How many people and companies use Cisco routers? You do not need to be a system integration engineer to know the specific figure. Baidu will tell you the answer. Do you panic when knowing that a backdoor targeting Cisco routers may affect most models? An experienced network administrator knows that the firmware of routers is not frequently upgraded. Once an attacker gets the knack of exploiting such backdoors, he or she can use them against those routers in a long time. Are you scared of that?
Infecting Common Models in Four Countries
People often consider it difficult or only theoretically feasible to implant a backdoor into a Cisco router. However, FireEye, a US security company, discovered that backdoors targeting Cisco routers were in the wild stealthily, involving Cisco 1841, 2841, and 3825 routers and other common models. Up to now, at least 14 similar implants have been found to propagate in four countries, namely Ukraine, the Philippines, Mexico, and India.
Replacing Cisco Router Firmware After Login with a Weak Password
SYNful Knock is implemented by implanting malicious code upon modification of the firmware of Cisco routers, similar to the process of infecting a good file with a virus. Attackers need to upload or load this backdoor-infected firmware unto the target router by other means. By far, they have not used any 0-day vulnerabilities to upload the firmware. Instead, they log in to the target router with the default password or a weak password and then upload the backdoor-infected firmware to replace the normal firmware. As long as the router administrator does not upgrade the firmware, attackers can maintain persistent control over the router.
Controlling Routers with the Typical Ploy of Botnets
This backdoor is embedded with a universal backdoor password, with which an attacker can log in to the target router via Telnet or the console. By employing the dynamic module loading technique, it can conveniently load new malicious functional modules whenever it deems necessary (this is a common technique frequently used in botnets under Windows or UNIX, but seldom seen in router backdoors). Each module can be updated, loaded, or deleted via the Hypertext Transfer Protocol (HTTP).
This backdoor program is named “SYNful Knock” maybe because its network command and control (CnC) functionality is triggered via a special TCP SYN packet.
Technical Details
(With no real samples at hand, we provide technical details here by reference to the related report released by FireEye.) This backdoor manages to implant malicious functions by modifying a normal Cisco IOS image as follows:
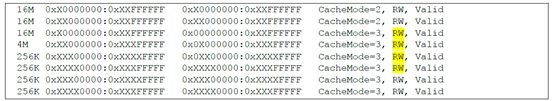
- Modify the translation lookaside buffer (TLB) Read/Write attributes.
In normal IOS images, certain TLBs are Read Only (RO). The backdoor forces all TLB Read and Write attributes to be Read-Write (RW). This is probably done to support the hooking of IOS functions by loaded modules. If TLB attributes are not set to RW, modifications to the cached pages may not be propagated to the original page in memory. The TLB attributes can be examined using the “show platform” command. If all TLB attributes are set to RW (as shown in the following figure), it indicates that the system may be implanted with a malicious backdoor.
- Modify a legitimate IOS function to call and initialize the malware.
It is believed that a function associated with process scheduling was modified to point to the malware hook processing function. After being initialized, the malware executes the original IOS function. This function was chosen because it, after being modified, is called during the IOS boot sequence, and is always called, as long as the IOS boots correctly. In this way, attackers can have the persistent power of control over the system.
- Overwrite legitimate protocol handling functions with malicious code.
To prevent the size of the image from changing, the backdoor overwrites several legitimate IOS functions with its own executable code.
- Overwrite strings referenced by legitimate functions with strings used by the malware.
Also for the purpose of preventing the size of the image from changing, attackers may replace strings referenced by legitimate functions with some strings used in CnC communication. In this way, abnormal results as follows may be returned when some legitimate IOS commands are executed:
Backdoor Password
Attackers implant a universal password into the backdoor-infected image to ensure that they can log in to the system by bypassing restrictions of legitimate passwords. This backdoor password can be entered via the console, Telnet, or elevation to administrative privileges (enable). If the user input is the backdoor password, access is granted; otherwise, the implanted code will pass the credentials on for verification of potentially valid credentials. Currently, the background password has not been set for login via Secure Shell (SSH) or HTTPS.
Network Command and Control
The CnC portion of the implant is modular and allows additional functionality to be loaded into the IOS, which is rarely seen in router backdoors. It can significantly increase the scalability of the malware. Once a router is restarted, all loaded malicious modules will disappear. In this case, attackers need to reload malicious modules.
Attackers enable CnC by sending certain special TCP packets. Even if filters are enabled on the router, these packets can still be received and processed by the malware.
The process of implementing CnC is as follows:
- A uniquely crafted TCP SYN packet is sent to port 80 of the “implanted” router. This is the default port of HTTP services on the router. The difference between the sequence and acknowledgment numbers must be set to 0xC123D. The ACK number does not need to be zero.
- The backdoor responds with a TCP SYN-ACK message acknowledging the first SYN message. This message meets the following conditions:
- The differential between the acknowledgment and sequence numbers is now 0xC123E.
- The following hard-coded TCP options are set: 02 04 05 b4 01 01 04 02 01 03 03 05.
- The urgent pointer is also set to 0x0001, but the urgent flag is not set.
- The backdoor also copies the acknowledgment number from the SYN packet for the sequence number. A typical server usually generates a random sequence number. Therefore, this is not a standard TCP handshake.
- After the 3-way handshake is complete, the controller then sends the following TCP message:
- The PUSH and ACK flags are set.
- From the start of the TCP header, at offset 0x62, the string “text” is written.
- The command data is at offset 0x67 from the TCP header.
The command format is as follows:
The command data portion is XOR encoded with a static key.
- The implant response is encapsulated in the following static HTTP server response. Fortunately, the response from the implant is not XOR encoded or encrypted.
CnC Commands
The backdoor supports five types of CnC commands, including displaying module status, allocating space for an additional module to load, populating the memory allocated for the module, activating a loaded module, and removing a module. A total of 100 additional modules can be loaded.
Each command message starts with 8 bytes. The first four are set to 0 and the second four identifies the message type (0 to 4). The following table describes the meaning of each command type.
If the first four bytes of a message are not 0, they will be deemed as a module ID and the code associated with the module ID is executed.
Protection Methods
Common Protection Methods Adopted by Vendors Outside of China
Generally, security vendors outside of China choose to release patches for users to patch their system. But in practice, this could be rather challenging for the following reasons:
- For small customers with low security requirements, it is extremely difficult to implement.
- For small customers with high security requirements, this can be implemented but the rectification will take a long time.
- For large customers with low security requirements, it is extremely difficult to implement because the implementation involves the shutdown of the entire business chain.
- For large customers with high security requirements, this can be implemented but the rectification will take a long time, involving various departments.
Protection Scheme Recommended by NSFOCUS
NSFOCUS recommends a protection scheme featuring one baseline and three phases. One baseline is to turn extensive risks to sporadic risks. Three phases refer to design and implementation, test run and acceptance, and long-term operation and maintenance (O&M). Each phase involves a lot of details. Following is a brief description of these phases.
Design and Implementation
- Check the quantity of Cisco devices on the system and that of devices from other vendors that need to be managed by a unified policy, preparing for risk identification.
- Strictly separate the management zone and production zone (VLAN technology and firewall) to put risks under control.
- Manage the management zone with a bastion host, on which a password policy is configured, to transfer risks.
- Use comparatively new versions of IOS firmware without compromise of system stability and conduct MD5 checking to mitigate risks.
- Use a network intrusion detection system and protection system (NIDS/NIPS) to detect this backdoor and monitor related network events on a daily basis, thereby implementing risk monitoring.
- The SYNful Knock event goes through three key phases: weak password guessing, backdoor linking, and backdoor command control. NIPS can not only provide protection for each of the three phases but also deliver hierarchical protection.
- With weak password rules properly configured, NIPS can alert users to Telnet weak password events, notify administrators of the existence of weak passwords in the system, and block brute force behaviors.
- Check patterns in the setup process of TCP sessions to block connection requests initiated by the backdoor.
- The backdoor uses CnC or TCP to issue commands for system control. NIPS can detect such commands during traffic checking and then block related traffic. In this way, even if the backdoor is implanted in the system, the backdoor cannot control the system by issuing commands.
- Consider using homegrown devices to avoid risks.
Test Run and Acceptance
- Conduct basic security assessment, including vulnerability scanning, baseline checking, and intranet penetration testing.
- Check all user passwords to remove weak ones.
- Test the availability of intrusion detection daily reports.
Long-Term O&M
- New system delivered for O&M: Regularly maintain the system according to design and implementation specifications.
- Old system:
• Fast handling: Set up a TFTP server to forcibly back up all live IOS images and check the consistency of MD5 values between backed-up IOS images and IOS images downloaded from the official website.
• If an IOS image fails the MD5 check:
For the sake of security, replace the problematic device instead of just deleting the IOS.
Return the problematic device to the vendor or use it as a honeypot.
Overhaul the entire business system to eliminate risk factors.
• Rectify the management zone according to system design standards.
- Analyze intrusion detection daily reports and pay special attention to trojan-related descriptions.
Summary
The technical details provided in this document are based on a technical report from FireEye. The attack process is roughly like this:
- Find a Cisco device that can be logged in to through brute force, social engineering, or use of weak passwords.
- Upload a trojan-implanted IOS image, load the new IOS when the occasion arises, and make these operations untraceable.
- Harden the router to prevent it from being exploited by others.
- Implant malware, such as trojans, and then launch an attack such as JavaScript hijacking.
According to FireEye’s report, the backdoor implanting technique targeting Cisco routers has gradually evolved from theoretical existence to practical application. The backdoor does not just use universal passwords now, but has the capability of remotely loading arbitrary modules with malicious code. Routers are deployed at the ingress and egress of a network, which are very important locations. Once an attacker executes code on a router, he or she can perform any operations on the network traffic passing through the router, without being restricted by the original functions of the router. Therefore, attacks targeting routers tend to cause more damage to the network.
Chinese version: https://blog.nsfocus.net/cisco-router-door-synful-knock-2/