Since May 12, 2017, WannaCry has spread on a massive scale around the world, causing significant impacts. Therefore, security firms start to analyze and prevent the spread of this ransomware. Technical personnel of NSFOCUS also analyzed the sample immediately and released a detailed analysis report.
However, we cannot help wondering who created WannaCry? Who is the attacker? What is the purpose? Here, we need to use the basic method adopted by Dalwin for exploring the origin of species: observing, representing, comparing and analyzing. Last Saturday, through NSFOCUS Threat Intelligence (NTI), we intercepted two variants of WannaCry 2.0. Our comparative analysis reveals that there are no essential changes and our protection measures remain effective. In the subsequent traceback process, we find that a sample detected in February 2017 was very similar to the sample captured in March. A foreign security team, through analysis, concluded that the sample detected in February 2017 and the Lazarus APT group’s sample disclosed in February 2015 were very much alike in code.
Inspired by this finding, NSFOCUS security team delves into samples. After a comparative analysis of the Lazarus APT group’s sample disclosed in February 2015, Wcry samples respectively detected in February and March 2017, and WannaCry sample, we conclude that WannaCry is version 2.0 of Wcry.
WannaCry 2.0 Snafu
By analyzing WannaCry, technical personnel finds a kill switch (www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com). Once the worm is running on a victim’s machine, it tries to connect to the domain iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com. If the connection succeeds, the worm exits and will not encrypt files. Otherwise, it will start spreading and encrypting files. This domain name is in plaintext and can be changed. This is why WannaCry 2.0 arises. On May 13, Kaspersky confirmed that they had seen samples that did not have the kill switch.

Statement from Kaspersky
The statement was quickly deleted and technical personnel from Kaspersky also confirmed “No version without a kill-switch yet” via messages. However, the snafu has been totally misunderstood and got about, and some teams call files dropped by WannaCry and subsequent variants WannaCry 2.0.
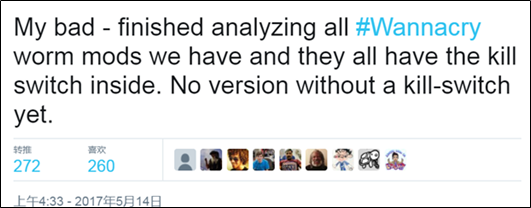
Clarification message from Kaspersky
Even if WannaCry 2.0 is a snafu, technical personnel of NSFOCUS, after an in-depth analysis, found that the decryptor of the Wcry sample detected and delivered in March 2017 and that of the ransomware that broke out on May 12 were of the same origin. After infecting a host, both samples drop a decryptor file, which is almost the same.
Continuing our traceback on WannaCry, we found a sample detected in February 2017 that was very similar to the sample captured in March.
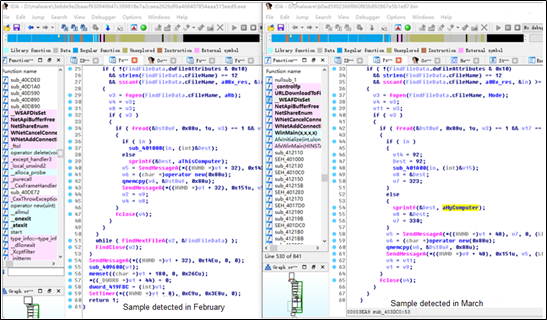
A foreign security team, through analysis, concluded that the sample detected in February 2017 and the Lazarus APT group’s sample disclosed in February 2015 were very much alike in code.


he Lazarus APT group is believed to have been involved in the “wiper” malware attack against the US-based Sony Pictures Entertainment, the attack against the Bangladesh Bank, and the DarkSeoul operation.
Ransomware Analysis
Sample Information
| Decryptor Version and Name of the Ransomware | MD5 | File Size |
| 1.0, Wcry | b0ad5902366f860f85b892867e5b1e87 | 237,568 bytes |
| 2.0, WannaCry (u.wnry) | 7bf2b57f2a205768755c07f238fb32cc | 245,760 bytes |
Note: u.wnry comes after the execution of the tasksche.exe file dropped by WannaCry. For details, see the Analysis Report on the WannaCry Sample published by NSFOCUS.
Comparative Analysis
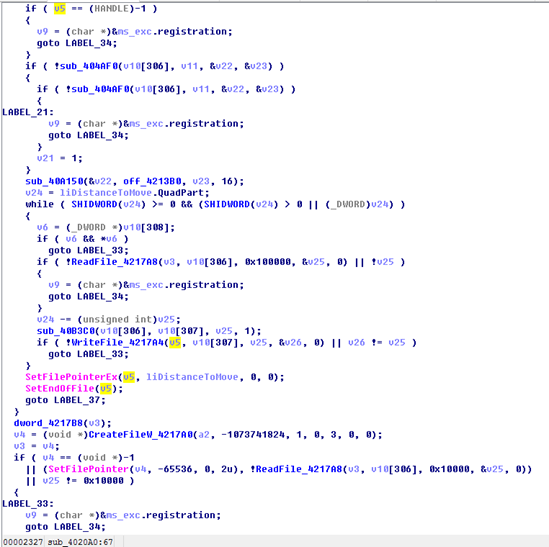
As shown in the following figure, the workflow of the decryptor of the two pieces of ransomware is exactly the same.
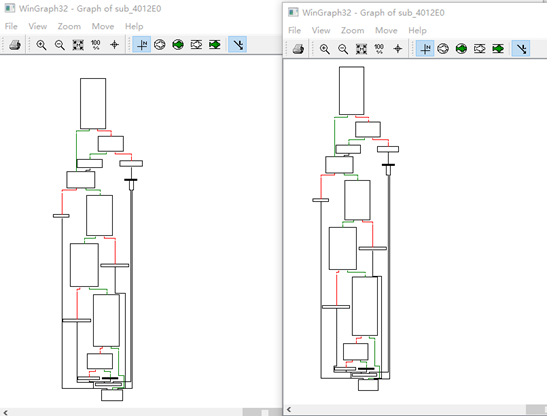
Flow chart of Wcry Flow chart of u.wnry of WannaCry
Also, the decryptor of the two pieces of ransomware is almost the same in the decrypting process, as shown in the following figures.
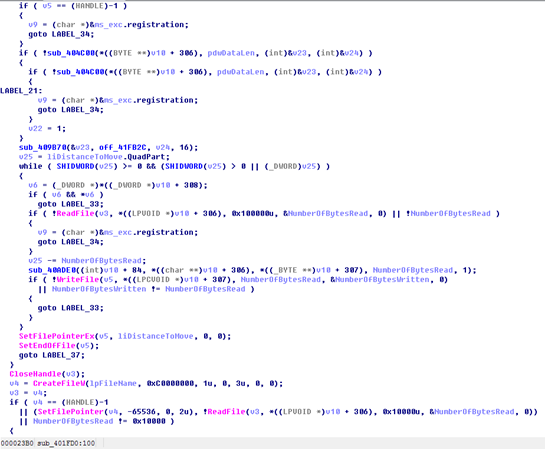
The preceding figure shows the decrypting process of Wcry and the following shows that of u.wnry of WannaCry.
A slight difference between the two is that Wcry directly imports functions to be called into the import list, but u.wnry of WannaCry saves such functions as strings and then dynamically obtains them and puts them in global variables for use.
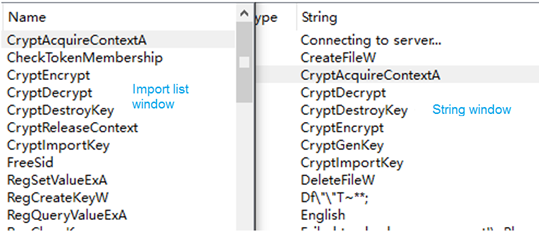
Import list of Wcry String list of u.wnry of WannaCry
After decrypting functions are called, the decryptor of the two pieces of ransomware will undergo almost the same procedure of operation.
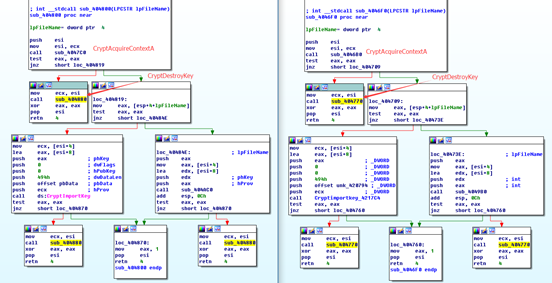
Wcry u.wnry of WannaCry
In addition, the sample provides hardcoded information about the version.
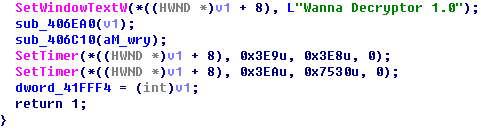
Hardcoded version information of Wcry
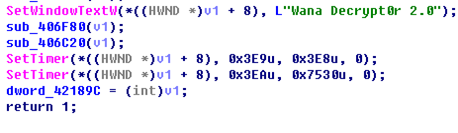
Hardcoded version information of u.wnry of WannaCry
These signs indicate that Wcry is the first version of this ransomware and exists only as a decryptor without the capability of proactive propagation. Based on the original ransomware, WannaCry leverages a Microsoft SMB vulnerability and the DOUBLEPULSAR backdoor to gain the power of fast propagation, making itself a 2.0 version of the ransomware.
Note to the Variant Analysis
The kill switch exists in plaintext in the WannaCry sample, which facilitates variant creation. The 2.0 version, as claimed by some people, is WannaCry itself or variants of WannaCry with the kill switch modified. For details, see the Preliminary Analysis Report of WannaCry Variants published by NSFOCUS. This report mentions that the so-called 2.0 version is nothing but variants of the original WannaCry with the kill switch and redirection function modified. These variants, together with WannaCry, are in fact the second version of Wcry.
Sum-Up
Rumor had it that WannaCry had evolved to the second version, which, however, proves to be a false alarm later. These seemingly new versions of ransomware are just variants of WannaCry or WannaCry itself. However, after analysis, we found that the decryptor dropped by WannaCry was almost the same as the ransomware Wcry detected in March 2017. Therefore, WannaCry can be taken as the second version of Wcry. It has a propagation framework: a Microsoft SMB vulnerability (MS17-010) and the DOUBLEPULSAR backdoor. With this framework, WannaCry has gained the power of fast propagation and for this reason is mistakenly called WannaCry 2.0.
Statement
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete any information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.
