The malware uses the following icons to disguise its EXE files as PDF and RAR executables. The attacker then sends malicious code to the target via email, tricking the victim into executing it. In this way, an attack is successfully launched via social engineering.
Date of Release: April 14, 2016
Sample Information
| MD5 | File |
| A92F13F3A1B3B39833D3CC336301B713 | EXE file masquerading as a PDF file |
| AF2379CC4D607A45AC44D62135FB7015 | EXE file masquerading as a RAR file |
Behavior Analysis
The malware uses the following icons to disguise its EXE files as PDF and RAR executables. The attacker then sends malicious code to the target via email, tricking the victim into executing it. In this way, an attack is successfully launched via social engineering.
![]()
After being executed, the trojan internally calls a system hardware error, which causes the system to reboot, a condition known as a Blue Screen of Death (BSOD).

After the system is rebooted, the user is prompted to perform a disk check, which is actually for the purpose of encrypting the disk.

After completing the encryption, Petya displays an animated image of a flashing red and white skull drawn in ASCII characters.

If the user presses any key as instructed, a ransom message is displayed on the screen, demanding the user to pay a specified amount of Bitcoins for the decryption of the encrypted disk.

Use DiskGenius to check the encrypted disk. It turns out that partitions on the disk rather than the entire disk are encrypted.
Executive Summary
The master file of the trojan is a shell program so that malicious code cannot be statically detected. During execution, more memory space will be requested to drop the main functional code, which will be written into the boot location of the physical disk, thus changing the Master Boot Record (MBR). Finally, the system is forced to reboot. The encryption process is as follows:

What Is MBR?
The MBR is a special type of boot sector at the very beginning of a fixed disk or removable drive for use with IBM PC-compatible systems. Its specific location on the disk is cylinder 0, head 0, and sector 1 (each sector contains 512 bytes).
The MBR holds the information on how the logical partitions, containing file systems, are organized on the medium. The MBR also contains executable code to function as a loader for the installed operating system — usually by passing control over to the loader’s second stage, or in conjunction with each partition’s volume boot record (VBR). This MBR code is usually referred to as a boot loader.
The MBR structure is as follows:
| Byte Offset (Hexadecimal) | Size (Bytes) | Description |
| 0x00-0x1BD | 446 | Bootstrap code area |
| 0x1BE-0x1CD | 16 | Partition entry 1 |
| 0x1CE-0x1DD | 16 | Partition entry 2 |
| 0x1DE-0x1ED | 16 | Partition entry 3 |
| 0x1EE-0x1FD | 16 | Partition entry 4 |
| 0x1FE-0x1FF | 2 | Boot signature 0xAA55 or 0x55AA |
Behavior Analysis
- Behaviors of the sample file

Encrypting 0x22 sectors

Replacing MBR data

Writing decryption code to disk sectors

Writing three pieces of encryption/decryption-related data to the disk
The data in red frames is a 32-byte encrypted key; the data in the blue frame indicates the unique device ID; the data in the violet frame is the decryption string provided for the user to type at the ransom website.

Calling a function to display a hardware error
- MBR code

Malicious MBR code
At 0x7C21, the main functional code of the malware is loaded to memory 0x8000. Then at 0x7C30, it skips to the malicious code for encryption and decryption operations.
- Encryption code

Location of the encrypted key (0x20) data in memory
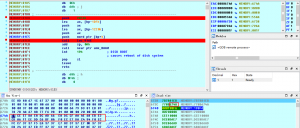
Encryption function
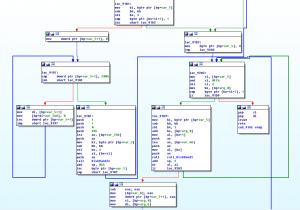
Partial handling procedure of the encryption function
- Decryption code
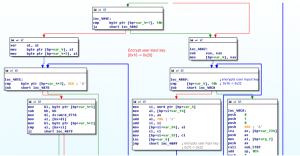
Procedure of encrypting the user-supplied key
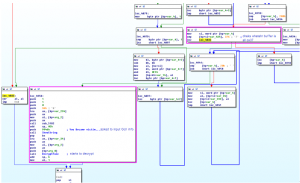
Procedure of checking the authentication buffer and decrypting the encrypted hard disk
Debugging Method
The malware uses MBR for attacks. Considering the importance of MBR, debugging should not be carried out at the user layer. Instead, it is advisable to perform it on a virtual machine. Here we combine IDA with VMware for debugging.
The GDB stub provided by VMware consists of two parts: one to support x86 and the other to support x64. When the virtual CPU on VMware in debugging state is running in 16/32-bit mode, the GDB stub supported by the 32-bit mode takes effect and will listen on port 8832. When the virtual CPU on VMware in debugging state is running in long mode, the GDB stub supported by the 64-bit mode takes effect and will listen on port 8864. Add the following code to the master configuration file (.vmx) of the virtual machine:
debugStub.listen.guest32.remote = “TRUE”
debugStub.listen.guest64.remote = ”TRUE”
monitor.debugOnStartGuest32 = “TRUE”
debugStub.hideBreakpoints = “TRUE”
bios.bootDelay = “3000”
After the virtual machine is started, IDA uses the remote GDB debugger to perform debugging, with parameters configured as follows.
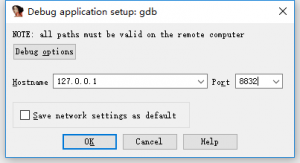
Check Result
| Antivirus Software | Check Result |
| MicroWorld-eScan | Trojan.GenericKD.3132766 |
| nProtect | Trojan/W32.Petr.806912 |
| CAT-QuickHeal | Trojan-Ransom.Petr.r5 |
| McAfee | RDN/Ransom |
| VIPRE | Trojan.Win32.Generic!BT |
| K7AntiVirus | Trojan (004e1c831) |
| BitDefender | Trojan.GenericKD.3132766 |
| K7GW | Trojan (004e1c831) |
| Cyren | W32/Petya.XMFF-8835 |
| Symantec | Trojan.Cryptolocker.AJ |
| ESET-NOD32 | Win32/Diskcoder.Petya.A |
| TrendMicro-HouseCall | Ransom_PETYA.E |
| Kaspersky | Trojan-Ransom.Win32.Petr.l |
| NANO-Antivirus | Trojan.Win32.AD.ebjjem |
| ViRobot | Trojan.Win32.S.Petya.806912[h] |
| AegisLab | Troj.Ransom.W32!c |
| Rising | PE:Malware.Generic/QRS!1.9E2D [F] |
| Ad-Aware | Trojan.GenericKD.3132766 |
| Sophos | Troj/Petya-C |
| F-Secure | Trojan.GenericKD.3132766 |
| DrWeb | Trojan.MBRlock.245 |
| Zillya | Trojan.Petr.Win32.5 |
| TrendMicro | Ransom_PETYA.E |
| McAfee-GW-Edition | BehavesLike.Win32.Downloader.bh |
| Emsisoft | Trojan-Ransom.Win32.Petya (A) |
| F-Prot | W32/Petya.G |
| Avira | TR/AD.Petya.Y.hhcl |
| Microsoft | Ransom:Win32/Petya |
| Arcabit | Trojan.Generic.D2FCD5E |
| SUPERAntiSpyware | Ransom.Petya/Variant |
| GData | Trojan.GenericKD.3132766 |
| ALYac | Trojan.GenericKD.3132766 |
| AVware | Trojan.Win32.Generic!BT |
| Panda | Trj/CryptoPetya.A |
| Tencent | Win32.Trojan.Petr.Llrb |
| Yandex | Trojan.Petr! |
| Ikarus | Trojan-Ransom.PetYa |
| AVG | Ransomer.LBN |
| Qihoo-360 | Trojan.Generic |
Check result of various antivirus software (check time: 2016-04-12 07:05:29)
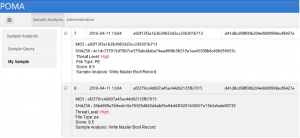
Check result of NSFOCUS POMA
Data Recovery
- Obtain the PetyaRansomware system recovery CD from NSFOCUS.
- Boot the system from the CD-ROM drive or from a USB flash drive that contains the system recovery program.
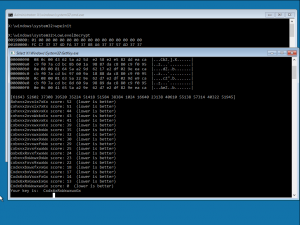
3. Record the key prompted by the program, reboot the host from the original hard disk drive, and then type the recorded key.
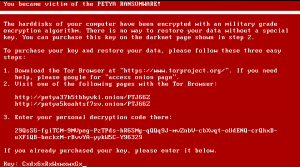
4. The system starts to decrypt the hard disk.
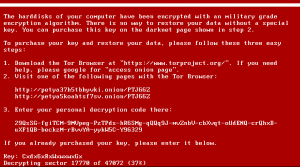
5. The system prompts users to reboot the computer after the decryption is complete.
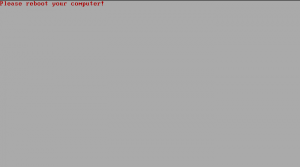
6. The system can be accessed after the reboot.
Solution
- For individual users:
- Install antivirus software and update it to the latest version.
- Run NSFOCUS’s PetyaRansomware system recovery software.
- For enterprise users:
- Install endpoint security software and update it to the latest version.
- Adopt NSFOCUS’s integrated solution of TAC + IPS + NGFW.
- Use NSFOCUS’s secure mail gateway.
- Run NSFOCUS’s PetyaRansomware system recovery software.
声 明
本安全公告仅用来描述可能存在的安全问题,绿盟科技不为此安全公告提供任何保证或承诺。由于传播、利用此安全公告所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,绿盟科技以及安全公告作者不为此承担任何责任。绿盟科技拥有对此安全公告的修改和解释权。如欲转载或传播此安全公告,必须保证此安全公告的完整性,包括版权声明等全部内容。未经绿盟科技允许,不得任意修改或者增减此安全公告内容,不得以任何方式将其用于商业目的。
关于绿盟科技
北京神州绿盟信息安全科技股份有限公司(简称绿盟科技)成立于2000年4月,总部位于北京。在国内外设有30多个分支机构,为政府、运营商、金融、能源、互联网以及教育、医疗等行业用户,提供具有核心竞争力的安全产品及解决方案,帮助客户实现业务的安全顺畅运行。
基于多年的安全攻防研究,绿盟科技在网络及终端安全、互联网基础安全、合规及安全管理等领域,为客户提供入侵检测/防护、抗拒绝服务攻击、远程安全评估以及Web安全防护等产品以及专业安全服务。
北京神州绿盟信息安全科技股份有限公司于2014年1月29日起在深圳证券交易所创业板上市交易,股票简称:绿盟科技,股票代码:300369。
如果您需要了解更多内容,可以
加入QQ群:570982169
直接询问:010-68438880
