On November 30, 2016, Mozilla Firefox released an emergency update on its official website to fix a vulnerability assigned CVE-2016-9079.
This vulnerability is a use-after-free vulnerability in the SVG animation module. When a user uses Firefox to browse a page that contains malicious JavaScript and SVG code, an attacker could exploit this vulnerability to execute code remotely on the user’s machine. Vulnerable platforms include Windows, Mac OS, and Linux. For details, click the following links:
https://www.mozilla.org/en-US/security/advisories/mfsa2016-92/
https://blog.mozilla.org/security/2016/11/30/fixing-an-svg-animation-vulnerability/
Vulnerability Analysis
This vulnerability is a use-after-free vulnerability that exists in the SVG animation module.
According to the exposed vulnerable code, this vulnerability affects all platforms on which Firefox runs, including Windows, Linux, and Mac OS.
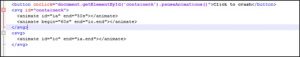
This vulnerability resides in the nsSMILTimeContainer::NotifyTimeChange() function in the SVG animation module. The following is simple example code for triggering this vulnerability:
However, the attack code targets Windows operating systems only. Once such an attack succeeds, the host name and MAC address of the victim will be sent to the remote server.
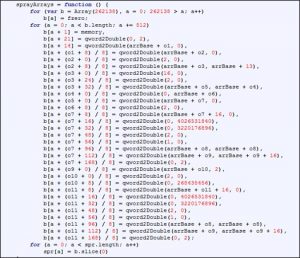
With the heap spraying technique, an attacker could assign memory and fill it with a large number of predefined directives to bypass address space layout randomization (ASLR). See the following figure.
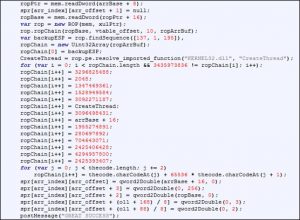
Then the attacker executes shell code by bypassing data execution prevention (DEP) with a dynamically crafted return-oriented programming (ROP) chain.
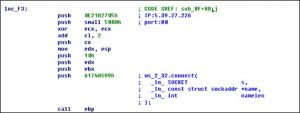
The shell code is executed to retrieve the host name and MAC address of the victim machine report them to a remote server (5.39.27.226).
At last, the attacker sends an HTTP request that contains the host name and MAC address of the victim machine.
Affected Versions
- Firefox version < 50.0.2
- Firefox ESR version < 45.5.1
- Thunderbird version < 45.5.1
Unaffected Versions
- Firefox 50.0.2
- Firefox ESR 45.5.1
- Thunderbird 45.5.1
Vendor Solutions
The vendor has released an update. Users are advised to upgrade Firefox to the latest version. Users can select the auto update option in the Firefox browser to enable the auto update function or manually download the latest version from one of the following links and install it:
- Firefox 50.0.2
https://www.mozilla.org/en-US/firefox/50.0.2/releasenotes/
- Firefox ESR 45.5.1
https://www.mozilla.org/en-US/firefox/organizations/all/
- Thunderbird 45.5.1
https://www.mozilla.org/en-US/thunderbird/
Recommended Solutions
- Products
- Use NSFOCUS’s protection product (IPS, IDS, or NF) to protect against the exploitation of the vulnerability.
- Authorize NSFOCUS RSAS to check services.
(2) Services
- Short-term service: Contact NSFOCUS engineers for onsite handling (penetration testing + emergency response) to ensure that risk points are immediately eliminated in the network and the event impact is minimized. After the handling, an event analysis report is provided.
- Mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services to eradicate risks and prevent events from recurring.
- Long-term service: NSFOCUS provides industry-specific risk mitigation solutions (threat intelligence + attack traceback + professional security service).
Statement
==========
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
============
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.