On August 12, 2016, 1n3 disclosed by email an SQL injection vulnerability in jsrpc.php in Zabbix, which can be exploited via the “insert” statement while jsrpc.php is processing the profileIdx2 parameter. This vulnerability is of the same type as the officially announced vulnerability, which is caused by latest.php processing the toggle_ids parameter. The only difference between the two is the location.
An attacker can log in as a guest user or with an authenticated account and then exploit this vulnerability to gain system privileges on the Zabbix server.
- Attack difficulty: low
- Severity level: high
- Official website where the vulnerability is announced:
https://support.zabbix.com/browse/ZBX-11023
What Is Zabbix?
Zabbix is a web-based, open-source, enterprise-class solution providing distributed system monitoring and network monitoring functions.
Zabbix can monitor various network parameters and ensure secure operations of the server system. It provides a flexible notification mechanism, allowing system administrators to rapidly locate and resolve various problems.
Zabbix consists of two parts: Zabbix server and Zabbix agent (optional).
The Zabbix server monitors the status of remote servers and networks by means of SNMP, Zabbix agent, ping, or port monitoring and provides the data collection function. It can run on various platforms, including Linux, Solaris, HP-UX, AIX, FreeBSD, OpenBSD, and OS X.
Affected Versions
- Zabbix 2.0.5, 2.0.13, 2.2.x, 2.4.2, 2.4.5, 2.4.7, 2.4.8, 2.5.0, 3.0.0-3.0.3
Unaffected Versions
- Zabbix 1.8.*, 2.2.14, 3.0.4, 3.2.0
Technical Analysis
Zabbix V3.0.4 has fixed the two SQL injection vulnerabilities and released the following two PoCs:
- /zabbix/jsrpc.php?sid=0bcd4ade648214dc&type=9&method=screen.get×tamp=1471054088083&mode=2&screenid=&groupid=&hostid=0&pageFile=history.php&profileIdx=web.item.graph&profileIdx2=2’3297&updateProfile=true&screenitemid=&period=3600&stime=20170813040734&resourcetype=17&itemids%5B23297%5D=23297&action=showlatest&filter=&filter_task=&mark_color=1
- latest.php?output=ajax&sid=&favobj=toggle&toggle_open_state=1&toggle_ids[]=15385); select * from users where (1=1
The following is the call chain of the first PoC:
Jsrpc.php:413 require_once dirname(__FILE__).'/include/page_footer.php'; include/page_footer.php:40 $result = CProfile::flush(); include/class/user/Cprofile.php:63 function flush() include/class/user/Cprofile.php:277 function insertDB ()
The following is the call chain of the second PoC:
Latest.php:88 CProfile::update('web.latest.toggle_other', $_REQUEST['toggle_open_state'], PROFILE_TYPE_INT, $hostId);
Latest.php:829 require_once dirname(__FILE__).'/include/page_footer.php';
include/page_footer.php:40 $result = CProfile::flush();
include/class/user/Cprofile.php:63 function flush()
include/class/user/Cprofile.php:277 function insertDB ()
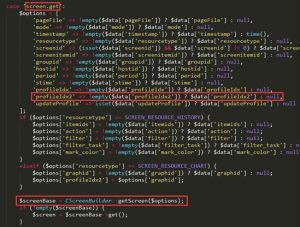
The first call chain is illustrated as follows, revealing the \zabbix-3.0.0beta2\frontends\php\jsrpc.php file.
When “method” is “screen.get”, the value of the profileIdx2 parameter is passed to “options”, which is then supplied to CScreenBuilder::getScreen(). The following shows contents of the \zabbix-3.0.0beta2\frontends\php\include\classes\screens\CScreenBuilder.php file.
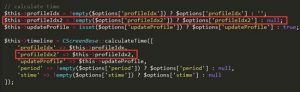
In this file, the profileIdx2 parameter is supplied to the CScreenBase::calculateTime() function. The following shows contents of the \zabbix-3.0.0beta2\frontends\php\include\classes\screens\CScreenBase.php file.
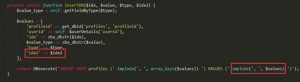
In this file, the profileIdx2 parameter is supplied to the CProfile::update() function. The following shows contents of the \zabbix-3.0.0beta2\frontends\php\include\classes\user\CProfile.php file.
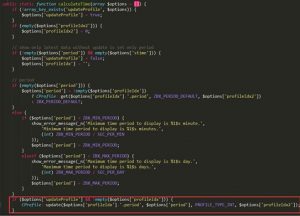
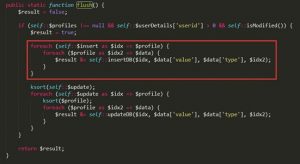
Here, profileIdx2 becomes idx2 as a part of “profile”, which is supplied to “insert”, thus adding idx2 to the insertDB() function.
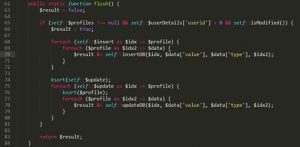
The following figure shows the handling procedure within insertDB.
Within insertDB, the zbx_dbstr() function sanitizes some key parameters, such as idx and value, but does not sanitize idx2, leading to an SQL injection vulnerability.
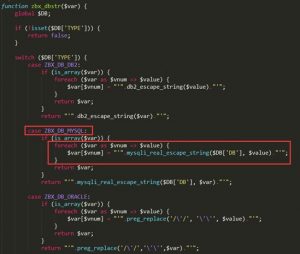
The analysis finds that the zbx_dbstr() function is located in zabbix-3.0.0beta2\zabbix-3.0.0beta2\frontends\php\include\db.inc.php.
From the preceding figure, we can find that zbx_dbstr() is a global sanitization function of Zabbix for sanitizing parameters to prevent SQL injection.
In the entire procedure, three parameters are added to the SQL statement: $options[‘profileIdx’], $options[‘period’], and $options[‘profileIdx2’]. However, $options[‘profileIdx2’] is directly added to the SQL statement without being sanitized.
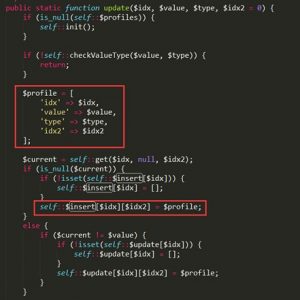
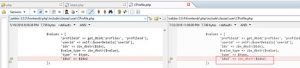
In the 3.0.4 version that fixes this vulnerability, the key parameter idx2 of the Cprofile::insertDB function is sanitized, as shown in the following figure.
Of course, to make the request finally reach this vulnerable function, attackers have to break certain constraints imposed by the Cprofile::flush function.
In the update() function, $profiles and $isModified() are set to “true”. To ensure userDeatails[‘suerid’] > 0, the user must log in or the guest mode must be enabled in the system.
Protection Solution
- For an affected version, upgrade to the latest version, which is available on the official website of Zabbix:
http://www.zabbix.com/download.php
- Disable guest accounts.
- Use the free detection service of NSFOCUS available at:
https://cloud.nsfocus.com/#/krosa/views/initcdr/productandservice?pid=0&sid=1
- Use the online detection service of NSFOCUS by logging in to NSFOCUS Cloud and applying for a trial use of the self-service scanning service:
https://cloud.nsfocus.com/#/krosa/views/initcdr/productandservice?pid=0&sid=0
- Use NSFOCUS’s remote assessment system (RSAS or WVSS) to evaluate intranet security.
- Use NSFOCUS’s detection product (IDS) to detect vulnerabilities.
- Use NSFOCUS’s protection product (IPS, NF, or SG) to protect against the exploitation of vulnerabilities.
- If you have purchased any of the preceding products or services of NSFOCUS, upgrade the product or service for effective detection and protection.
- Use NSFOCUS’s short-term service: NSFOCUS engineers handle the related event onsite to immediately eliminate risk points within the network and control the impact, and will provide an analysis report after the event.
- Use NSFOCUS’s mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services to eradicate risks and ensure that the event does not recur.
- Use NSFOCUS’s long-term service: NSFOCUS provides solutions specific to risks in the fund industry (threat intelligence + attack traceback + professional security service).
Reference Links
Statement
This security bulletin only describes possible security issues and NSFOCUS does not undertake any warranty or commitment on it. The user shall be liable for any direct and indirect consequences and losses caused by spreading or using information provided in this security bulletin and NSFOCUS and the author of this security bulletin will not undertake any liabilities for such consequences and losses. NSFOCUS reserves all the rights for revising and interpreting this security bulletin. If you want to reprint this security bulletin, you must ensure that it is reprinted in whole, including the copyright statement. Without NSFOCUS’s prior consent, no one can modify this security bulletin, add or delete any contents of it, or by any means use it for commercial purposes.