Ukrenergo, a major energy provider in Ukraine, experienced a power failure on the night of December 17, 2016, which involved the automatic control system of the “North” substation in New Petrivtsi close to Kiev. The blackout affected the northern part of Kiev, the country’s capital, and surrounding areas.
Overview
Shortly after the incident, Ukrenergo engineers switched devices to manual mode and started restoring power in about 30 minutes. Power was fully restored 75 minutes after the blackout.
On the morning of December 18, 2016, Ukrenergo Director Vsevolod Kovalchuk explained the incident in a post on Facebook and said that this outage may be caused by a device fault or cyber attack.
The following is a timeline of activities carried out by NSFOCUS’s security team in the wake of this incident.

Figure 1 Responses made by NSFOCUS’s security team to this incident
Historical Attacks on Ukrenergo

Figure 2 Attacks on the Ukrainian power grid
Figure 2 shows attacks on the Ukrainian power grid in recent years. NSFOCUS’s security team, through analysis of the malware code, determined that this incident was initiated by Telebots, which is believed to be associated with BlackEnergy.
What Is an Electric Power System?
An electric power system is a network of electrical components deployed to generate, supply, transfer, transform, and use electric power, as shown in Figure 3. In the figure, step-up transformers are used to increase voltage before transmitting electrical energy over long distances through wires. Step-down transformers are used to decrease the supply voltage to a level suitable for use by regional power grids or end users. The distribution substation transfers power from the power grid to various users. Throughout the power system, operations in almost every stage rely on computer technology, such as the computer system used by the scheduling and control center of power grids at various levels and the computer-aided monitoring system at every substation.
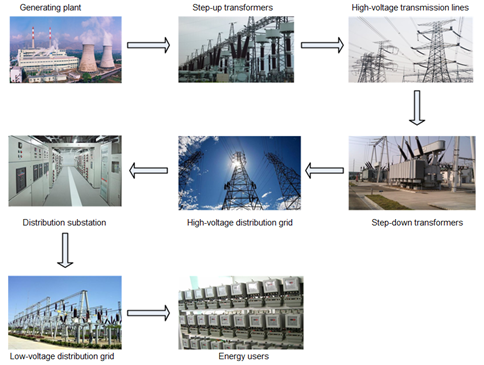
Figure 3 Components of an electric power system
Figure 4 shows the structure of a transformer substation in China.
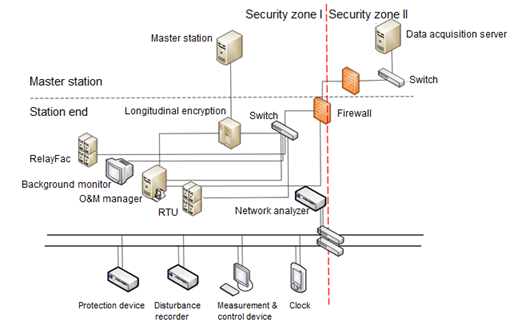
Figure 4 Structure of a transformer substation in China
- Longitudinal encryption: encrypts channel data transmitted from the substation to the scheduling center.
- RTU: sends information within the substation to the remote scheduling center.
- Network analyzer: records communication packets of the substation’s internal network.
Figure 5 shows the structure of transformer substations in other countries than China.
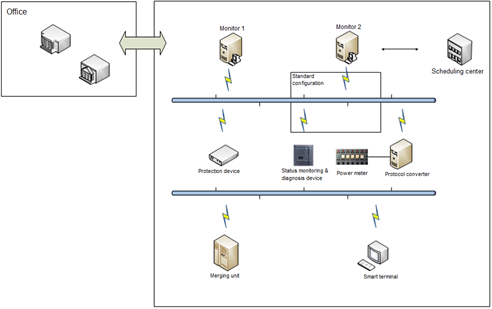
Figure 5 Structure of transformer substations in other countries than China
- Protection device: implements appropriate protection and control logic for collected voltage, current, and Boolean signals of primary devices.
- Merging unit: collects voltage and current signals of primary devices.
- Smart terminal: collects Boolean signals of primary devices and implements switch control commands issued by the protection device.
- Status monitoring and diagnosis device: a type of additional field devices at the substation for monitoring purposes.
- Protocol converter: converts protocols so that devices using different protocols can communicate with one another.
- Monitor: aggregates and displays field information of the substation.
- Scheduling center: displays and controls centralized control centers of multiple substations in a centralized manner.
Substations in China are different from those in other countries in the following aspects:
- In China, the substation area is divided by firewalls into security zone I and security zone II. The former is a zone for real-time production control, where the running of primary electrical devices can be directly controlled. The latter is a zone for non-real-time control, where the electrical energy metering system, the disturbance recorder, and others are deployed.
- In China, a substation is a totally isolated local area network (LAN) from the public network. In foreign countries, the internal network of a substation can be accessed via an office network acting as a virtual private network (VPN).
Sample Execution Flow
Figure 6 shows the execution flow of the sample.
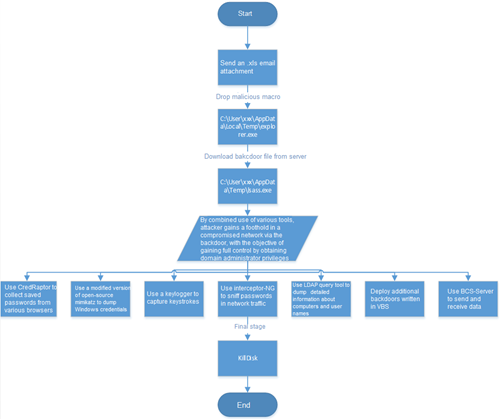
Figure 6 Sample execution flow
Sample Structure
This is a compound sample that consists of multiple files.
| File Type | MD5 | Description |
| XLS | FD0FD58B20B1476E8F67D6A05307E9BC
7D4FC63F2096A485D2DA3DB1150E6D34 |
Drops and executes C:\User\xxx\AppData\Local\Temp\explorer.exe. |
| explorer.exe | 1019C101FC1AE71E5C1687E34F0628E6 | Downloads and executes C:\User\xxx\AppData\Local\Temp\lsass.exe. |
| lsass.exe | 873C7701E16BC68AD7A90886B5D0A3F0
75EE947E31A40AB4B5CDE9F4A767310B 0FCE93CD9BEEEA30A7F0E2A819D2B968 |
This is a remote control trojan, which implements different functions as instructed by the server. |
| KillDisk.exe | B75C869561E014F4D384773427C879A6
FFB1E8BABAECC4A8CB3D763412294469 |
Deletes system logs, clears parts of sector data, and causes the system to crash, unable to be restarted. |
| keylogger.exe | 4919569CD19164C1F123F97C5B44B03B | Records keystrokes. |
| LDAPquery.exe | 76691C58103431624D26F2B8384A57B0 | Makes queries to Active Directory using LDAP. |
| mimikatz.exe | BDE6C0DAC3E594A4A859B490AAAF1217 | Captures system passwords. |
| CredRaptor.exe | 389AE3A4589E355E173E9B077D6F1A0A | Steals user names and passwords in browsers. |
| Intercepter-NG.exe | 5BD6B79A4443AFD27F7ED1FBF66060EA | Intercepts traffic. |
| VBS | 2D7866989D659C1F8AE795E5CAB40BF3
C404B959B51AD0425F1789F03E2C6ECF |
Obtains and executes instructions. |
| telebot.exe | 24313581BBBFFA9A784B48075B525810 | This is a remote control trojan, which implements different functions as instructed. |
……
Attack Location
The sample analysis reveals that this sample connects to two IP addresses and one domain name as follows:
- IP address 188.234.144.11 in Russia.
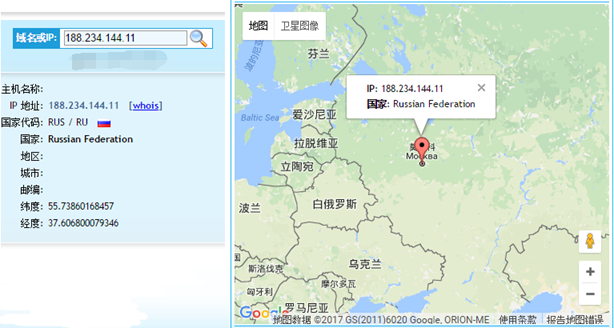
Figure 68 Attack location (1)
- IP address 93.190.137.212 in Holland.
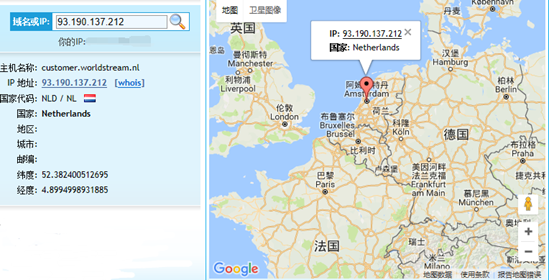
Figure 69 Attack location (2)
- Isass connects to the following domain name:
https://api.telegram.org/bot140192111:AAGSxqO9Xz9meTaG7Ecdh80LGnYXNIbbgp4
Figure 70 shows the domain name parsing result.

Figure 70 Domain name parsing result
Recommended Solution
- NSFOCUS Detection Services
- NSFOCUS engineers provide onsite detection services.
- NSFOCUS provides online cloud detection services. You can visit the following link to apply for the trial use of NSFOCUS Threat Analysis Center (TAC):
https://cloud.nsfocus.com/#/krosa/views/initcdr/productandservice?service_id=1018
- NSFOCUS Solution for Removing Trojans
- Short-term service: NSFOCUS engineers provide the onsite trojan backdoor removal service (manual services + NIPS + TAC + Kingsoft V8+ terminal security system) to ensure that risk points are immediately eliminated in the network and the event impact is minimized. After the handling, an event analysis report is provided.
- Mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services (NIPS + TAC + manual services) to eradicate risks and prevent events from recurring.
- Long-term service: NSFOCUS provides industry-specific risk mitigation solutions (threat intelligence + attack traceback + professional security service).
Conclusion
Like a BlackEnergy attack, this attack takes leverage of a spear phishing email attached with a Microsoft Excel document that contains a malicious macro as an initial infection vector. The difference is that this malicious document does not employ any social engineering methods to entice victims to click the macro start button. This is because when such methods are introduced, whether the attack succeeds entirely depends on the victim clicking it.
After the macro virus runs, the malicious file is dropped to perform malicious functions.
About NSFOCUS
NSFOCUS IB is a wholly owned subsidiary of NSFOCUS, an enterprise application and network security provider, with operations in the Americas, Europe, the Middle East, Southeast Asia and Japan. NSFOCUS IB has a proven track record of combatting the increasingly complex cyber threat landscape through the construction and implementation of multi-layered defense systems. The company’s Intelligent Hybrid Security strategy utilizes both cloud and on-premises security platforms, built on a foundation of real-time global threat intelligence, to provide unified, multi-layer protection from advanced cyber threats.
For more information about NSFOCUS, please visit:
http://www.nsfocusglobal.com.
NSFOCUS, NSFOCUS IB, and NSFOCUS, INC. are trademarks or registered trademarks of NSFOCUS, Inc. All other names and trademarks are property of their respective firms.
