1 Security Event Investigation and Threat Intelligence
Over a year ago, I wrote to put forward three suggestions:
- Set up a system for security event disclosure and case analysis.
- Clearly delineate security disclosure responsibilities.
- Establish a security data and response platform. These measures will gradually promote best security practices at the strategic level, in terms of effectiveness and accuracy and even correctness.
This document is a companion to the previous one.
Defending against advanced threats rests on threat intelligence which is so important as to get great attention from the management and industry. At present, there are numerous meetings, forums, and reports on threat intelligence. In addition, subscribing to threat intelligence has become common practice and a wide range of R&D activities are carried out. All of these obviously demonstrate an inspiring development. However, it remains a great challenge for the industry to work out how to lay a solid foundation for an ecological system of threat intelligence, including intelligence collection, analysis, accumulation, sharing, and application.
Threat intelligence is sourced from three aspects across the industry:
- Transactions such as purchases shared within the industry and alliances.
- Operating procedure of the security protection system.
- Independent research of researchers.
- Security event investigation and tracking activities.
The last one, in particular, presents live, continuous, and verifiable sources for threat intelligence, which is essential to the entire threat intelligence ecology. Extensive event analysis that covers a broad range of industries and regions, shared threat intelligence, and best practices will be powerful and effective weapons against threats.
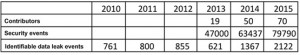
Let’s look at an example of Verizon, an American carrier. Verizon has been releasing annual data security situation reports for many years. Initially, only Verizon collected data for such reports, but currently a total of over 70 organizations contribute data, including United States Department of Homeland Security (DHS), US-CERT, Secret Service, and many security vendors and service providers. Security events that are covered by such reports have been increasing steadily since 2013, with nearly 80,000 in 2015. Besides, identifiable data leak events included in annual reports increase from 761 in 2010 to 2122 in 2015.
Figure 1 Accumulation of data included in Data Breach Investigations Report (DBIR)
The preceding table shows what the American counterparts have done in threat intelligence is a good reference to us.
As the Cyber Security Law and Amendment to Criminal Law are released and come into force, those who cause serious cyber security events will be held responsible legally. The Amendment to Criminal Law requires that the following be added to Article 286 in the Criminal Law: Internet service providers that cause serious consequences arising from disclosure of user information, will be sentenced to fixed-term imprisonment of not more than three years, criminal detention, or control, in addition to fines; or are to be fined. Apparently, the new legislation will make cyber security events treated more severely and encourage owners and operators of information systems to pay more attention to and increase investment in cyber security.
Frankly speaking, hushing security events up is very common within the industry. As the new cyber security legislation further increases the price to be paid for security events that are reported and revealed, it is much more difficult to effectively investigate and analyze security events, especially high-quality analysis that is made by professionally and can be shared, in cases where incentives or constrains are absent. This undermines the foundation for sustainable development of the threat intelligence ecology.
2. “Living Loop” and “Dead Loop”
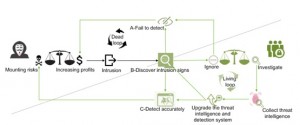
Cyber attackers and security teams fight each other all the time. When the strength of one side gains momentum, the other side may lie low. After an attack is initiated, a security protection system may (1) fail to detect it; (2) discover intrusion signs; or (3) accurately detect the attack.
In the first case, the attacker easily achieves his or her purpose of gaining profits and therefore is eager for more profits. At the same time, the attacker obtains more “intelligence” about the defending side, preparing himself or herself for further attacks. In the second case, the protection system detects some symptoms of the attack. Subsequently, the defending side may ignore such symptoms, as is described in the first case. Alternatively, the defending side may locate the source by tracking the attack, and then upgrade the threat intelligence and detection system for accurate detection and prevention of this attack, thus evolving into the third case. In the third case, the attack is blocked and ends up in a wild-goose chase. In addition, the source is probably located and the attacker may be brought to justice. During this process, the defending side, thanks to its investigation and forensics, enriches its threat intelligence database, having a clearer idea of the attack resources, tactics, techniques, and methods. This makes it more difficult for attackers to invent new attack methods and tools and more possible for attacks to be detected. As a result, attackers may think twice before attacks or even give up attacks for good. The following figure illustrates the “living loop” and “dead loop”.
Figure 2 “Living loop” and “dead loop” in a cyber attack
Apparently, the first case and ignoring the attack in the second case both lead to increased profits for attackers, more frequent attacks, and more adverse cyber security environments, thus constituting a “dead loop”. The third case and the investigation in the second case give rise to a reinforced protection capability and an increased possibility of locating the attack source, making quitting the only option for the attacker. As a result, the cyber security environment will be clean under effective governance. This is what we call a “living loop”. Figure 2 shows that the most clear-cut divide between the “living loop” and “dead loop” is the detection of symptoms of an attack event, at which the defending side may choose to ignore the symptoms or initiate an investigation, depending on its capabilities, resources, or the priority given to the input-output ratio.
3. Ignore or Investigate?
There is no existence of complete security, which is universally acknowledged in the security industry. This means that “accidents” inevitably happen here or there in a network owing to defects in the protection system. These “accidents” actually exist, but some may be perceived while some may not, some may be ignored while some may be investigated, and some may be analyzed for the root cause while some may not.
The scenes of accidents usually convey a lot of information about attackers. Investigating such a scene calls for a huge input of resources, with the output of root cause analysis, attacker profile information, attack techniques, tactics, and methods, and the cause of protection failures. The input of resources is deeply felt. In contrast, the preceding output and the value of such output are quite uncertain for the small- and medium-sized unprofessional security operations teams. Therefore, small- and medium-sized enterprises with limited security capacities are not capable enough and some large enterprises capable enough are not willing to conduct the investigation. This is one of the phenomena of cyber security protection.
The professional division of duties is conducive to the resolution of the “incapability” issue. The issue of “unwillingness” can be resolved by appropriately rewarding those who collect more threat intelligence following root cause analysis instead of punishing those with security issues.
4. Threat Intelligence and Cyber Insurance
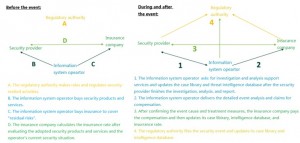
By reference to rules governing traffic accidents and insurance, the introduction of the “insurance” role in the cyber security ecosystem will help break the “externality” and “lemon market” traps. The United States has made great progress in cyber insurance, with at least 50 insurance companies providing cyber insurance products by 2014. 24% of American businesses has bought the cyber insurance, all at a cost of $2 billion. Figure 3 shows the eco-map with the introduction of the “insurance” role drawn by the author. It mainly presents two situations: before the security event, and during and after the security event.
Figure 3 Threat intelligence and cyber insurance
The regulatory authority makes corresponding rules. An information system operator independently develops security products and services or buys such products and services from a professional security provider to strengthen the protection system. Then the operator buys the cyber insurance to cover all other “residual risks”. The insurance company assesses the operator’s current security situation and the “reliability” of the security products and services adopted by the operator before calculating the “insurance rate”. In the case of a security event, the information system operator asks the professional service provider to investigate on and analyze the event, and then submits the detailed event information and analysis result to the insurance company for compensation. After confirming the event cause and treatment measures, the insurance company pays the compensation and updates its case library, threat intelligence database, and insurance rate accordingly.
Through an alternative form of “redemption”, the information system operator becomes willing to “investigate” rather than “ignore” security events; the professional security provider can obtain the first-hand “threat intelligence” for investigation and forensics; and the “effectiveness” of security products and services is objectively verified by the security event analysis and reflected by the “insurance rate”. In this way, the ecological security protection system can defend against security threats more effectively.
5. Summary
Sun Zi once said, “Know the enemy and know yourself, and you can fight a hundred battles with no danger of defeat.” Threat intelligence is the key for you to “know the enemy and know yourself” in the network attack and defense field, while the continuous accumulation of security event investigation and analysis is the most important springhead of threat intelligence.
Undoubtedly, it is very important to, by legislation, increase the “punishment” for security events and improve the cyber security awareness of information system owners and operators. However, as cyber security events are inevitable, we should encourage the investigation and forensics and recognize the efficient analysis processes and results. This can help improve the current situation where, in Chain, the basic data of cyber security is deficient, and relevant standards and best practices lack data support and verification.
To achieve this goal, it is necessary to design and build the corresponding regulatory and ecological environment, for example, introducing the cyber insurance role to realize case accumulation and sustainable development of threat intelligence through cyber security event claims.