawkEye, which is sold openly on the Darkweb and provides a variety of tools for attackers. Once installed, the malware will collect the following data from and perform the following operations on the victim PC:
- Keystrokes
- Clipboard data
- Bank PIN codes
- Monitoring screens
- Downloading and executing files
- Dropping and executing bound files
- Disabling system functions: cmd, reg, taskmgr, msconfig, and so on
- Bitcoin wallet information
- FTP server credentials
- Account data from browsers
- Account data from messaging clients (Paltalk, Google Talk, AIM …)
- Account data from email clients (Outlook, Windows Live mail …)
- Information about installed applications (Microsoft Office)
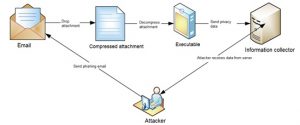
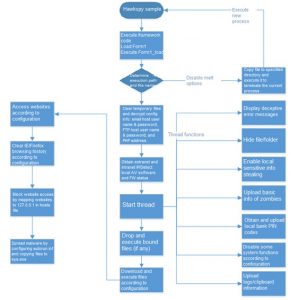
The following figure shows the execution process.
The Hawkspy sample can perform the following actions:
- Accessing websites
- Blocking website access by configuring the “hosts” file
- Clearing the browsing history from the Internet Explorer or Firefox browser
- Setting the broadcast mode besides automatic startup to infect other hosts via autorun.inf
Sample Analysis
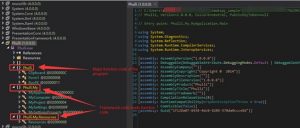
The Hawkspy sample is written in C#. The source code of the program can be directly viewed by using dnSpy. As the code is not obfuscated, we can see the complete structure of the program, within which Phulli is the major function code. Phulli.My and Phulli.Resources, as the framework code, are responsible for loading Phulli and Form1.
Checking the code of Phulli.Form1, we find that Form1_Load is the major function framework code, which contains information of the configuration file, as shown in the following figure.
Code for the configuration file is as follows:
//Configuration file:
// Phulli.Form1
// Token: 0x06000020 RID: 32 RVA: 0x0000261C File Offset: 0x0000081C
public Form1()
{
base.Load += new EventHandler(this.Form1_Load);
Form1.__ENCAddToList(this);
this.encryptedemailstring = "kU9AKBY**********************************0f5Ki+"; //Email address
this.encryptedpassstring = "3/BxGI***********************************gtq6ug="; //Email password
this.encryptedsmtpstring = "R6xOQ********************************D7agYk="; //SMTP server
this.portstring = "5000"; //Port number
this.timerstring = "300000"; //Timer configuration
this.fakemgrstring = "windows error 32"; //Deceptive error message
this.encryptedftphost = "DAsa*********************************************wLtBAs"; //FTP host
this.encryptedftpuser = "wY0Lee************************************C1PY="; //FTP user name
this.encryptedftppass = "3/BxGI**********************************gtq6ug="; //FTP password
this.encryptedphplink = "bFQooC****************************qwc/L28DWULUK6g=="; //PHP link
this.useemail = "noemail"; //Whether to use email to upload information
this.useftp = "noftp"; //Whether to use FTP to upload information
this.usephp = "yesphp"; //Whether to use PHP to upload information
this.delaytime = "0"; //Delay startup time
this.clearie = "clearie"; //Whether to clear the browsing history from Internet Explorer
this.clearff = "clearff"; //Whether to clear the browsing history from Firefox
this.binder = "bindfiles"; //Whether to bind other files
this.downloader = "downloadfiles"; //Whether to download files
this.websitevisitor = "websitevisitor"; //Access websites
this.websiteblocker = "websiteblocker"; //Block websites
this.notify = "notify";
this.DisableSSL = "DisableSSL"; //Whether to use SSL for encrypted transmission
this.fakerror = "fakeerror"; //Whether to display deceptive error messages
this.startup = "startup"; //Whether to configure automatic startup
this.screeny = "screeny"; //Whether to monitor screens
this.clip = "clip"; //Whether to upload clipboard data
this.TaskManager = "TaskManager"; //Whether to disable the task manager
this.logger = "logger"; //Whether to enable logging
this.stealers = "stealers"; //Whether to steal passwords
this.melt = "melt";
this.reg = "reg"; //Whether to disable registry
this.cmd = "cmd"; //Whether to disable cmd
this.misconfig = "msconfig"; //Whether to disable msconfig (view system startup items)
this.spreaders = "spreaders"; //Whether to spread malware via the USB flash drive
this.steam = "steam"; //Whether to terminate the Steam process and delete the configuration file
this.screenynumber = 1;
this.Minecraftt = 120000;
this.Pinsst = 140000;
this.Bitcoinst = 180000;
this.path = Path.GetTempPath(); //Obtain the temporary file directory
this.meltLocation = Environment.GetFolderPath(Environment.SpecialFolder.ApplicationData) + "\\Windows Update.exe"; //Path of the installation file
this.appname = Path.GetFileName(Application.ExecutablePath); //Obtain the current file name
this.CLog = string.Empty;
this.CH = new Clipboard();
this.LHeader = "----["; //Left label indicating the start of a log
this.RHeader = "]----"; //Right label indicating the end of a log
this.UseCaps = false;
this.BackSpace = false;
this.KeyboardHandle = (IntPtr)0;
this.LastCheckedForegroundTitle = "";
this.callback = null;
this.mem = Resources.CMemoryExecute;
this.User = WindowsIdentity.GetCurrent().Name.Split(new char[]
{
'\\'
})[1];
this.InitializeComponent();
}
Network Communication
- Malware-related domains are listed as follows:
- Indyproject.org
- Studiousb.com
- copylines.biz
- Glazeautocaree.com
- Brokelimiteds.in
- meedlifespeed.com
- 468213579.com
- 468213579.com
- 357912468.com
- aboranian.com
- apple-recovery.us
- security-block.com
- com-wn.in
- f444c4f547116bfd052461b0b3ab1bc2b445a.com
- deluxepharmacy.net
- katynew.pw
- Mercadojs.com
- Information can be uploaded by any of the following means:
- HTTP PHP
- FTP
- SMTP
Attack Tracing
HawkEye is written or sold by a person who compiles another piece of malware that was previously tracked by NSFOCUS’s security team. The following figure shows the source tree.
In the sample, we found the user name and password (encrypted) of the attacker. An analysis of the email content and the signature of the sample enabled us to locate the website of the sample author or seller. Through a website security test, we discovered a directory listing vulnerability in the website and obtained the administrator name of the server. Via Google, we then found a trojan sale video on YouTube and spotted a suspicious domain name. The author or seller manages trojans via this website.
Then a suspicious Gmail address came to our notice. Using the account information and the information collected previously, we successfully logged in to a Twitter account.
A further look into the account disclosed the following email:
Analyzing the Gmail account, we determined that it belonged to the user who published the malware sale video on YouTube.
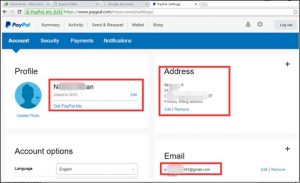
This Gmail account was then found to be associated with a PayPal account.
Finally, two sellers were identified.
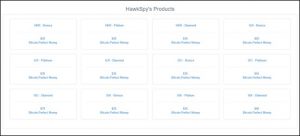
The following figure shows prices of HawkSpy products.
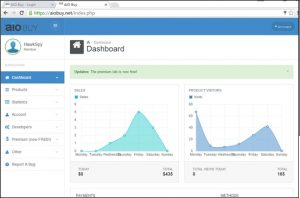
The following figure shows the sales volume of these products in that week.
Solution
NSFOCUS Detection Services
NSFOCUS engineers provide onsite detection services.
NSFOCUS Solution for Removing Trojans
- Short-term service: NSFOCUS engineers provide the onsite trojan backdoor removal service (manual services + NIPS + TAC) to immediately eliminate risk points within the network and control the impact, and will provide an analysis report after the event.
- Mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services (NIPS + TAC + manual services) to eradicate risks and ensure that the event does not recur.
- Long-term service: NSFOCUS provides solutions specific to risks in the fund industry (threat intelligence + attack traceback + professional security service).